On October 17, 2021, one of the REvil group administrators made a shocking claim on a Darknet forum. The REvil group got their servers compromised and decided to go offline for a while, and then stated that they will never go back online.
What’s happened to the REvil ransomware group?
On Saturday, October 17, the REvil group member (0_neday) started a topic on a Darknet forum. The exact forum is dedicated to cybersecurity, hacking and various other semi-legal things. He claimed that their domain server had been hijacked. Earlier, one of their main actors (under the nick “UNKNWN”) suddenly disappeared, and they thought he was dead, giving no attention to what happened. In September, after several months of the group inactivity, 0_neday introduced himself as a REvil member. He said that he backed REvil alive after several months of inactivity using the backups.
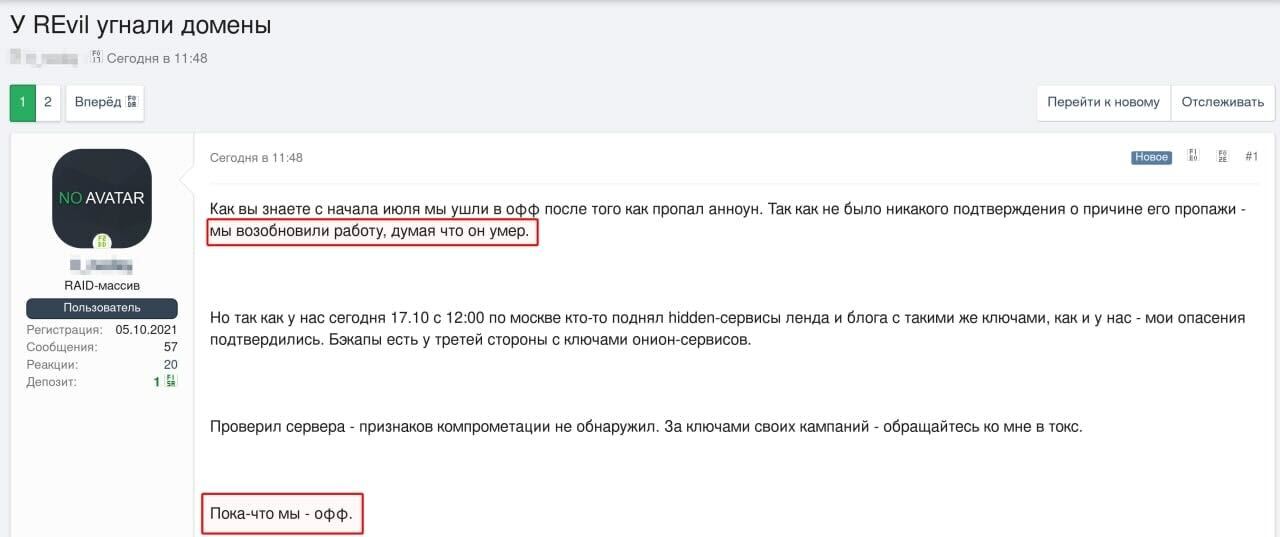
This person has likely ignored the rumors that the FBI did a great success in their investigation against the REvil group. To the moment when 0_neday decided to launch their network from the backups, the FBI have already compromised these backups. Hence, after the federals got an approval that they have really valid backups, they just did an interesting gesture – suddenly launched their own alteration of the landing page and blog of the REvil group. 0_neday says that he understood that their services were compromised after seeing this. However, he cannot find any leftovers in logs or something like that – hence, the third party who did this used a legit and normal access way (i.e. regular login into the system).
How could it happen?
