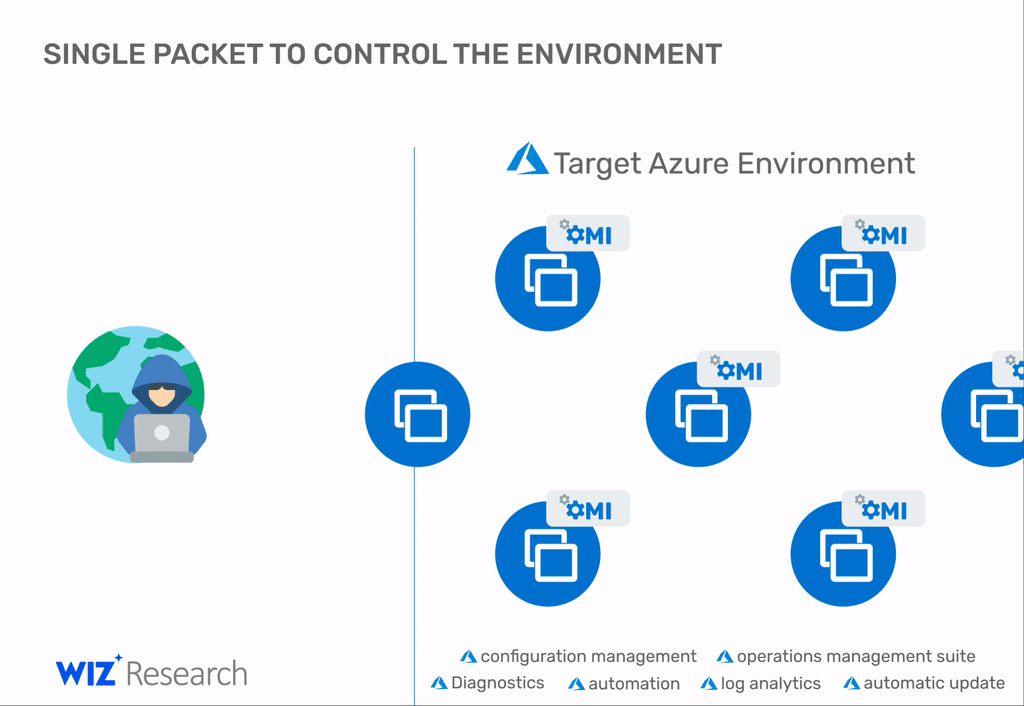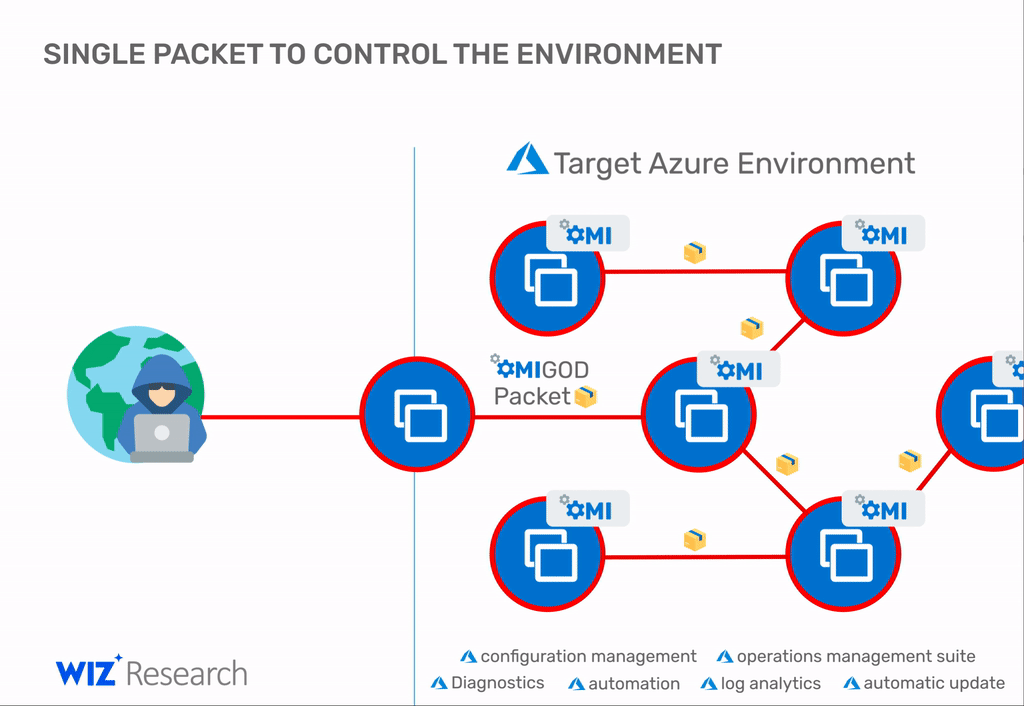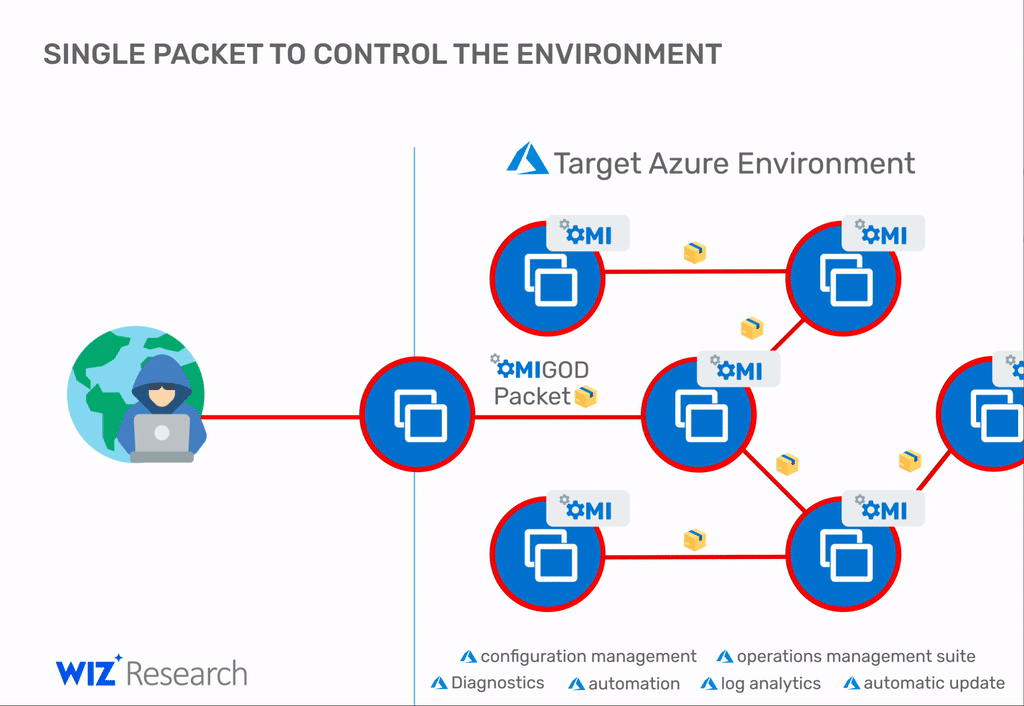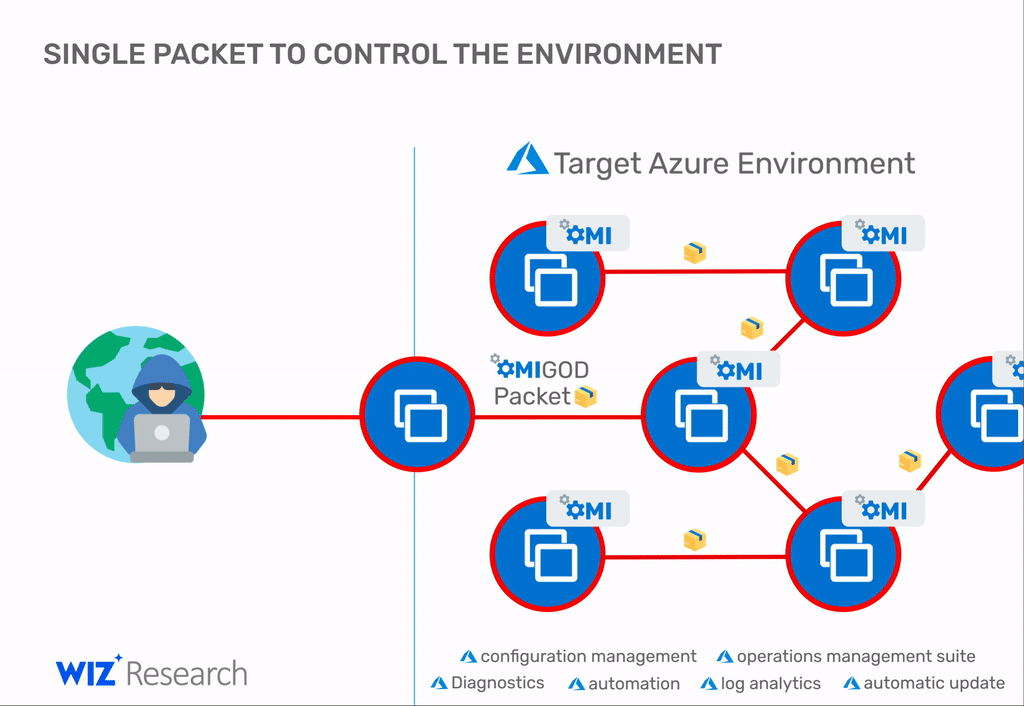
Microsoft patches four critical vulnerabilities with a common name OMIGOD. Issues were found in Open Management Infrastructure (OMI), which is silently and automatically installed on Azure Linux VMs (more than half of all Azure instances).
OMIGOD issues were fixed in OMI version 1.6.8.1, but there is no automatic update mechanism in the application, so most Azure Linux VMs will remain vulnerable until the update is manually installed.Open Management Infrastructure is the Linux equivalent of Microsoft Windows Management Infrastructure (WMI), a service that collects data from on-premises environments and synchronizes it with a central management server.
