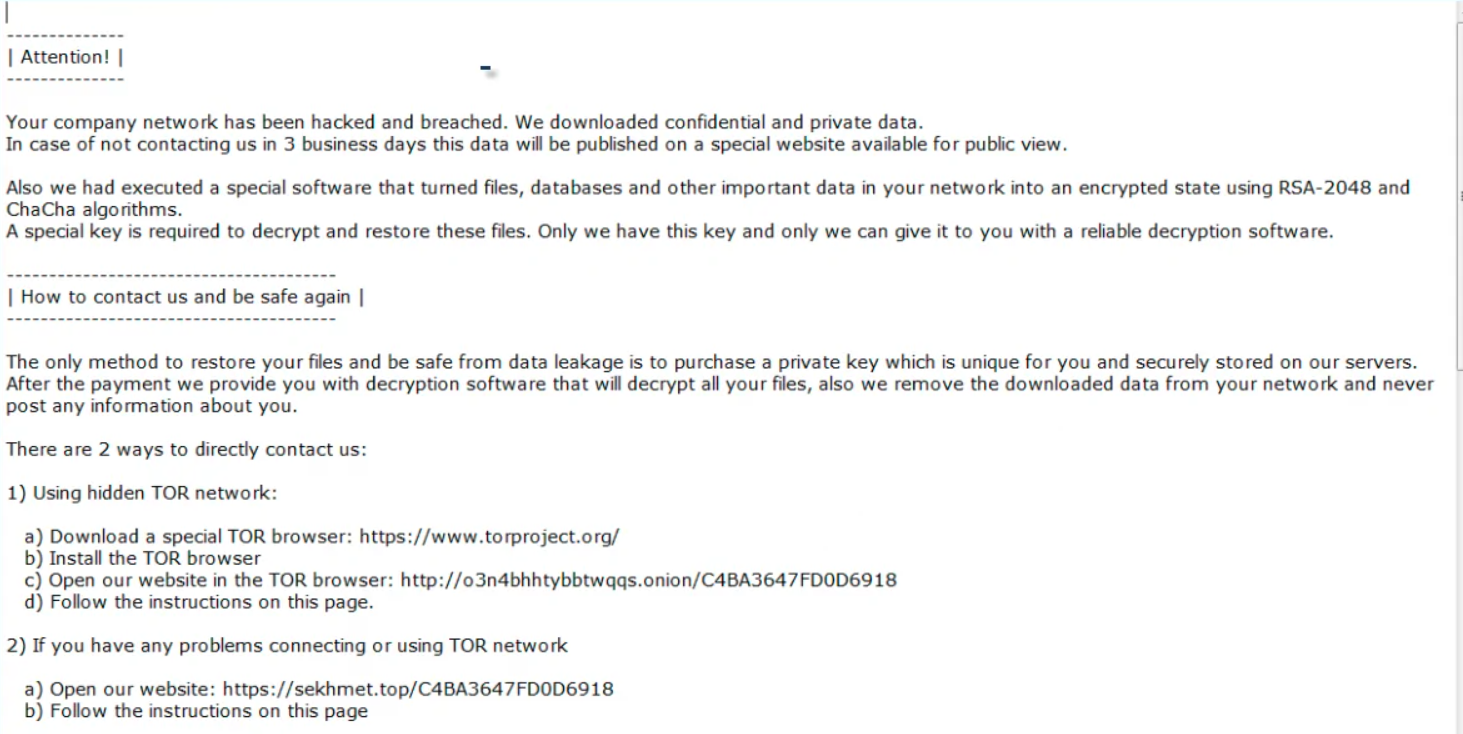
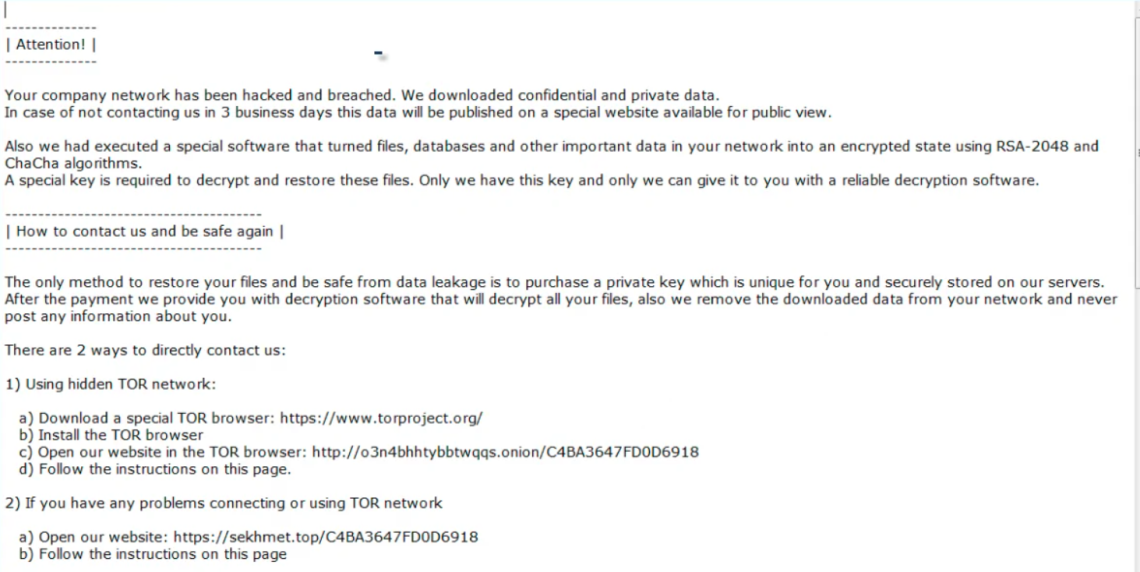
On February 9, 2022, amazing news appeared for the victims of Maze, Sekhmet and Egregor ransomware. The master decryption key was released by the developer of both malicious groups, which changed each other through time.
About Maze and Egregor ransomware
Maze ransomware appeared in 2019 and turned out to be a trendsetter in the ransomware world. While LockBit ransomware, which appeared around the same time, was standing on their honesty, Maze was boasting of high profitability. This ransomware group was the first who applied the double extortion technique – a usual thing for all other groups nowadays. Such a technique supposes not only file encryption, but also data stealing – and then the offer to pay separately for keeping the stolen information unpublished.
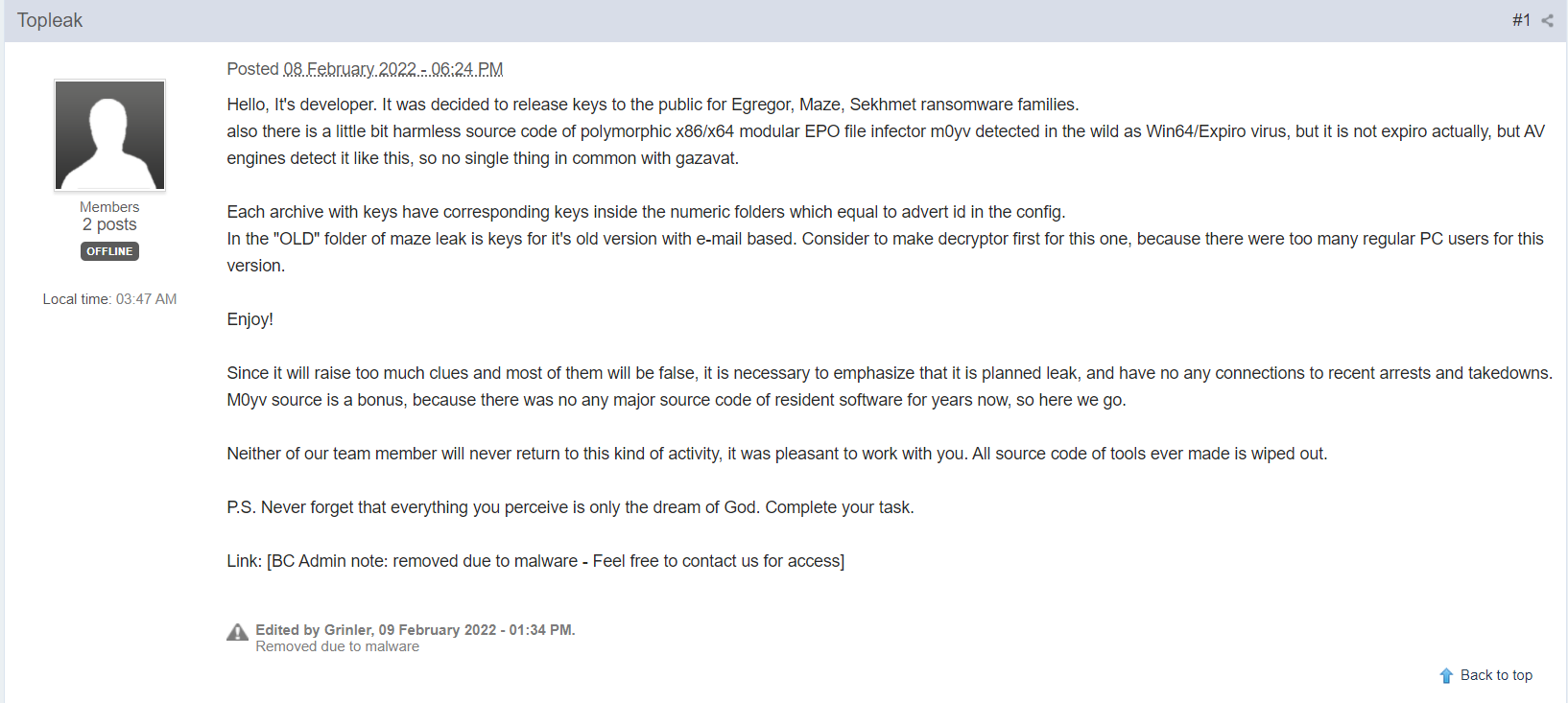
Topleak comment on the BleepingComputer forum
In September 2020, Maze claims about the shutdown and soon re-appears under the name of Egregor ransomware. The aforementioned Sekhmet ransomware was just a short-living fork of the original Maze group. It was active in spring 2020 and then ceased to exist. Egregor was not a long-living brand, too – after its members captured Ukraine in February 2021, this group has stopped its activity. So why did they decide to shut down after a year of agony?