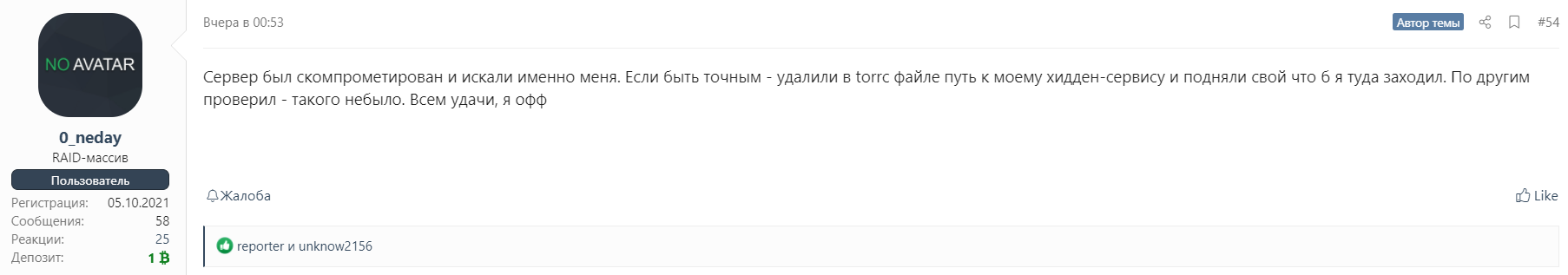
Assuming all background information, a lot of cybersecurity experts supposed that UNKNWN disappearance is somehow related to the following events. This person could be captured by the FBI, and then he/she gave up all the credentials from REvil system. Nonetheless, REvil administrator (nickname “REvil”) ensures that all compromised elements of their system were deleted exactly after the UNKNWN have vanished.
What is the real matter of this incident? No one – even REvil administrators – don’t know. Possibly, the network compromise is the result of operator capturing, which happened at the edge of September 2021. Europol and Ukrainian Cyber Police, together with the FBI and several other executive authorities, captured the REvil ransomware operator. Possibly, he gave up information during the interrogation. This guy can barely be the disappeared UNKNWN, since he was conducting his activity up to the moment when police were at his door, while the aforementioned member was offline since June 2021.
Aftermath of REvil group
It seems that their network was compromised by multiple reasons – FBI actions and mistakes of REvil members. After the comeback, they have likely lost their fortune as well as skilled operators. The incident they have during the Kaseya attack says a lot about a bad organization in the “reborned” REvil.
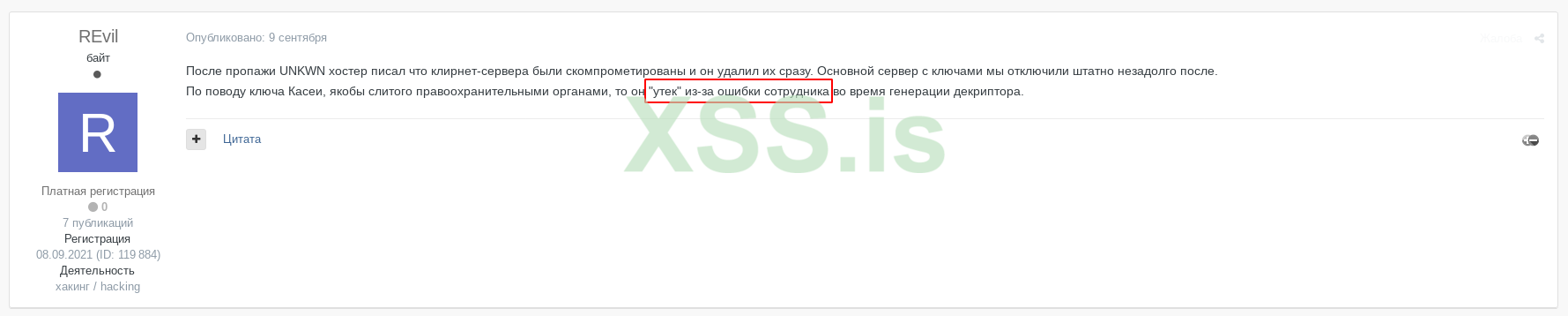
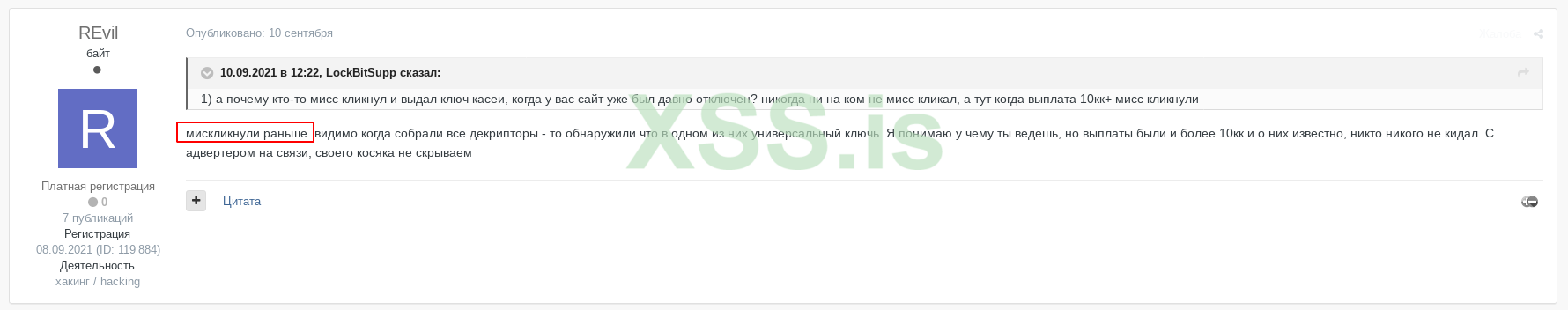
On these screenshots, you may see the messages from users under the nickname “REvil” on the mentioned Darknet forum. Possibly, he is one of the group administrators. In these messages, he describes that during the attack on Kaseya, their operator has mistakenly generated a false key. Instead of an individual key for each machine in Kaseya’s network, he generated the universal one, and unintentionally sent him in a pack with other “individual” keys. This mistake cost the group almost all ransom – they asked the company for 70 million euros, but got only €10 million.