Unbeknownst to most Azure customers, Microsoft silently installs OMI on all Azure Linux VMs. Moreover, the OMI client runs with root privileges.
OMIGOD contains the following vulnerabilities:
- CVE-2021-38647 – RCE without root authentication (9.8 points on the CVSS scale);
- CVE-2021-38648 – privilege escalation vulnerability (7.8 on the CVSS scale);
- CVE-2021-38645 – Privilege escalation vulnerability (7.8 on the CVSS scale);
- CVE-2021-38649 – Privilege escalation vulnerability (7 on the CVSS scale).
As you might guess, the most serious of the four problems is CVE-2021-38647, which allows an attacker to hijack a virtual machine simply by sending a specially crafted packet. Even worse, once inside the network, an attacker can repeat the attack on other systems and continue until the network is completely compromised.
The researchers note that the ports through which this bug can be exploited are fortunately not “visible” on the Internet by default.
Alas, if these ports are not available, an attacker could still abuse the other three OMIGOD errors by tricking the Azure user into opening a malicious file, which would ultimately allow the attacker’s code to gain root access.
But the worst news in this situation is the already mentioned lack of a mechanism for automatic updates in OMI. The fact is that most users do not know about the existence of OMI at all, and its work is invisible to them, so they obviously will not update it manually either. Meanwhile, OMI is installed and enabled upon activation of any of the following tools and services:
- Azure Automation
- Azure Automatic Update
- Azure Operations Management Suite (OMS)
- Azure Log Analytics
- Azure Configuration Management
- Azure Diagnostics.
Let me remind you that earlier we reported that Microsoft fixes MSHTML vulnerability and residual PrintNightmare issues.