Google Project Zero expert Samuel Groß discovered that with the release of iOS 14, Apple’s operating system has a new security system – the BlastDoor sandbox, designed to process iMessages data.
Gross says that BlastDoor is a basic sandbox where code can be executed separately from the rest of the OS. Although iOS already has a number of sandbox mechanisms, BlastDoor is an innovation that only works at the iMessage level.Basically, BlastDoor’s job is to accept incoming messages, as well as unpack and process their content in a safe and isolated environment, where malicious code hidden inside the message cannot harm the operating system or reach user data.
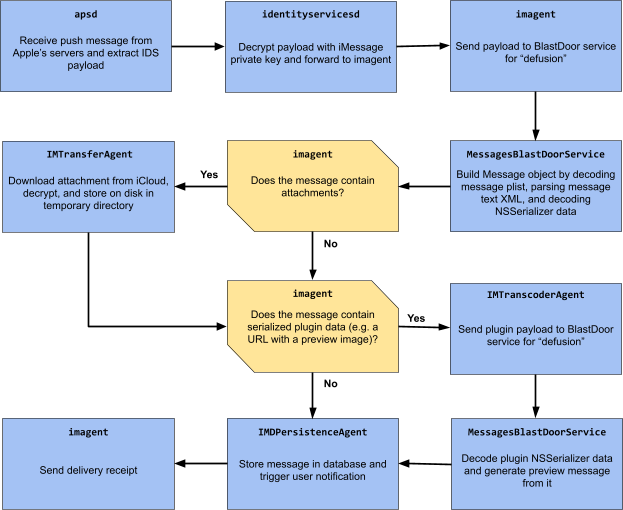
Apparently, the need for BlastDoor arose due to the fact that in recent years security experts have repeatedly discovered that iMessage cannot cope with cleaning incoming user data.
For example, at the end of 2020, Citizen Lab specialists spoke about hacker attacks on employees of the Al-Jazeera TV company. These attacks were carried out through a 0-day vulnerability in iOS, and the bug stopped working after the release of iOS 14.
This fact interested Gross, who decided to look for new protective mechanisms in the updated version of iOS, which made the exploits of cybercriminals suddenly useless.
Let me remind you that we also wrote that hacker can get in an iPhone by simply sending a text message.

