Attackers hack into Microsoft SQL servers, turning them into proxy servers, which they then rent out for money.
South Korean company Ahnlab talks about a malicious campaign in which hackers steal someone else’s bandwidth by installing proxyware on hacked machines and using them as a proxy.Such proxy systems are used by tenants for a variety of purposes, including legitimate testing, data collection, or content distribution. However, such proxies also allow access to “live” IP addresses that are not blacklisted by online stores and can be used for a variety of illegal activities (of course, without the user’s awareness).
Let me remind you that we also wrote that Mining botnet Vollgar bruteforced Microsoft SQL servers for two years, and also that KingMiner botnet hacks MSSQL to install miner.
Experts explain that there are services that allow device owners to turn them into proxies and receive a certain percentage of the amounts charged to customers in exchange for “sharing” the bandwidth. For example, Peer2Profit service statistics say that users earn up to $6,000 per month by installing proxyware on thousands of devices.
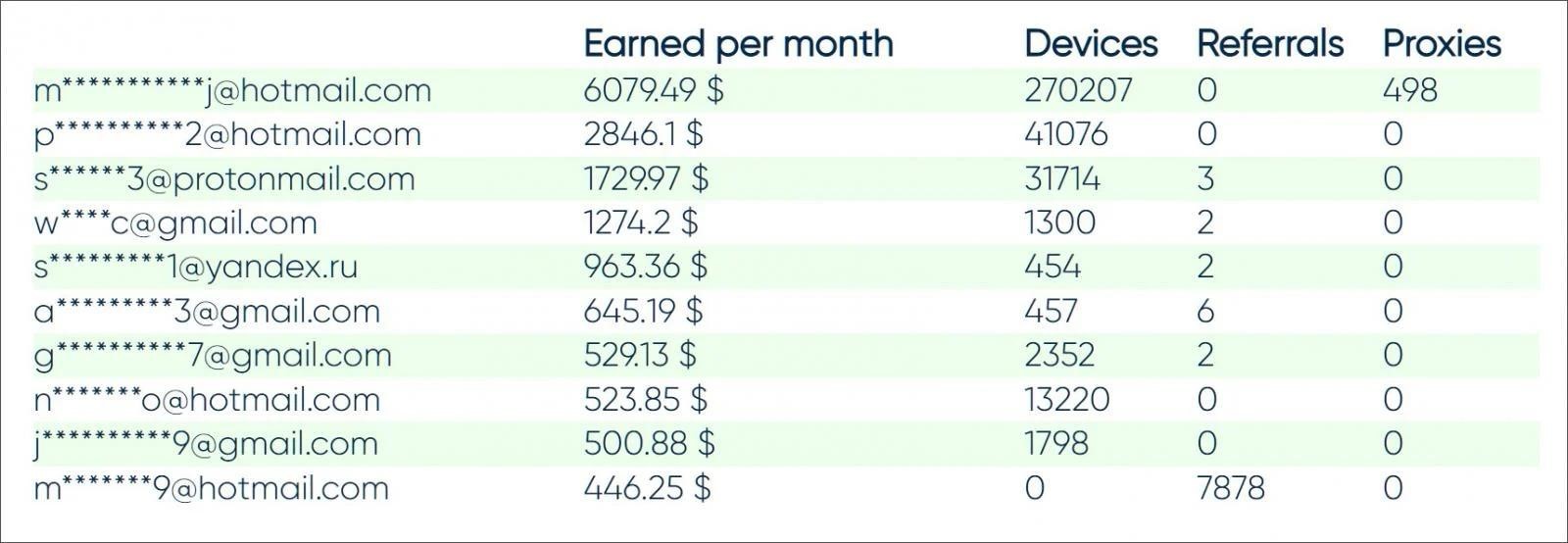
According to Ahnlab analysts, lately, not ordinary users, but hackers, are increasingly earning on such services. Researchers write that new malicious campaigns have emerged, in which attackers infect victims with proxyware in order to earn money. Hackers get a percentage for using someone else’s bandwidth by setting their email address as the user’s mail, and the victims do not notice anything or sometimes experience slight slowdowns and connection failures.
Experts describe the installation of proxyware for services such as Peer2Profit and IPRoyal, which are often distributed using adware and other malware. So, after infection, the malware checks if the proxy client is running on the host and can use the p2p_start() function to start it if it is not active.
