Cyble and Bleeping Computer analysts have discovered more than 200 typesquatter domains that imitate the resources of 27 well-known brands. In this way, scammers try to force visitors to download various malware for Windows and Android.
Let me remind you that we also wrote that Malicious Packages from PyPi Arrange DDoS Attacks on Counter-Strike Servers.The researchers say that the domains used in this campaign are very similar to the real ones: usually only one letter is replaced or there is an additional letter “s”, which is easy enough to miss. In most cases, such malicious sites look like complete clones of the originals or look convincing enough that users do not suspect fraud.
Apparently, victims usually get to these resources by incorrectly typing the site address in the address bar of the browser, although journalists note that users can also get to the sites through links from phishing emails, as well as SMS, private messages on social networks, forums and etc.
Cyble, whose report focuses on the Android malware campaign, says the scammers are imitating popular Android app stores, including Google Play, APKCombo and APKPure, as well as download portals PayPal, VidMate, Snapchat and TikTok.
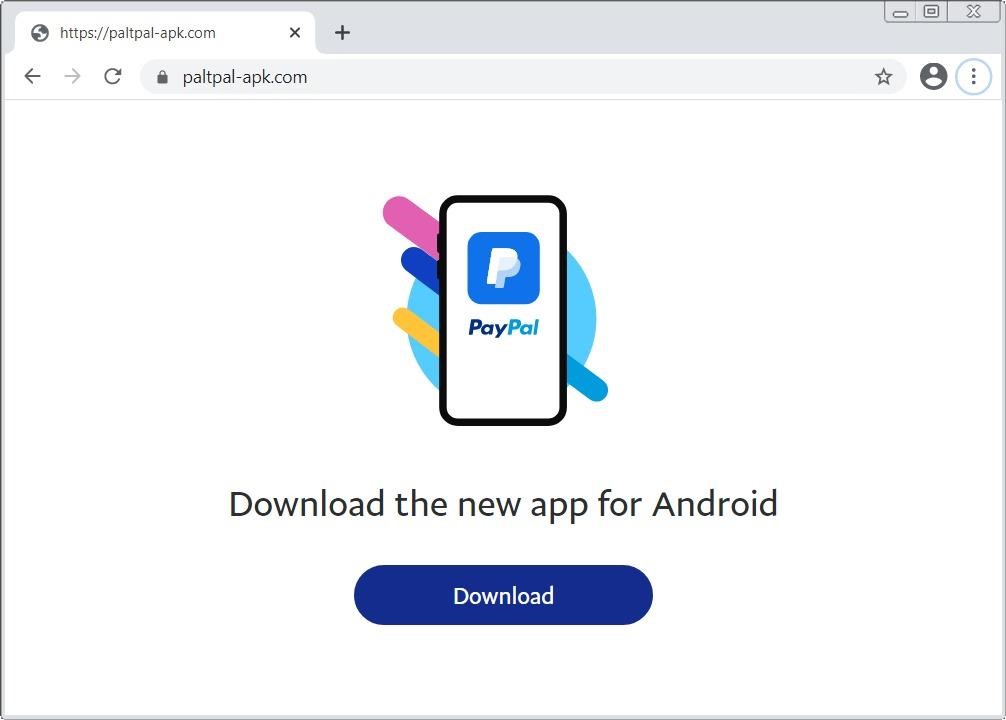
Some of the domains that attackers use:
- payce-google[.]com – pretends to be Google Wallet;
- snanpckat-apk[.]com impersonates Snapchat;
- vidmates-app[.]com – pretends to be VidMate;
- paltpal-apk[.]com – pretends to be PayPal;
- m-apkpures[.]com impersonates APKPure;
- tlktok-apk[.]link – Simulates the download portal of the TikTok app.
In all of these cases, the attackers are spreading the ERMAC banking trojan, first discovered in 2021 and currently targeting bank accounts and cryptocurrency wallets in 467 applications.
Bleeping Computer journalists write that they were able to uncover an even larger typesquatter campaign by the same operators, which is used to distribute Windows malware. This campaign involves over 90 sites that imitate the resources of more than 27 well-known brands. Here, visitors can be robbed of recovery keys for cryptocurrency wallets, as well as catch a malware for Android.
