Ransomware is losing effectiveness, and victims increasingly refuse to pay the ransom. Specialists have been observing this trend since the middle of 2021, and some factors contribute to it, which we will discuss below.
Ransomware Attack Victims Mass Refuse to Pay
According to the latest data from Coveware, a ransomware remediation firm, the number of victims of ransomware attacks who choose to pay the ransom has dropped to a record low. At the beginning of 2019, when ransomware was on its first peak, 85% of ransomware attack victims paid the ransom. By mid-2021 though, the percentage had decreased to 46% – quite a steep decline, if you ask me. And finally, in Q4 of 2023, only 29% of victims paid the ransom.
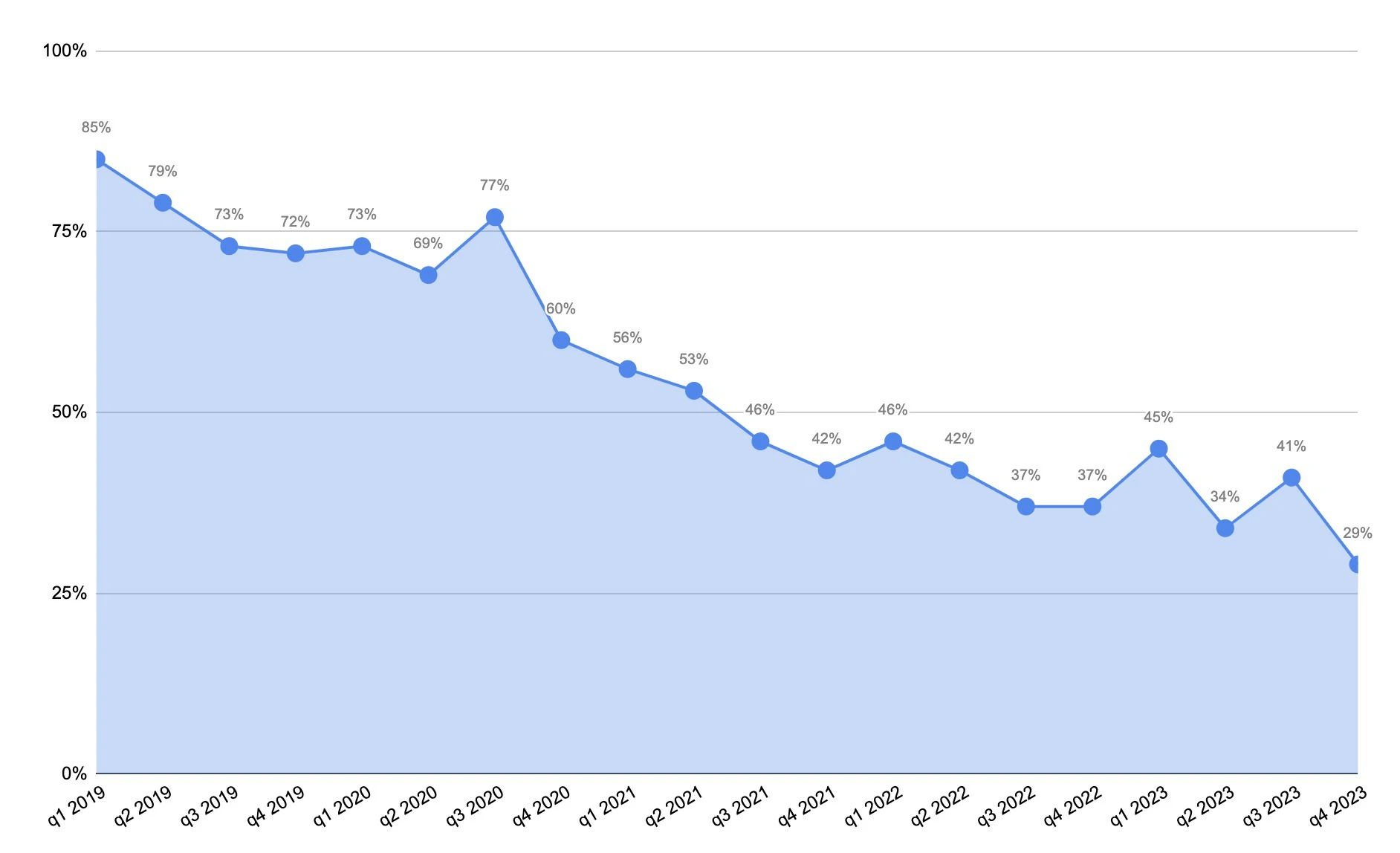
Ransom payment statistics. Data Source: Coverware
In 2019, ransomware groups began using double extortion tactics. This involves accessing victims’ networks and exfiltrating data before encrypting files. To prevent stolen data from being leaked or sold, ransom payments are required to obtain the keys to decrypt files. However, many victims paid the ransom to avoid a data leak rather than to obtain the decryption keys.
Why Do Companies Choose Not to Pay Ransom?
The trend is obviously good news. Just think of it – 71% of ransomware attack victims have refused to pay the ransom. However, this doesn’t necessarily mean that attacks have decreased. Instead, the companies simply refuse to contact the attackers, making their job much less paid. Though what caused this change in behavior among victim organizations?
Better Preparedness
One of the main reasons ransomware victims refuse to pay is that they are ready for such a case. Backups, disk encryption, network segmentation – you name it. As a result, they can restore their systems without relying on the decryption keys provided by the attackers. Experts say that more and more companies are investing in backup solutions and testing their recovery processes regularly.
Some ransomware victims can also decrypt their files using free tools developed by security researchers and organizations. For January 2024, there were 2 such decryptors released: for Tortilla ransomware, a variant of Babuk, and Black Basta. All this inspires hope to both organizations and people who fell victim to a ransomware attack.
