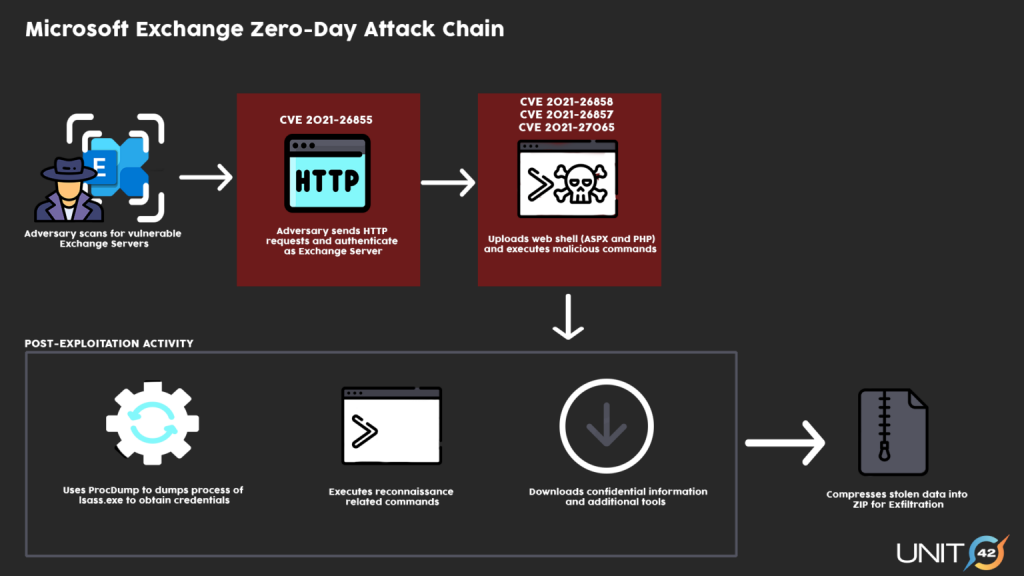
Last week, Microsoft engineers released unscheduled patches for four new vulnerabilities in the Microsoft Exchange mail server, which the researchers called ProxyLogon.
In fact, these vulnerabilities can be chained together, and their exploitation would allow an attacker to authenticate on the Exchange server, gain administrator rights, install malware, and steal data.A week ago, it was reported that fresh vulnerabilities were already under attack by the Chinese hacker group Hafnium. However, after the bugs were disclosed, other attackers joined the attacks on Exchange.
For example, ESET analysts write that APT LuckyMouse, Tick and Calypso, as well as other “not yet classified” groups, were involved in the attacks.
Red Canary experts report that ProxyLogon problems are used by at least one group to deliver web shells to infected servers, and then install DLTminer mining malware.
The attacks from several criminal groups have also been confirmed by Microsoft experts, who have updated their original report on Hafnium’s activity.
Even worse, according to Wired and KrebsOnSecurity, hackers no longer target victims, but simply search the network and attack any vulnerable Exchange servers.
Former head of the Department of Homeland Security’s Cybersecurity and Infrastructure Protection Agency (DHS CISA), Chris Krebs says government agencies and small businesses are more affected by these attacks than large enterprises. On Twitter, he notes that incident response teams are having a very difficult time right now, especially with the education sector and local governments.
Among the large organizations that have been already affected are the Ministry of Labour and Social Affairs in the Czech Republic and post offices in Prague, as well as the European Banking Authority.
Many countries (including Australia, United Kingdom, Germany, Romania, Austria, Sweden, Finland, Spain, New Zealand, France, Singapore, Hungary, Ireland, Canada and Italy) have issued national security alerts warning companies and government agencies about the threat and ask everyone to install patches as soon as possible.
Taking into account the seriousness of the situation, in addition to the usual patches, Microsoft engineers prepared fixes for old and unsupported versions of Exchange, and also released a special PowerShell script designed to check Exchange servers for hacks and known indicators of compromise (web shells).
A similar script was presented by the CERT-Latvia team.
In addition, over the weekend, Microsoft updated the Microsoft Support Emergency Response Tool (MSERT) to enable the tool to detect signs of intrusion on servers that do not have Microsoft Defender installed and that cannot automatically detect ProxyLogon attacks.
In turn, PwnDefend has compiled a list of IP addresses associated with scanning and hacking Exchange mail servers over the past few weeks.
Let me remind you that I also talked about the fact that Microsoft and McAfee form Ransomware Task Force (RTF).