Mobile applications and services:
TikTok, Vidmate, SnapChat, Paypal, APK Pure, APKCombo, Google Wallet
Soft:
Microsoft Visual Studio, Brave Browser, ThunderBird, Notepad+, Tor Browser
Cryptocurrencies:
TronLink, MetaMask, Phantom, Cosmos Wallet, Mintable, Ethermine, GenoPets.
Exchange trading:
Trading View, IQ Option, NinjaTrader, Tiger.Trade
Sites:
Figma, Quatro Casinos, Big Time, CS:Money.
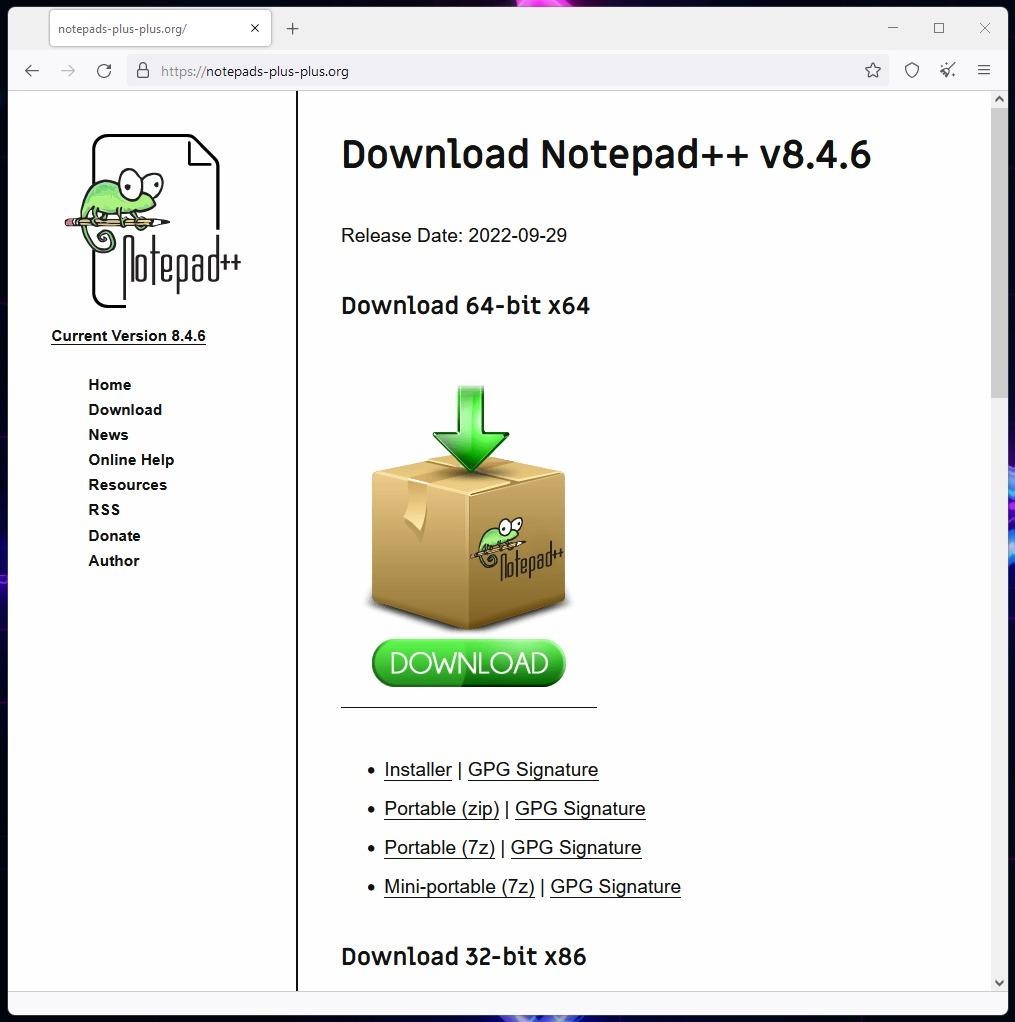
As an example, the publication cites the fake website of the popular text editor Notepad++. The fake site uses the notepads-plus-plus[.]org domain, which differs from the real notepad-plus-plus.org domain by only one character. The files from this site contain the Vidar infostealer, which has been deliberately increased to 700 MB to avoid detection.