Maze and Egregor decryption keys released by the developer
The person who introduced himself as a Maze and Egregor developer appeared on the BleepingComputer forum under the nickname of Topleak. That user claimed that he decided to leak the rest of the keys for the victims that did not pay the ransom. To clear out the situation, he/she also made a reference that this leak is planned, and is not related to recent ransomware developers’ captures.
Since it will raise too much clues and most of them will be false, it is necessary to emphasize that it is planned leak, and have no any connections to recent arrests and takedowns. M0yv source is a bonus, because there was no any major source code of resident software for years now, so here we go.
The person who represented itself as Maze developer also ensured that neither he nor his teammate will ever return to this sort of activity. Before the decryption keys for Maze and Egregor were published, they managed to wipe all source code of their malware. Seems they really want to cut all ropes with that business. Nonetheless, it is not clear why did they commit a shutdown. Possibly, they got enough money, like GandCrab group did in 2018. Less likely that they’re afraid that executive authorities will capture them, like it was with REvil group.
Maze and Egregor keys: what did they released
By the link you can see at the bottom of the screenshot, the downloading of the 7zip file will start. In that file, we found the following contents for Maze, Egregor, and Sekhmet decryption. As a bonus, the developers also added the source code of m0yv_infector – a specific module used by ransomware developers to commit attacks.
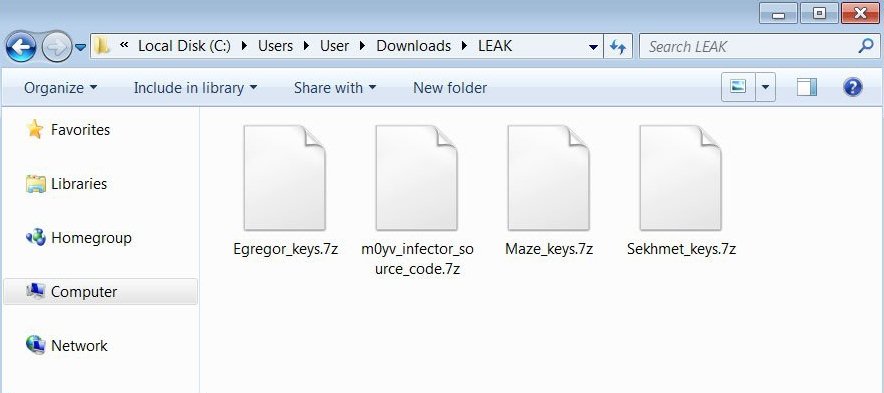
7zip archives contain 9 master keys for non-corporate victims of Maze ransomware and 30 master keys for corps. 19 master keys were released for Egregor and 1 – for Sekhmet. All ransomware examples of this group use RSA-2048 keys – undecryptable in the wild. In the .txt file, all of them look like this:
Checking the m0yv_infector
The peculiar “bonus” added by the ransomware developer is a part of ransomware payload. Exactly that thing was responsible for regulating the attack process. For sure, that is not the full source code of that element, but it is enough for software engineers to analyze and make conclusions. In particular, that piece of code may say a lot about the Maze ransomware mechanism.
