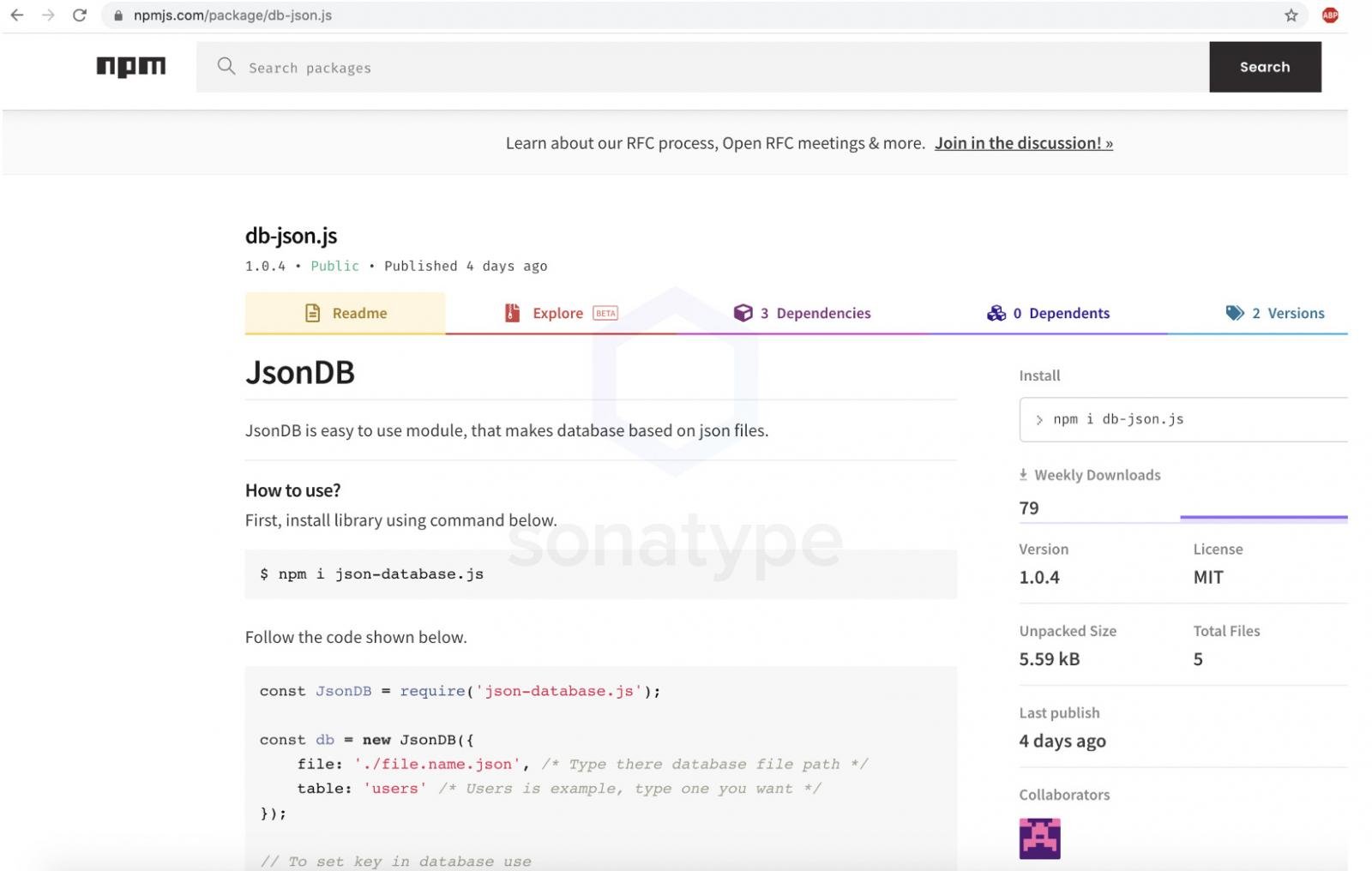
Another malware was found in the JavaScript package manager (Node Package Manager) – njRAT trojan installed malicious npm packages on infected machines.
The developers that installed the jdb.js and db-json.js packages were infected with the njRAT remote access trojan. Both packages were removed from npm earlier this week.Packages were created by the same author and described as tools that help working with JSON files. Both packages were uploaded to npm last week, and users downloaded them more than 100 times before Sonatype discovered malware in them.
According to Sonatype analysts, these packages contained a malicious script that was run after the developer imported and installed any of the two malicious libraries. The script performed basic reconnaissance on the infected host and then tried to download and run the patch.exe file (file on VirusTotal), which later installed the njRAT Trojan on the affected machine. This malware is also known as Bladabindi and has been used by cybercriminals since at least 2015.
To load njRAT without problems, the patch.exe loader changed the behaviour of the local Windows firewall by adding a rule for its command and control server to the whitelist before downloading the malware.
Since njRAT is a very serious threat, the npm security team recommends affected developers to consider that their systems were completely compromised.
It should be noted that since August this year, cybercriminals’ interest in npm has definitely increased. In recent months, experts have more than once discovered various malicious packages designed to steal data from infected systems.
Apparently, hackers are interested in breaking into developers in order to be able to steal credentials from confidential projects, source code, intellectual property, or prepare for attacks on larger supply chains.
Let me remind you about the fact that npm package was stealing information from browsers and Discord, as well as that Sonatype Information security specialists discovered malicious npm package with a backdoor.