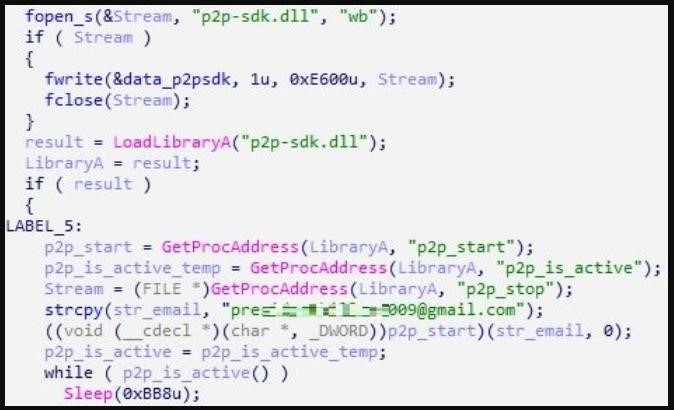
In the case of IProyal Pawns, the malware prefers to install the CLI version of the client instead of the GUI version, since the process should work as stealthily as possible and in the background.
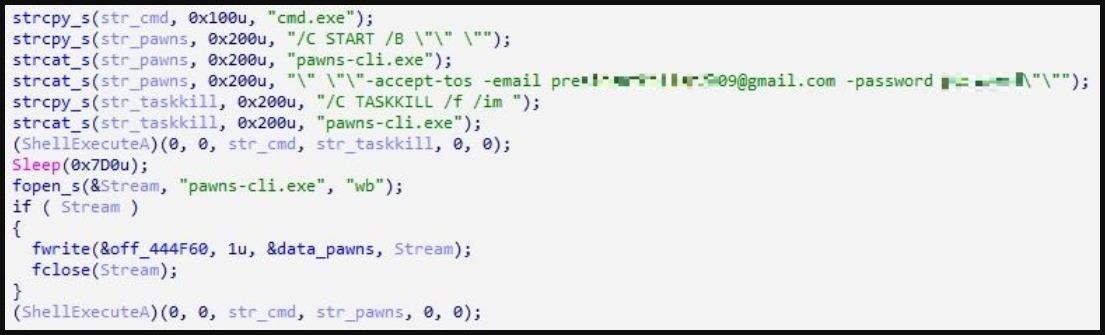
Also, sometimes attackers use Pawns as a DLL and substitute their email addresses and passwords as encoded strings by running the Initialize() and startMainRoutine() functions.
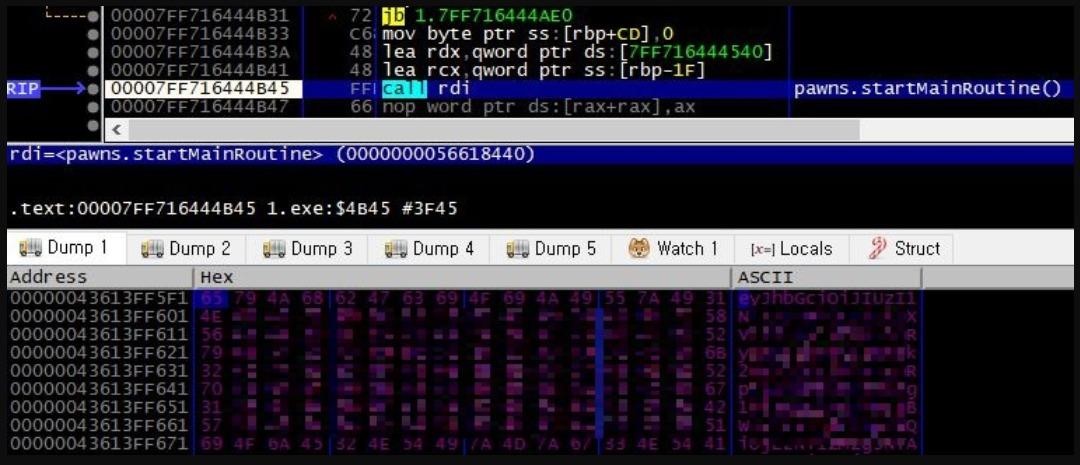
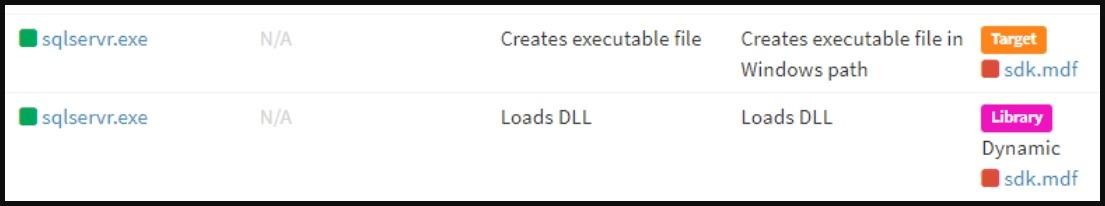
According to an Ahnlab report, malware operators are using this scheme to generate revenue and often attack vulnerable MS-SQL servers to install Peer2Profit clients. This activity has been observed since the beginning of June 2022, and most of the logs received from infected machines indicate the existence of a packaged UPX file named sdk.mdf.
The researchers write that it is not yet clear how much money attackers make with such attacks.
