Orca Security analysts have discovered a critical vulnerability affecting Jupyter Notebook for Azure Cosmos DB. The problem that researchers dubbed CosMiss, allowed unauthorized access to containers for reading and writing, as well as an arbitrary code execution.
Let me remind you that we also talked about Emergency Patch Fixes Issues with Azure Active Directory and Microsoft 365 on ARM Devices, and also that Old bug in Azure leaked client source code.The vulnerability is related to Jupyter Notebook for Azure Cosmos DB, which integrates with Azure and Azure Cosmos DB accounts to make it easier to parse and visualize NoSQL data and query results.
When a user creates a new Notebook in Azure Cosmos DB, a new endpoint is created along with a new session or Notebook unique identifier (UUIDv4). The researchers examined the request traffic from the newly created Notebook to the server and noticed the presence of an Authorization Header. When they removed it and sent a request to list all the Notebooks on that server, it turned out that the server responded normally, since the Authorization Header was not required.
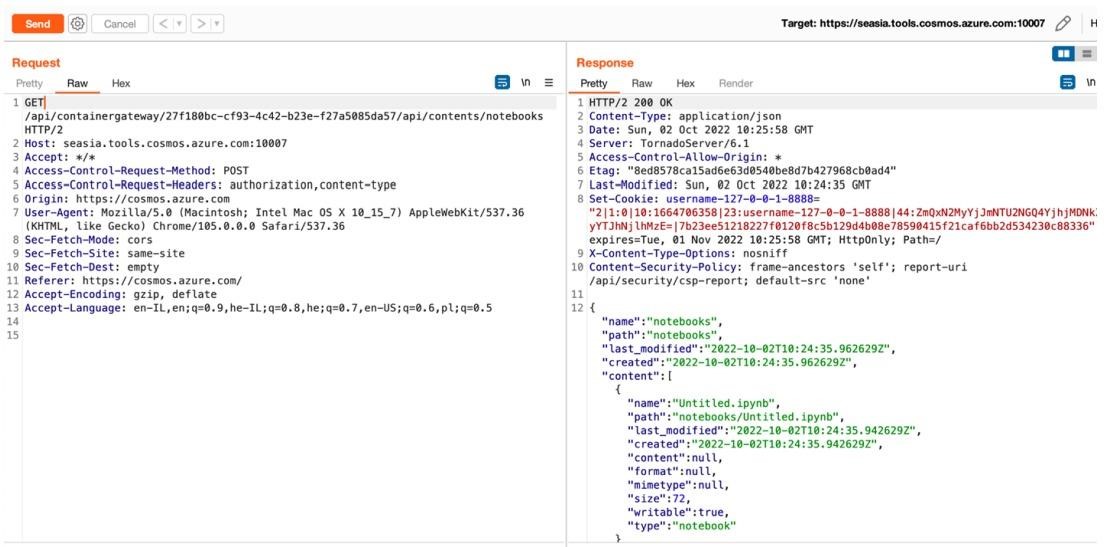
As a result, Orca Security analysts found that they could change the code in the Notebook, overwrite data, insert new fragments or delete them. In addition, it turned out that due to the disclosure of all Notebook identifiers within one platform, attackers can access and change any of them.
Ultimately, all of this at all could lead to remote code execution in the Notebook container by overwriting the Python file associated with Cosmos DB Explorer to create a reverse shell. However, for successful exploitation, the attacker must know the unique 128-bit identifier forwadingID and use it within an hour, since the field of this temporary Notebook is automatically deleted.
Microsoft fixed the vulnerability in early October. In its security bulletin, Microsoft notes that it found no evidence of exploitation of this issue and generally characterizes exploitation of the vulnerability as very difficult due to the randomness of the 128-bit forwadingID and its limited lifetime.