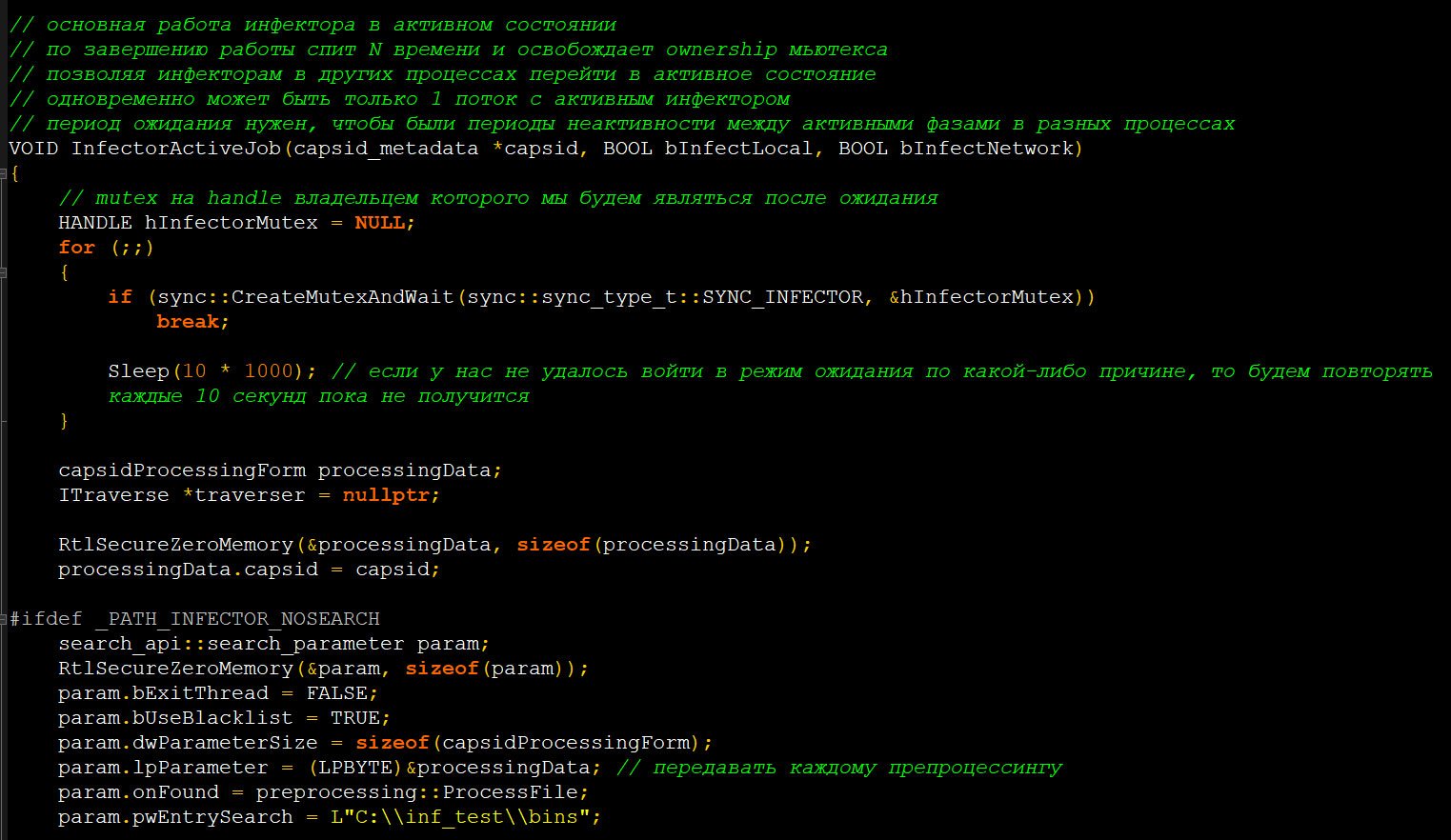
M0yv malware source code
User Review
( votes)