Building the timeline
What if all events we see are just the self-liquidation of REvil? Kaseya was under attack in late July, and after the failure, UNKNWN suddenly ceases to exist. The network gets stopped, because some of the servers were compromised. Was that a self-punishment, or did someone decide to get rid of the unskilled administrator? Possibly, he was responsible for the Kaseya attack – but no one can prove that besides crooks themselves. But the assumption about punishment is backed by previous actions from group administrators. Earlier, they scammed their operators, explaining it as a “punishment” for some kind of violations.
Then, someone from the REvil group launches the network despite the fact that there was no official re-launch. At the end of September 2021, the operator was captured. Don’t you think that it was just a setup? This conclusion becomes even more obvious when we have a look at further actions. He was just punished for compromising the network – regardless of the fact he did not want to do it.
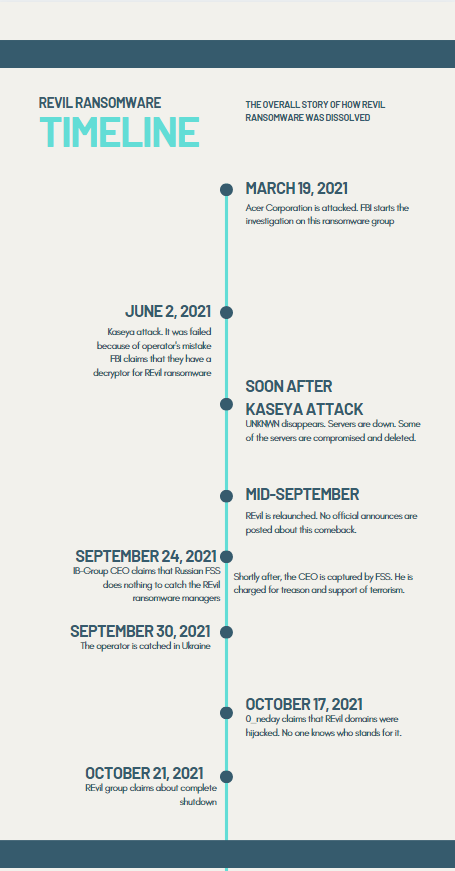
The timeline of the things happened to REvil group in 2021
The FBI was chasing the REvil for more than half a year, after the crooks asked Acer Corp. for the biggest ransom in history – $50 million. After the Kaseya incident, the rumors about the FBI having the decryption keys for all REvil cases appeared. But to get the decryption keys, they were about to get the key generator and logs – which is possible only when you have access to the internal server of this group.
Conclusions. REvil’s sad final
It seems that the “awakening” of the group in September was a fateful mistake. Highly likely, this network launch was one of the final nails into a REvil’s coffin. The FBI got everything they needed after seeing the network running again. Then, they just launched the copy of their servers, trying to bait the operators to log in. By doing that, fraudsters uncover their own IP address and other critical information, which surely points out who they are and how to find them. Sure, the operator which found this trick understood the danger, and hasten to close the connection.
User Review
( votes)

