While the information security community around the world is discussing the elimination of Emotet, the law enforcement agencies of Bulgaria and the United States carried out another important operation: they disrupted the operation of the NetWalker infrastructure, one of the most active ransomwares of 2020.
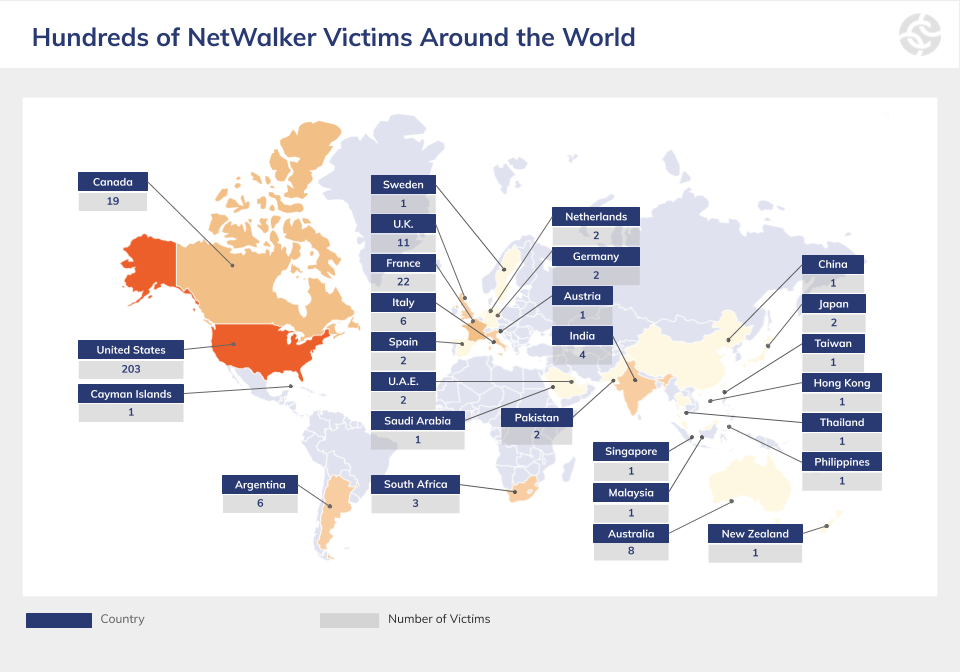
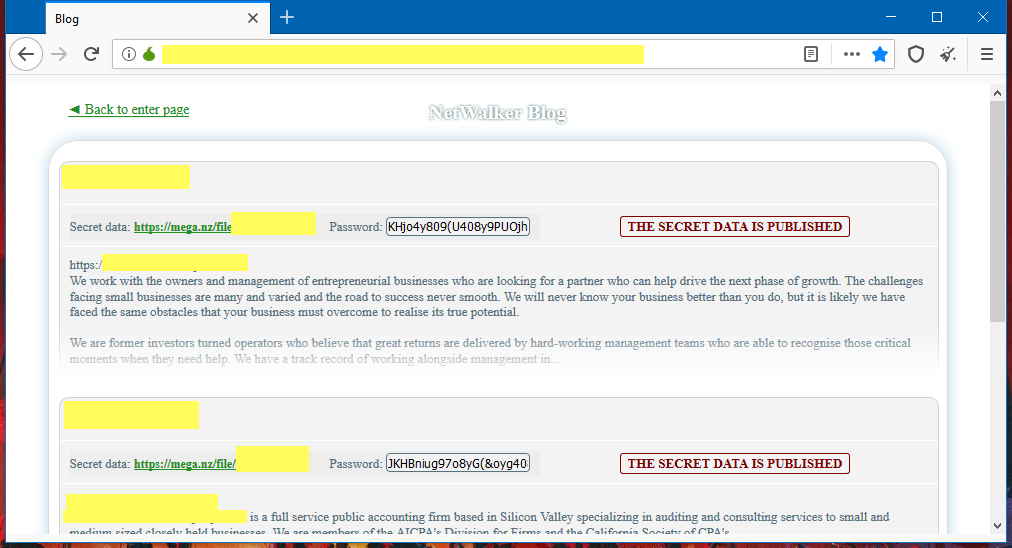
According to the US Department of Justice, at least 305 victims from 27 countries, including 203 victims in the United States, suffered from NetWalker activity. It is reported that the Bulgarian police seized a server that hosted the darknet portals of NetWalker operators, and law enforcement officers in the United States, meanwhile, indicted a Canadian citizen who gained at least $27.6 million by infecting the networks of various companies with this ransomware.It is known that the server seized by the authorities hosted special pages, where NetWalker redirected victims of its attacks so that they could contact the attackers and negotiate the ransom payment. It also hosted hackers’ blog, where they published data stolen from companies if they refused to pay. Infographics: Chainalysis
Little is known about the detained citizen of Canada, Sebastien Vachon-Desjardins, who was arrested in the US.Apparently, he was one of the NetWalker clients, that is, he rented an encryptor from the developers and used it for its own intended purposes, since NetWalker operates on a ransomware-as-a-Service (RaaS) scheme.
Incidentally, last year McAfee analysts estimated the revenues of NetWalker operators at $25 million. Now, Chainalysis experts report that cybercriminals “earned” about $46 million in 2020, and NetWalker has become one of the five most profitable ransomwares of last year, along with Ryuk, Maze, Doppelpaymer and Sodinokibi.
The Chainalysis experts also believe that the aforementioned Canadian citizen was not only associated with the NetWalker authors, but also worked with other ransomware hack groups, including the Sodinokibi, Suncrypt and RagnarLocker developers.
Let me remind you that recently the cyber police of Ukraine exposed a transnational hacker group that were distributing Emotet, one of the most dangerous current malwares.