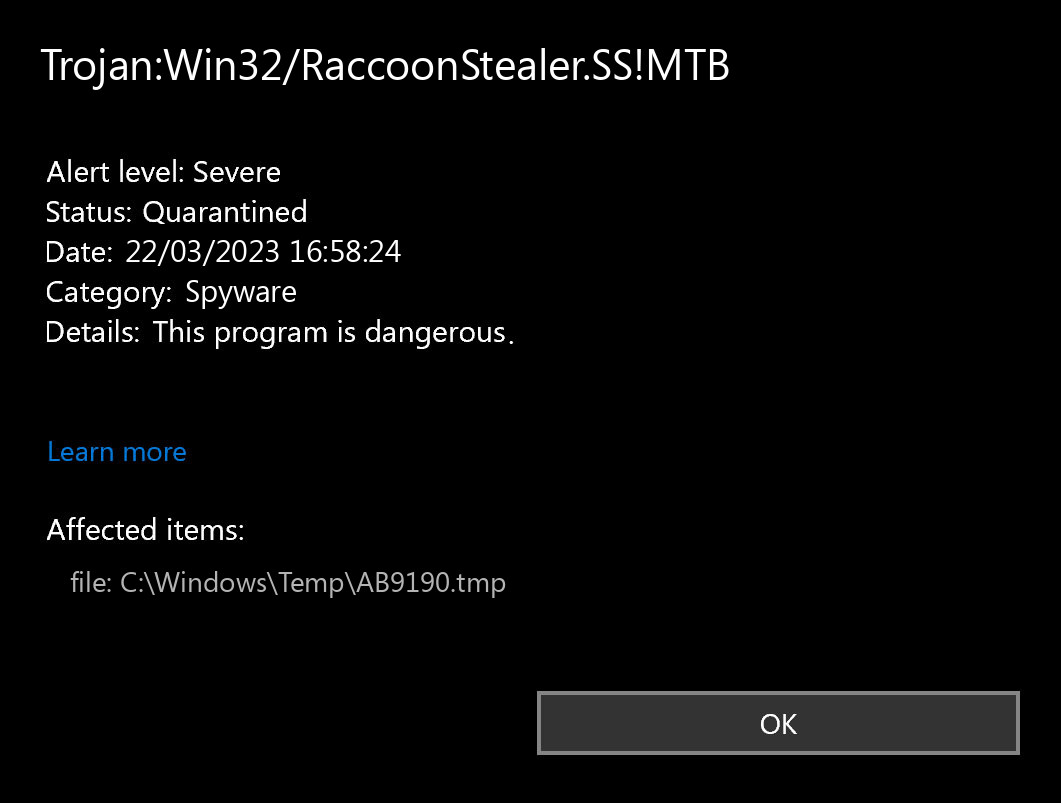
If you spectate the notification of Trojan:Win32/RaccoonStealer.SS!MTB detection, it looks like that your PC has a problem. All viruses are dangerous, with no exceptions. Raccoon is malware that targets on grabbing different categories of data from your system. It applies a lot of hacks to evade security software detection, and uses secured connections to send data to the command server. The activity of this malware commonly results in losing access to your accounts, and exposing your identity. Moreover, certain samples can also deliver other malicious programs to the system.
Any type of malware exists with the only target – make money on you1. And the developers of these things are not thinking of morality – they use all available ways. Taking your personal data, receiving the payments for the promotions you watch for them, exploiting your hardware to mine cryptocurrencies – that is not the complete list of what they do. Do you want to be a riding equine? That is a rhetorical question.
What does the pop-up with Trojan:Win32/RaccoonStealer.SS!MTB detection mean?
The Trojan:Win32/RaccoonStealer.SS!MTB detection you can see in the lower right side is displayed to you by Microsoft Defender. That anti-malware software is quite OK at scanning, but prone to be generally unstable. It is unprotected to malware attacks, it has a glitchy user interface and problematic malware removal capabilities. For this reason, the pop-up which states about the Raccoon is just a notification that Defender has actually found it. To remove it, you will likely need to use a separate anti-malware program.
Having Trojan:Win32/RaccoonStealer.SS!MTB malware on your computer is not a pleasant thing from any perspective. The worst problem is that you will not discover anything wrong. Key feature of any spyware is being as secretive as possible. Some Raccoon samples are also able to perform self-deletion after grabbing all the valuables available on the PC. After that, it will be nearly impossible to recover the flow of events and understand how your accounts were hacked. Variants of spyware that aim at long-term action can target the specific folder in the system or file type. Then, files grabbed in that way will be put for sale on the Darknet – at one of its numerous marketplaces with stolen data.
Spyware Summary:
| Name | Raccoon Spyware |
| Detection | Trojan:Win32/RaccoonStealer.SS!MTB |
| Damage | Steal personal data contained in the attacked system. |
| Similar | Trojan:Win32/Raccoon.RA!MTB, Trojan:Win32/Raccoon.N!MTB |
| Fix Tool | See If Your System Has Been Affected by Raccoon Spyware |
Raccoon Stealer Technical Description
Malware Behaviour
Alternative detection names
Is Trojan:Win32/RaccoonStealer.SS!MTB dangerous?
