Experts warn that hackers have already begun to exploit the critical vulnerability CVE-2022-30525 that affects firewalls and Zyxel VPN devices.
Successful exploitation allows unauthenticated hackers to remotely inject arbitrary commands and implement reverse shells.By the way, let me remind you that we also wrote that Zyxel firewalls and VPN gateways contain a built-in backdoor, and also that New Mirai version attacks Zyxel devices.
The vulnerability that was patched last week and that allows remote command injection without authentication, received a CVSS score of 9.8 out of 10. In addition, even then it was already reported that it was easy to use by sending simple HTTP or HTTPS requests to vulnerable devices.
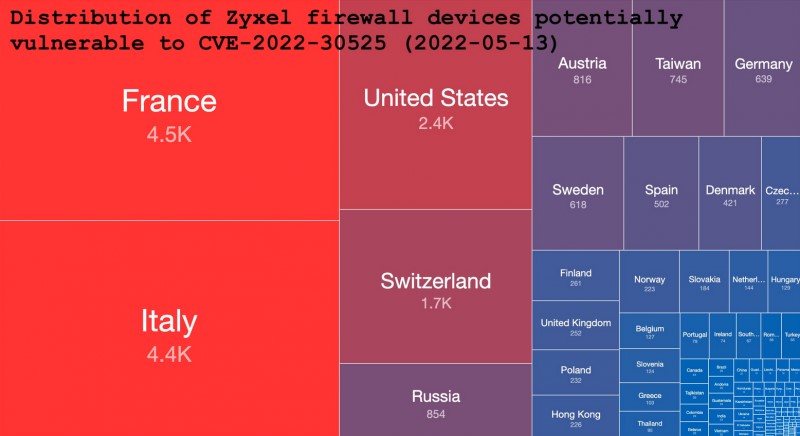
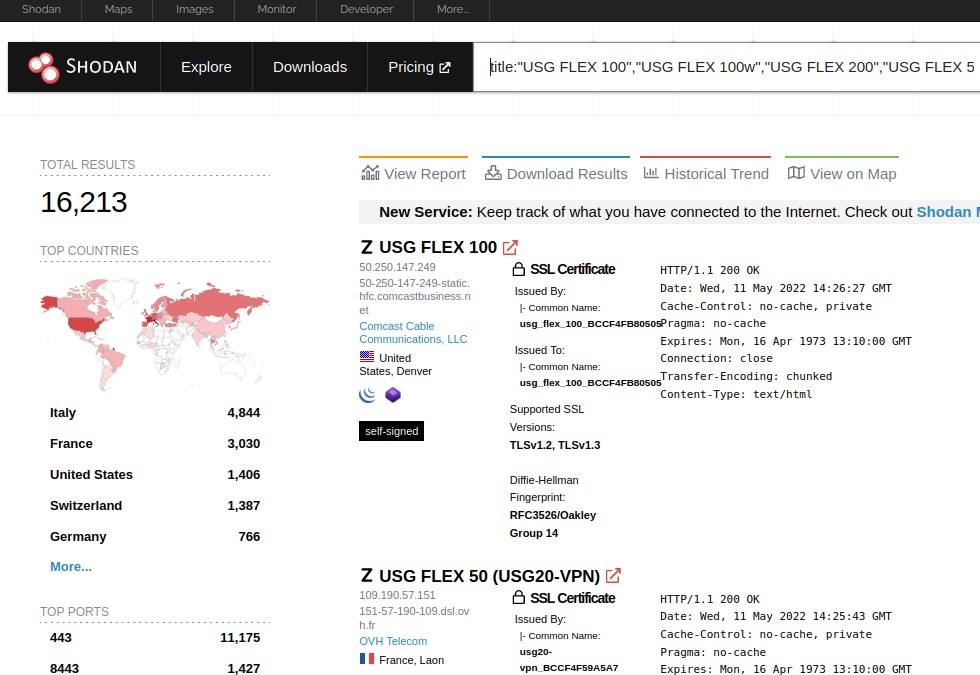
The issue affects a number of company firewalls that use the auto-provisioning feature. Such devices are used to establish VPN connections, SSL verification, web filtering, intrusion protection, email security, and so on. According to Shodan, over 16,000 potentially vulnerable devices can be found on the network.
The vulnerability was discovered back in April of this year by experts from Rapid7. In their report, they say that the bug could allow a remote and unauthenticated attacker to execute code as the nobody user. Thus, the vulnerability is exploited via the /ztp/cgi-bin/handler URI and is the result of an attacker passing unverified data to os.system in lib_wan_settings.py.
Experts explain that the consequences of such an attack can be modification of files and execution of commands, which will allow attackers to gain access to the network and then continue lateral advancement.
Interestingly, Rapid7 notified Zyxel about the issue last month, and the company quietly released patches on April 28, 2022, but did not publish the CVE identifier associated with the vulnerability, security advisories, or technical details of the problem. After Rapid7 has released its own detailed bug report, Zyxel has assured that there was some “misunderstanding during disclosure coordination.”
However, since the vulnerability poses a serious threat, even the director of cybersecurity at the NSA, Rob Joyce, warned of the need to urgently install updates.

Rob Joyce
As expected, soon the security specialists noticed the first attacks on CVE-2022-30525. Starting Friday, May 13, experts from the non-profit organization Shadowserver Foundation report that they have observed attempts to exploit the bug. It should be noted that it is not yet clear whether hackers are behind these attempts or whether it is information security researchers who seek to find vulnerable devices of Zyxel devices that are of interest to attackers.
Earlier, Rapid7 experts reported that about 16,000 potentially vulnerable devices could be found on the network, but now Shadowserver Foundation analysts have conducted their own scan and identified at least 20,800 Zyxel firewalls on the network that are potentially affected by the new vulnerability. The organization counted devices by unique IP addresses and reports that more than 15,000 of them are USG20-VPN and USG20W-VPN models.
Most vulnerable devices were found in the EU countries (including France and Italy).