Guardicore researchers have discovered a serious bug in Microsoft Exchange Autodiscover: the problem can be abused to collect credentials from Windows domain and applications. Because of this, approximately 100,000 logins and passwords have already leaked from Windows domains of users from all over the world.
The root of the problem lies in the incorrect operation of the Microsoft Autodiscover protocol. With this feature, mail clients can automatically discover mail servers, provide them with credentials, and get the appropriate settings. Autodiscover is an important part of Exchange because it allows administrators to easily verify that clients are using the correct settings for SMTP, IMAP, LDAP, WebDAV, and so on.To obtain automatic settings, email clients typically ping against a set of predefined URLs that derive from the email address configured on the client. For example, the experts used the mail [email protected] and the client tried to use:
- https://autodiscover.example.com/autodiscover/autodiscover.xml
- http://autodiscover.example.com/autodiscover/autodiscover.xml
- https://example.com/autodiscover/autodiscover.xml
- http://example.com/autodiscover/autodiscover.xml
Guardicore explains that the client will iterate over URLs until it is successfully authenticated to the Microsoft Exchange server and receives configuration information. In addition, this mechanism has a “rollback” procedure that is triggered if the client does not find the Autodiscover Exchange endpoint.
Based on these findings, the company registered a number of Autodiscover domains that were available and launched honeypots on them. Among them:
- Autodiscover.com.br (Brazil);
- Autodiscover.com.cn (China);
- Autodiscover.com.co (Colombia);
- Autodiscover.es (Spain);
- Autodiscover.fr (France);
- Autodiscover.in (India);
- Autodiscover.it (Italy);
- Autodiscover.sg (Singapore);
- Autodiscover.uk (Great Britain);
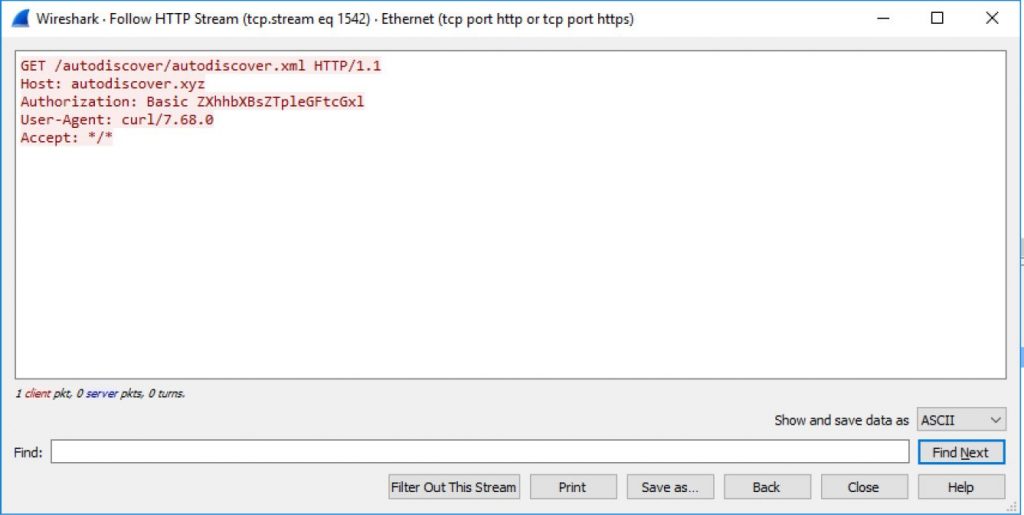
- Autodiscover.xyz;
- Autodiscover.online.
It ended up with an impressive collection of credentials for a wide variety of companies and businesses, including food manufacturers, banks, power plants, real estate, shipping and logistics, fashion and jewellery firms, and a number of publicly traded Chinese companies.
Although all credentials came over unencrypted HTTP connections, the researchers also detail how to collect credentials using NTLM and Oauth.
Since there are no patches yet, and Microsoft has not commented on the situation, the researchers advise companies to block any Autodiscover domains at the firewall or DNS level so that devices cannot connect to them (the company has prepared a list of such domains). It is also recommended to disable Basic Authentication as it sends credentials in clear text.
Let me remind you that recently vulnerabilities in Microsoft Exchange have affected tens of thousands of organizations.