On February 9, 2022, amazing news appeared for the victims of Maze, Sekhmet and Egregor ransomware. The master decryption key was released by the developer of both malicious groups, which changed each other through time. About...
Egregor
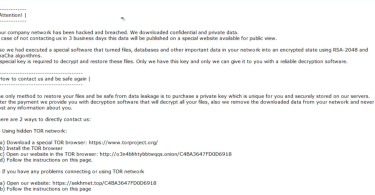
Egregor ransomware encrypts business users’ data with AES+RSA and then requires contact within 3 days for a Bitcoins ransom to get the files back. Distributers Egregor threatens to publish the stolen data in order to increase pressure on the victim. To do this, ransomware operators begin to steal data even before encrypting files. In some info, we know that Maze operators switched to Egregor.
Maze and Egregor ransomware operators earned more than $75 million in bitcoins
Analyst1 security researchers have calculated that the hackers behind the Maze and Egregor ransomware have already earned more than $75 million in ransoms from their victims. The company’s data is based on transactions that...


![What is the Win32:Evo-gen [Trj] virus?](https://howtofix.guide/wp-content/uploads/2019/11/trojan-ransom-145x100.jpg)