Distrust of Ransomware Operators
Another factor that discourages ransomware victims from paying is the lack of trust in the ransomware operators. According to numerous reports, some ransomware groups do not keep their promises and fail to provide valid decryption keys. Moreover, it’s typical when threat actors don’t delete the stolen data or prevent leaks.It is a rather often case when paying the ransom can also lead to further extortion attempts or repeated attacks. For instance, the Conti ransomware group has been known to ask for additional payments after the initial ransom was paid.
Law Enforcement Crackdown
The report also cites the increased efforts by law enforcement agencies to disrupt ransomware operations and arrest ransomware operators. For example, in October 2023, the US Department of Justice announced the indictment of 12 Russian nationals for their involvement in the REvil ransomware group responsible for some of the most notorious ransomware attacks in 2021 and 2022. Additionally, law enforcement agencies have also been able to seize some of the cryptocurrency wallets used by ransomware groups to collect ransom payments. There was a case in November 2023, when the FBI seized over $6 million worth of Bitcoin from the DarkSide ransomware group, which had attacked the Colonial Pipeline in May 2021.
Legal Restrictions on Ransom Payments
Finally, paying ransom to ransomware groups has legal implications. It especially encounters those sanctioned by the US government or other authorities. Thus, paying ransom to these groups can result in fines or penalties for the victims or the intermediaries involved in the negotiation process. Furthermore, some countries or states have also imposed partial or complete bans on ransom payments. For example, they prohibit public entities or organizations from paying ransom to ransomware groups. Still, popular belief argues that these bans are counterproductive and ineffective. They can discourage victims from reporting attacks, hinder law enforcement investigations, and create a black market for ransom payments.
Is That Exclusively Good News?
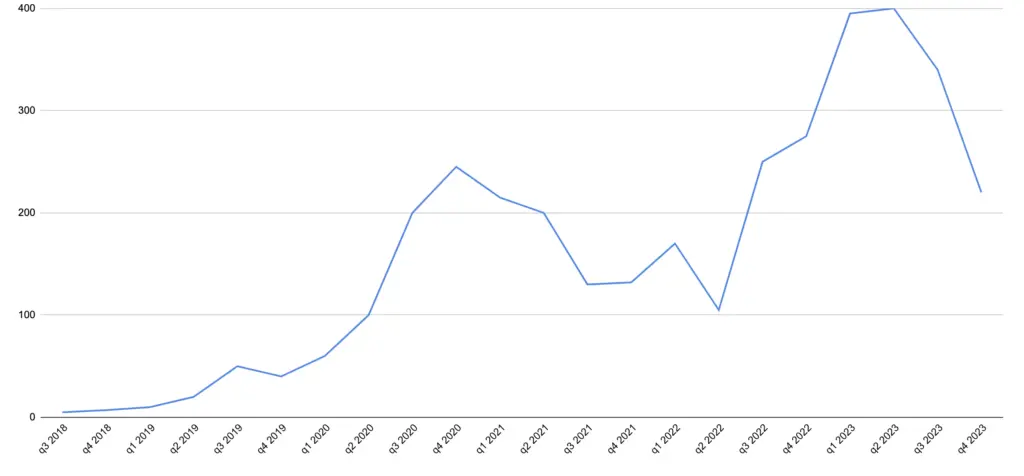
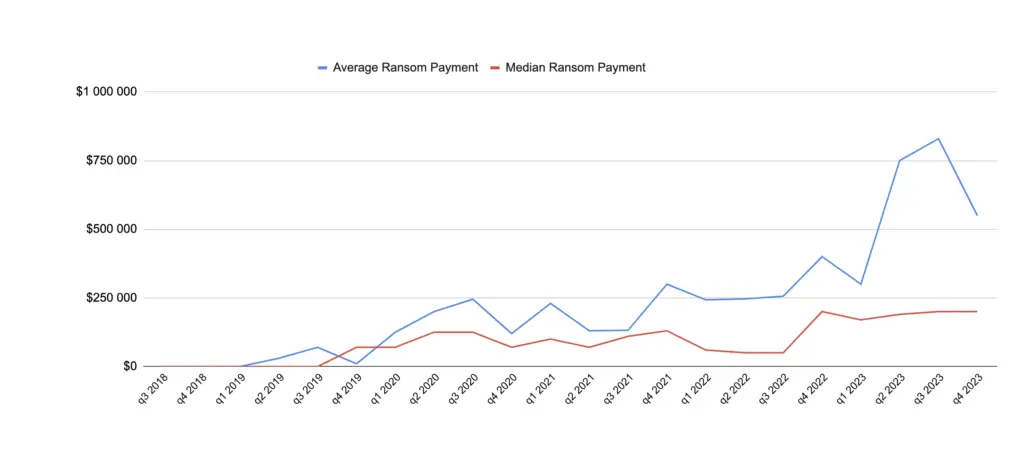
Every rain cloud has a silver lining – for this time, for cybercriminals. To respond to such a drastic decrease in the number of ransom payments, they decided to crank up the demanded sum. The numbers provided by the same Coverware show a steep increase in ransom sum paid in 2023. This may be associated with the fact that hackers intensively targeted bigger companies in that period of time, according to the same data source. Nonetheless, they started targeting something that can pay more – this obviously points at the fact that frauds feel the decrease in money flow.
Still, the fight against ransomware is possible to win, even though it may be effort-hungry. It will obviously take time and collaboration among various stakeholders – government, law enforcement agencies, security vendors, and ransomware victims. But the scale of a threat is nothing short of worldwide, and so should be the means to respond.