Microsoft experts have discovered a new Prestige ransomware that is being used to attack transport and logistics organizations in Poland and Ukraine.
Although the researchers have not yet linked Prestige activity to specific attackers, the company noted that Prestige activity is similar to the attacks of the previously discovered FoxBlade malware.Let me remind you that we also reported that Google Specialists Said That Former Members of Conti Are Attacking Ukrainian Organizations, and also that Sandworm Targets Ukraine With Industroyer2 Malware.
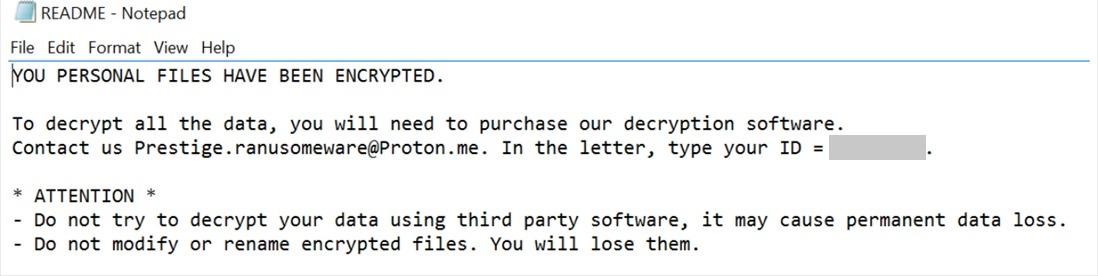
Analysts say that Prestige refers to itself as “Prestige ranusomeware” in its extortion notes, and the first attacks of this malware were recorded on October 11, 2022, when several incidents occurred with a difference of only one hour.
So far, analysts have not linked the Prestige attacks to specific attackers and track this activity under the identifier DEV-0960. At the same time, the report notes that the activity of Prestige has a certain similarity with the attacks of the previously discovered malware FoxBlade (aka HermeticWiper). This destructive malware was used to attack Ukrainian organizations shortly before the start of a special military operation.
A Microsoft report says that Prestige operators use several methods to deploy payloads on victim networks, and this has nothing to do with what security measures the defenders use. Experts list three deployment methods:
- the ransomware payload is copied to the ADMIN$ shared folder, and the open source Impacket WMIexec is used to remotely create a scheduled task on target systems to execute the payload;
- the ransomware payload is copied to the ADMIN$ share, and Impacket WMIexec is used to remotely invoke an encoded PowerShell command on target systems to execute the payload;
- the ransomware payload is copied to an Active Directory domain controller and deployed to systems using the default domain group policy.
It is noted that the malware encrypts files based on a list of extensions and adds the .enc extension to all affected files. The Prestige uses the CryptoPP C++ library for AES encryption of each file and deletes all backups and shadow copies of all volumes to make it difficult to restore information.