As I said before, any malware is harmful. And Trojan:Win32/RaccoonStealer.SS!MTB is not even near of distracting you rather than harming. The most misleading quality of this malware is the fact you cannot witness its activity by any means, other than with anti-malware software scanning. And when you are in the dark, hackers who successfully delivered their malware to your computer are starting to count the money. Darknet forums offer a lot of opportunities to sell malware logs for a hefty sum – especially when these logs are newly-collected. And it is a bad idea to imagine what will happen to your accounts when other cybercriminals will put their hands on your credentials.
However, situation may have much faster turnover. In some situations, hackers are delivering their virus precisely to the person they are attempting to rob. Spyware is invaluable when it comes to grabbing login credentials, and some samples target precisely at banking accounts or cryprocurrency wallets. One may say, giving spyware a run is the same as sending all your money to fraudsters.
How did I get this virus?
It is not easy to trace the origins of malware on your PC. Nowadays, things are mixed, and distribution tactics chosen by adware 5 years ago can be utilized by spyware these days. However, if we abstract from the exact spreading tactic and will think about why it works, the answer will be very basic – low level of cybersecurity awareness. Individuals click on ads on strange sites, click the pop-ups they receive in their web browsers, call the “Microsoft tech support” thinking that the odd banner that states about malware is true. It is necessary to recognize what is legitimate – to avoid misconceptions when attempting to determine a virus.
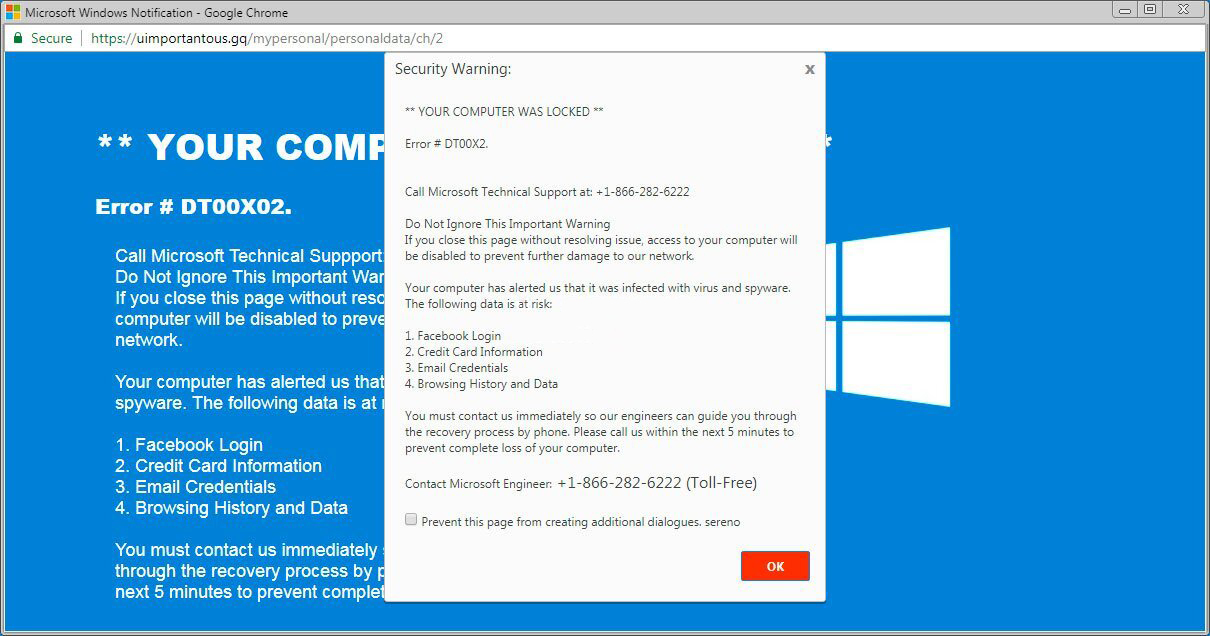
The example of Microsoft Tech support scam banner
Nowadays, there are two of the most extensive ways of malware spreading – bait e-mails and also injection into a hacked program. While the first one is not so easy to stay away from – you should know a lot to recognize a fake – the second one is easy to address: just don’t utilize hacked apps. Torrent-trackers and other sources of “totally free” applications (which are, in fact, paid, but with a disabled license checking) are just a giveaway point of malware. And Trojan:Win32/RaccoonStealer.SS!MTB is simply one of them.
How to remove the Trojan:Win32/RaccoonStealer.SS!MTB from my PC?
Trojan:Win32/RaccoonStealer.SS!MTB malware is extremely hard to eliminate by hand. It places its data in a variety of locations throughout the disk, and can restore itself from one of the elements. Furthermore, countless alterations in the windows registry, networking settings and also Group Policies are really hard to find and return to the initial. It is much better to utilize a special tool – exactly, an anti-malware app. GridinSoft Anti-Malware will fit the best for virus elimination objectives.
Why GridinSoft Anti-Malware? It is very lightweight and has its detection databases updated almost every hour. Furthermore, it does not have such bugs and vulnerabilities as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for getting rid of malware of any type.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Raccoon the default option is “Delete”. Press “Apply” to finish the malware removal.



User Review
( votes)References
- Read about malware types on GridinSoft Threat encyclopedia.