Norton Labs researchers say that 8 out of 10 search-powered sites leak all their users’ search queries to third parties, most often to companies involved in online advertising.
Let me remind you that we also wrote that Hackers Attacked Website of the Ministry in Russia, and Rostelecom Leaked Employee Data, and also that Air India reports data leak of 4.5 million passengers.To study a million sites, experts have created a special crawler that can bypass the so-called “interstitials” and other obstacles that require human interaction during browsing. This scanner went to sites, found a search bar, searched for the word “JELLYBEANS” with it, and then collected all subsequent network traffic for analysis.
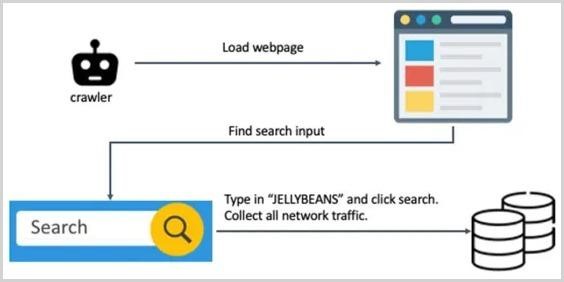
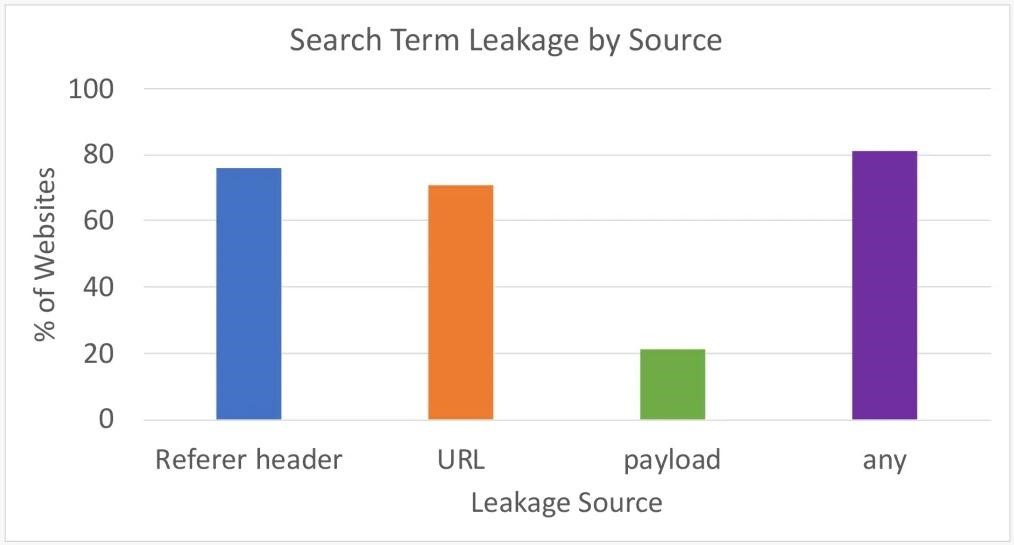
The team’s idea was to scrutinize each HTTP request to see if “JELLYBEANS” appears somewhere among the requests submitted to third party partners. It turned out that exactly this took place in 81.3% of cases.
Thus, network requests include a URL, a referer header of the request, and a payload that typically contains the browser’s “profile” and visit data. The analysis showed that the majority of leaks occur through the referer header (75.8%) and URL (71%), and the payload contained the word “JELLYBEANS” in 21.2% of the cases studied.
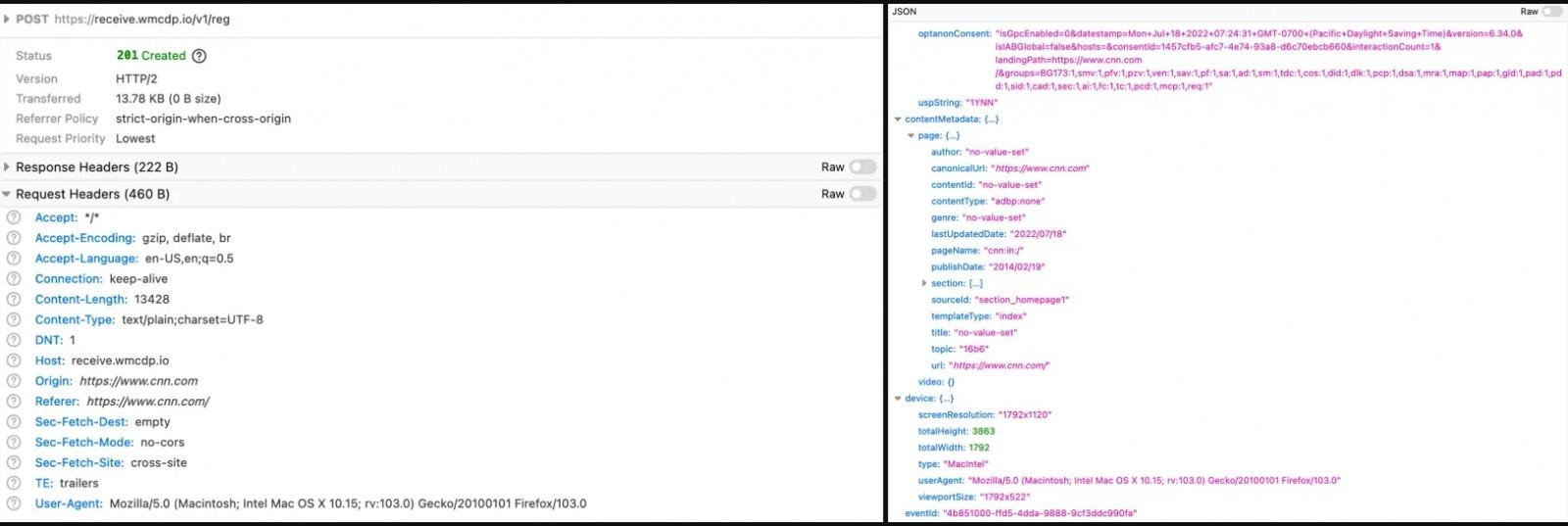
A total of 81.3% of the sites transmitted information to advertisers in at least one of the three ways listed. At the same time, Norton Labs believes that the actual percentage of leaks of search queries is likely even higher. The fact is that many payloads in HTTP requests are obfuscated, so the analysis could not find “JELLYBEANS” among the data, although the test search query could be there.
Interestingly, at the same time, only 13% of the sites at least somehow mentioned “search terms” in their privacy policies, and 75% of the resources got off with general statements about the possible “exchange of information about users with third parties.”
