The Computer Emergency Response Team of Ukraine (CERT-UA) reports a counteracted cyberattack which was planned by infamous Russian hacking group Sandworm. The attack on the unnamed energy provider was to take place on April the 8, but was successfully thwarted.
What is Industroyer2 Malware?
Hacking group who is said to be affiliated with Russia’s military intelligence had the task to sabotage the operations of an unnamed energy provider in the country. In the attempted attack threat actors used regular disk wipers and ICS-capable malware together with updated versions of the Industroyer malware.
First time threat actors deployed Industroyer malware in a 2016 assault on Ukraine’s power grid. And once again Ukraine is at the center of cyber attacks that target its critical infrastructure. This renewed Industroyer campaign goes together with the latest waves of wipers, a malware that has been targeting different Ukrainian sectors recently.
“The attackers attempted to take down several infrastructure components of their target, namely: Electrical substations, Windows-operated computing systems, Linux-operated server equipment, [and] active network equipment,” the State Service of Special Communications and Information Protection of Ukraine (SSSCIP) said in a statement.
CERT-UA also warns over waves of spear-phishing campaigns conducted by another Russian threat group Armageddon which is said to have ties with the Federal Security Service (FSB). Cybersecurity specialists say this group has been attacking Ukraine since at least 2013.
The findings come amidst the news over court authorized takedown of Cyclops Blink. Threat actors from Sandworm also controlled this advanced modular botnet.
Sandworm attempted to deploy Industroyer2 malware against high-voltage electrical substations in Ukraine. In addition to it, they also used several destructive malware families including AwfulShred, SoloShred, OrcShred and CaddyWiper.
Industroyer that also goes by the name “CrashOverride” is regarded as one of the biggest threats to industrial control systems since Stuxnet. Both modular malware examples share the capabilities of gaining direct control of switches and circuit breakers at an electricity distribution substation.
Apart from full scale war at it`s territory, Ukraine is also fighting on the cyber frontline
The same as its predecessor the new version of Industroyer takes advantage of an industrial communication protocol called IEC-104 to seize control of the industrial equipment such as protection relays that are used in electrical substations. In addition, cybersecurity specialists note the sophistication and high customization of a new version.
Attack chain of Industroyer
Cybersecurity specialists believe that the victim’s power grid network has been penetrated in two waves. The initial compromise occured no later than February 2022 which happen together with the Russian invasion of Ukraine. In April threat actors conducted follow on infiltration that allowed them to upload Industroyer2.
A revealed compilation timestamp of March 23, 2022 indicates that threat actors planned the attack for at least two weeks beforehand. Though in a forensic analysis of the artifacts left by the Industroyer2 specialists took some significant bit of information there’s something still unclear like: How the attackers moved from IT network to the the Industrial Control System (ICS) network, or how the targeted power facility was initially compromised?
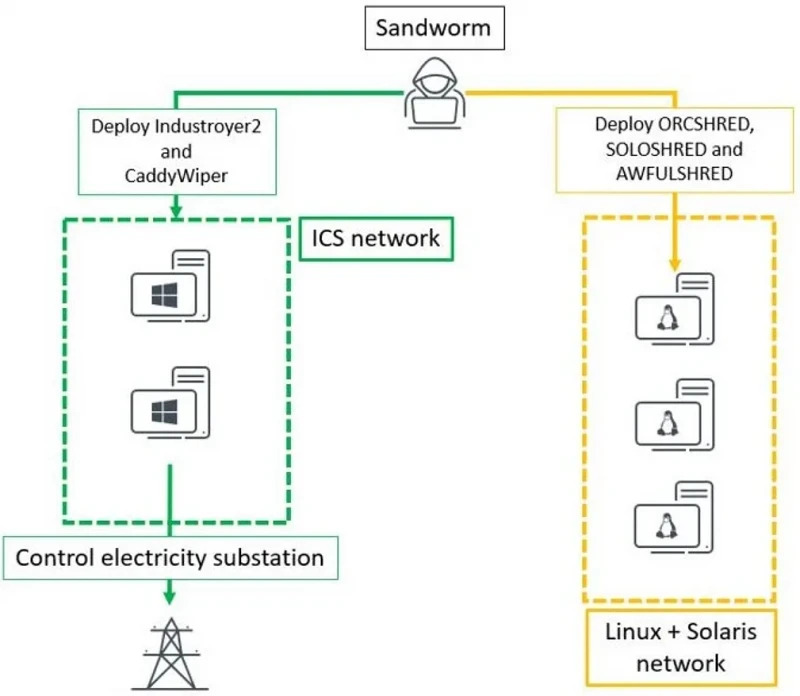
Visualized Industroyer2 chain of an attack
The destructive actions against company’s infrastructure were set on April 8, 2022 but failed. Cybersecurity specialists say that after the Industroyer2 malware should have done its job, the execution of a data wiper called CaddyWiper was set to erase the traces of it 10 minutes later.
