The hack group El_Cometa, formerly known as SynAck, released keys to decrypt data that had suffered from attacks by their ransomware between July 2017 and early 2021.
The keys were provided to The Record by a man who introduced himself as a former member of the group SynAck.The authenticity of the keys has already been confirmed by the well-known information security expert Michael Gillespie, an employee of Emsisoft and the creator of the ID-Ransomware service.
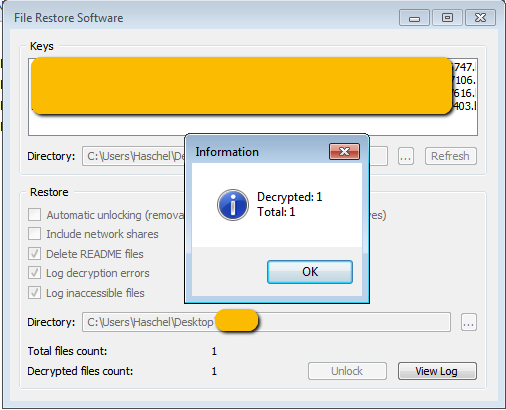
The specialist successfully used the provided data decryption utility and private keys to recover files damaged by old SynAck attacks.
Journalists decided not to publish the keys themselves, as “the decryption process can be somewhat difficult for untrained users,” and former SynAck victims may end up damaging their files even more.
Instead, Emsisoft will create its own data rescue tool that is safe and easy to use. The company promises to release this utility within the next few days.
The hack group SynAck, first discovered by experts back in July 2017, is one of the oldest ransomware groups to date.
Hackers explain simply their decision to leak the old master keys for decrypting files: last month they stopped working on SynAck and focused on a new malware called El_Cometa.
In addition, the group said that while they previously worked with only two external “partners” to distribute SynAck, they now plan to significantly improve their operating model.
This will be done by launching a new Ransomware-as-a-Service (RaaS) platform through which they plan to attract more partners (also known as “affiliates”) to launch attacks and infect victims with the new El_Cometa strain.
Let me remind you that Universal decryption key of REvil appeared on the Russian-language hacker forum.