Security firm CloudSEK has identified 3,207 mobile apps that expose Twitter API keys to the public, allowing attackers to take over Twitter user accounts associated with those apps.
By the way, we also wrote that Apps that spread AlienBot and MRAT malware found on Google Play, and also that Attackers Hack into Accounts Posing as Verified Twitter Accounts.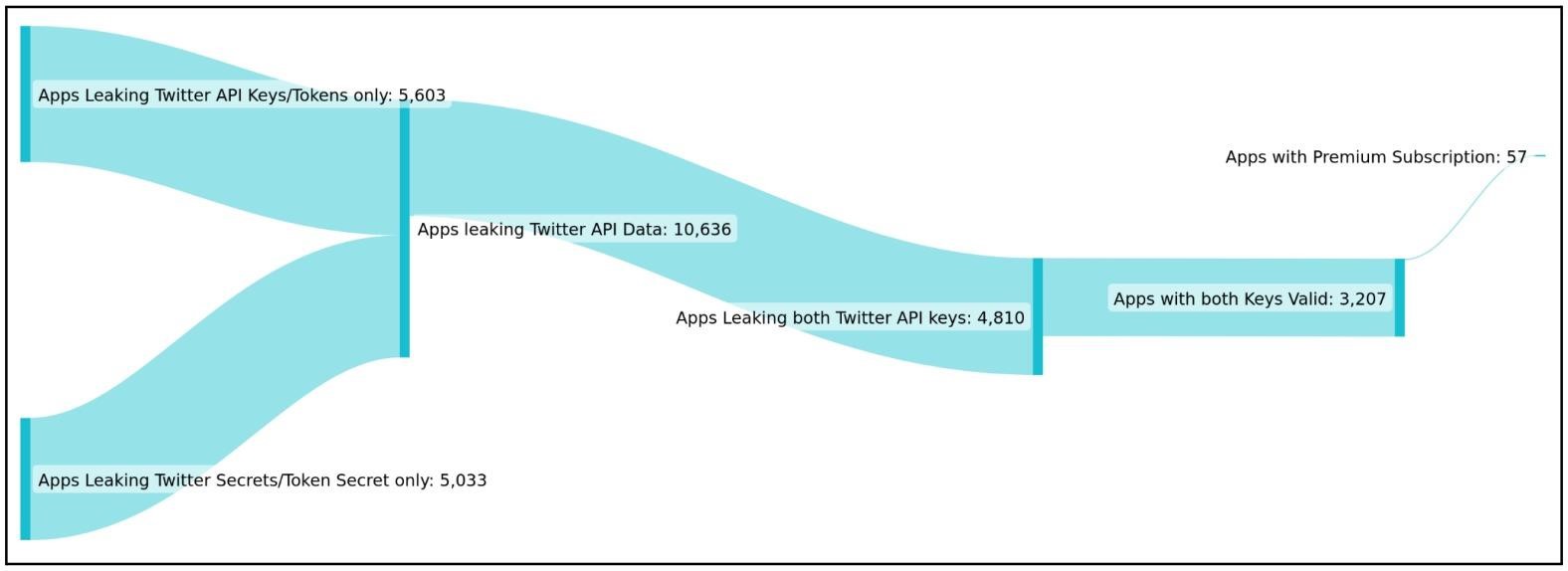
CloudSEK analysts targeted large numbers of applications looking for potential data breaches and as a result discovered thousands of valid Consumer Keys and Consumer Secrets for the Twitter API.
The fact is that when integrating mobile applications with Twitter, developers are provided with special authentication keys or tokens that allow their applications to interact with the Twitter API. When a user links their Twitter account to such a mobile app, the keys give the app the ability to act on the user’s behalf, such as logging in with Twitter, tweeting, sending private messages, and so on. For this reason, it is strongly discouraged to store the keys directly in the application, where outsiders can get to them.
CloudSEK explains that leaked API keys are usually the result of a mistake or oversight by developers who forget to delete them before a product is released. In these cases, the credentials are usually stored in the following locations:
- resources/res/values/strings.xml
- source/resources/res/values-es-rAR/strings.xml
- source/resources/res/values-es-rCO/strings.xml
- source/sources/com/app-name/BuildConfig.java
One of the most obvious abuse scenarios for such keys is the creation of an army of verified accounts on Twitter with large followings to promote fake news and malware campaigns, cryptocurrency scams, and so on.
The Bleeping Computer, with which analysts shared a list of problematic applications, reports that these applications have between 50,000 and 5,000,000 downloads and are related to urban transport, reading books, newspapers, electronic banking, GPS bike trackers and so on.
Unfortunately, most of the developers who leaked API keys did not contact CloudSEK even a month after receiving the warnings, and in most applications the problems were not fixed. For this reason, researchers and journalists do not disclose the names of vulnerable products, because they can still be used to take over other people’s Twitter accounts.