In addition to the Industroyer2 and CaddyWiper, threat actors also deployed Linux worm called OrcShred. With the help of it they further deployed AwfulShred and SoloShred aimed at Linux and Solaris systems respectively. Both malwares render the targeted machine fully unoperable.
Timeline of events
To better understand the general evolvement of the situation, you can take a look at the next timeline:
- 2022-02-24: Russia started a war against Ukraine;
- 2022-03-14: Threat actors deployed CaddyWiper against a Ukrainian bank;
- 2022-04-01: Threat actors deployed CaddyWiper against a Ukrainian governmental entity;
- 2022-04-08 14:58 UTC: Threat actors deployed CaddyWiper on some Windows, Linux and Solaris machines at the energy provider;
- 2022-04-08 15:02:22 UTC: The malware operators created the scheduled task to launch Industroyer2;
- 2022-04-08 16:10 UTC: The scheduled execution of Industroyer2 was to cut power in one Ukrainian region;
- 2022-04-08 16:20 UTC: Scheduled execution of CaddyWiper on the same machine was to erase Industroyer2 traces.
Technical analysis of the Industroyer2
Threat actors deployed Industroyer2 as a single Windows executable named 108_100.exe and executed it creating a scheduled task on 2022-04-08 at 16:10:00 UTC.
According to the PE timestamp, the executable was compiled on 2022-03-23 that makes cybersecurity specialists assume that the attack had been planned for more than two weeks beforehand.
Industroyer2 only executes the IEC-104 (IEC 60870-5-104) protocol to communicate with industrial equipment. The exploit of this protocol also gives threat actors control over protection relays used in electrical substations. The Industroyer2 malware version differs from that of 2016 year. The 2016 Industroyer variant was fully modular platform with payloads for multiple ICS protocols.
Not to take into consideration the above mentioned difference cybersecurity specialists note that both variants of the malware share the same source code.
Industroyer2 boasts high configuration hard coded in it’s body that dictates the malware actions. But not unlike the Industroyer it stores configuration in a separate .INI file. Because of this threat actors will need to recompile Industroyer2 for each new environment or victim.
However judging by how often this malware is used and why, it’s not a big deal for these particular threat actors.
Sandworm operators store the new configuration format as a string and then add it to the IEC-104 communicative activity of the malware. Industroyer2 has the ability to communicate with several devices at the same time.
Cybersecurity specialists argue what possible damages for other world will have cyber war between Ukraine and Russia
The configuration has values that the malware uses during communication via IEC-104 protocol such as timeouts, Information Object Addresses (IOA) and ASDU (Application Service Data Unit) addresses.
Before Industroyer2 connects to the targeted devices it deletes the legitimate process used in standard daily operations. In addition, the malware also prevents the restart of the legitimate process by adding .MZ to the filename of the application.
Industroyer2 produces a log file or outputs its progress to the console window. But instead of meaningful texts as in the previous version there are only various error codes. Cybersecurity specialists assume it was specifically done in order to harden the analysis.
The analysis of this malware is still in the process to further determine the exact actions taken for each device.