Another site that Bleeping Computer discovered impersonates the Tor Project using the tocproject[.]com domain. In this case, the resource distributes the RAT and the Agent Tesla keylogger.
Among other examples:
- thundersbird[.]org: mimics Thunderbird, distributes Vidar infostealer;
- codevisualstudio[.]org: mimics Microsoft’s Visual Studio Code, distributes the Vidar infostealer;
- braves-browsers[.]org: mimics the Brave browser, distributes the Vidar infostealer.
Another cluster of scam sites target cryptocurrency wallets and victims’ seed phrases. For example, ethersmine[.]com, which immediately tries to steal the seed phrase from the visitor’s Ethereum wallet. Other sites from this group also attack cryptocurrency holders and investors, and masquerade as popular crypto wallet sites, trading applications and NFT sites.
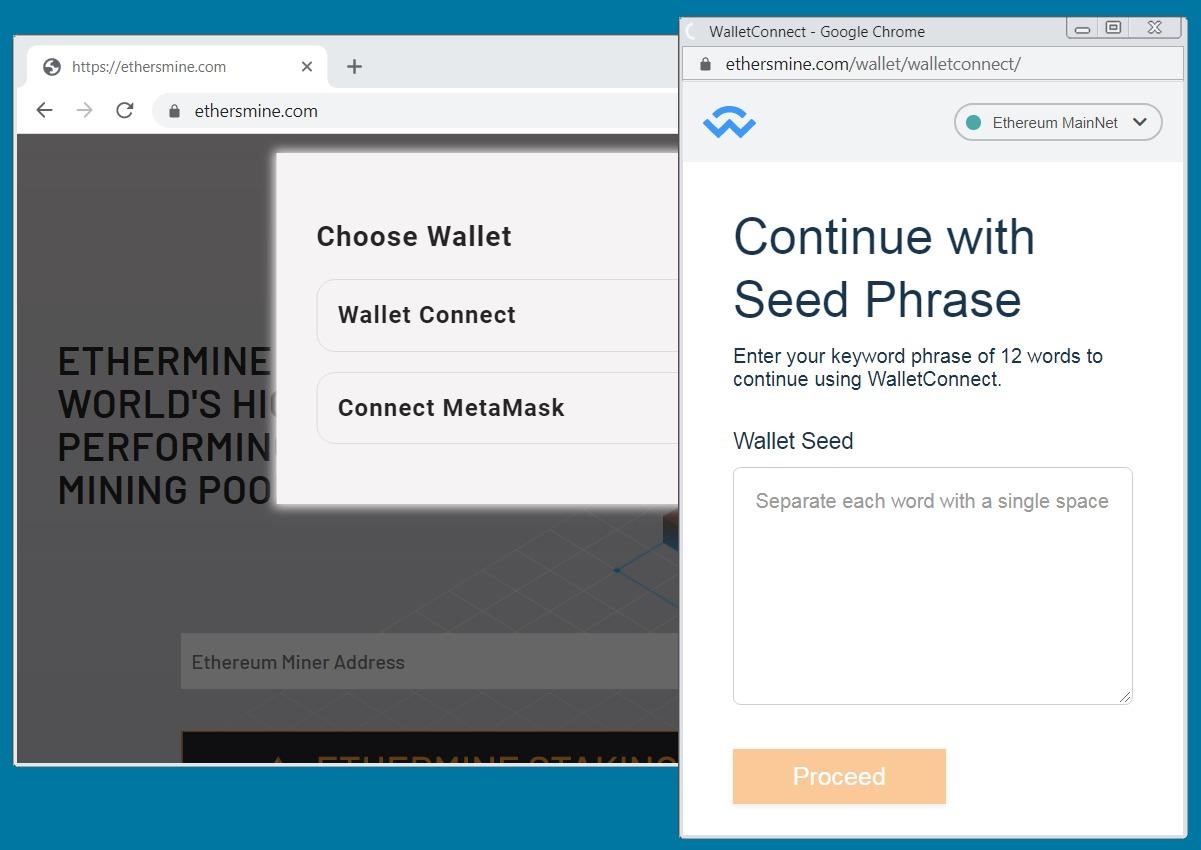
It is noted that the attackers use several address options for each domain to cover more possible typos, so the domains discovered by the researchers are most likely only a small part of this campaign.
