Researchers have proven that popular video conferencing applications, including those used in corporate environments, continue to actively request the microphone, even after pressing the Mute button.
A study of the problem was published by a group of experts from the University of Wisconsin-Madison and Loyola University of Chicago.By the way, we also have articles about interesting research on cybersecurity, for example, we wrote that Researcher shows how to extract text from pixelated images.
In fact, the mute buttons provided in the applications themselves may not deactivate the microphone completely, as the operating system interfaces allow.
Experts are going to present a detailed report on this problem at the Privacy Enhancing Technologies Symposium event, which will be held in July 2022.
You might also be interested that Researcher finds that Twitter images can hide up to 3MB of data.
Returning back to the “mute” button, the researchers warn that some applications are constantly monitoring not only microphone input (even when the sound is muted), but also collect telemetry, which is then transmitted to their servers and can be used to pinpoint various types of background user activity.
According to analysts, the main problem is that video and audio signals are processed inconsistently. That is, on macOS and Windows, disabling the camera in an application is tied to an OS-level control that completely disables the camera and provides the user with clear visual confirmation that the camera is not active.
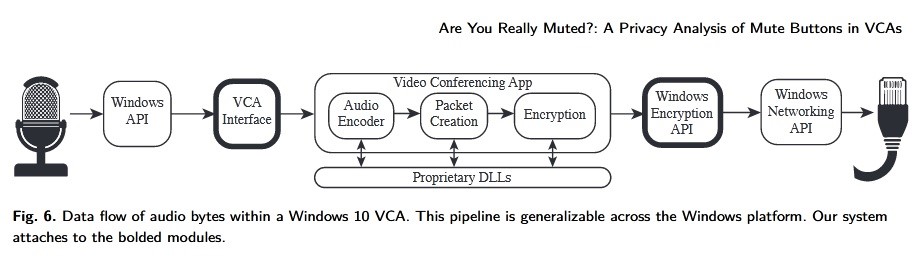
However, soft mute buttons are application specific and rarely have a visible indicator that the microphone is recording audio. In fact, mute buttons in apps don’t generally behave the way most people expect them to.
In general, the researchers studied popular video conferencing products such as BlueJeans, Cisco Webex, Discord, Google Meet, GoToMeeting, Jitsi Meet, Microsoft Teams/Skype, Slack, WhereBy, and Zoom (Enterprise). To prove that the sense of privacy experienced by conference participants when the microphone is muted is false, the experts used a PoC background activity classifier that allowed them to accurately recognize six types of background activity based on telemetry packets sent by applications when the microphone was muted.
Most of the products listed above have some sort of privacy issue, but mostly very limited or only theoretical. That is, all these applications had the ability to capture sound when the microphone is turned off, but most of them never used this ability.
The researchers explain that most native apps for Windows and macOS “can check if the user is talking even if the sound is muted, but they don’t continuously sample the sound in the same way as if the sound was on.”
However, when it comes to web applications, it uses the browser’s software mute feature to force the microphone driver to completely disable microphone data.
At the same time, scientists were unable to determine how the Microsoft Teams and Skype applications use microphone data when mute, because “they directly access the operating system” instead of using the standard Windows API.
It was also found that one of the applications still abused its capabilities and studied the audio signal, even when the microphone was turned off. It turned out that Cisco Webex sends network packets containing telemetry audio to their servers every minute, even if the microphone is muted.
The researchers emphasize that Webex is the only product that “continuously records data from the microphone when the user’s sound is muted” and transmits telemetry data to its servers every minute. So, the experts were able to intercept data in plain text format and use it for very accurate fingerprinting of background user actions.
Such telemetry is not the actual recorded sound, but a certain value obtained from the sound corresponding to the volume level of various background activities. This data was enough to recognize, with an accuracy of 82%, background activity in the room where the application was active: cooking, cleaning, typing, and so on.
The researchers say they notified Cisco of the issue back in January 2022 so the company could conduct its own investigation. As Cisco representatives have now told the media, the issue has since been resolved:
In January 2022, Webex stopped collecting troubleshooting audio settings data if users turned their audio off.the company said.
Webex customers are now encouraged to contact Cisco if they want to permanently eliminate this “snooping” that is required “for features that are active even when the user is muted, such as mute notifications and echo cancellation.”
