JetBrains recently discovered a critical authentication bypass vulnerability in TeamCity On-Premises servers. This flaw could allow attackers to execute remote code without user interaction, gaining admin privileges on affected servers.
The Critical Security Vulnerability Affecting TeamCity
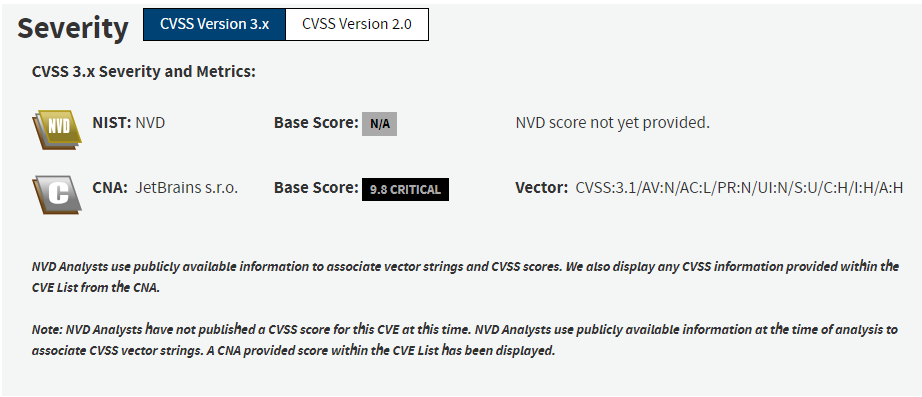
A critical security vulnerability has been detected in JetBrains’ TeamCity On-Premises software. The flaw coded as CVE-2024-23917 could allow an attacker to take control of a vulnerable TeamCity server without authentication and execute any desired commands. According to the JetBrains’ claim, an external security researcher reported the issue on January 19, 2024.
Description of the TeamCity vulnerability from NVD NIST website
Although JetBrains has not disclosed the technical details of the flaw, they have thanked the researcher who reported it. JetBrains has stated it will soon release more information about the flaw. This will include recommendations on how to check if a TeamCity server has been compromised.
More About CVE-2024-23917
The flaw, tracked as CVE-2024-23917, is an authentication bypass vulnerability. It affects the HTTP(S) protocol used by TeamCity On-Premises. According to JetBrains, the flaw may enable an attacker with HTTP(S) access to a TeamCity server to bypass authentication checks and gain administrative control of that server. This could result in data theft, malware infection, ransomware attacks, or other malicious activities.
The vulnerability impacts all versions of TeamCity On-Premises, ranging from 2017.1 to 2023.11.2. JetBrains has revealed that over 30,000 organizations globally employ the TeamCity software building and testing platform.
JetBrains Response
Company has released a fixed version, 2023.11.3, and strongly advises all users to update their servers as soon as possible. For those who are unable to update, JetBrains has also provided a security patch plugin that can be installed on TeamCity versions 2017.1 through 2023.11.2. The plugin will patch the vulnerability and prevent unauthorized access.
JetBrains has also confirmed that TeamCity Cloud servers, which are hosted and managed by JetBrains, have already been patched and were not attacked by the flaw. So, TeamCity Cloud users do not need to take any action.
As I have mentioned, the details on how exactly the flaw works are not published at the moment – an excellent move, if you ask me. Nonetheless, statistics show that the vast majority of exploitation cases happen after all the info on the vulnerability is published. For instance, the past flaw in TeamCity was discovered back in May 2023, and its massive exploitation happened only in December of the same year.
