The completely new variant of malware distribution says not only about the professionalism of its creators. Possibly we are spectating another serious security breach in Windows. A lot of users, and especially developers, were happy to see the Windows Subsystem for Linux. After 5 years of being successfully used on Windows, no one expected that this thing could turn into a hazard.
Linux malware for Windows?
Windows Subsystem for Linux (shortly WSL) is an integrated environment in Windows. This subsystem allows the operating system to launch and use the applications for Linux (primarily – for Debian-like distributions). This “compatibility layer” allows you to minimize the efforts needed for launching the Linux programs on your PC. Previously, users were using dual-boot or virtual machines for this purpose.
Such close relations between Windows and Linux, that is run under WSL, require simplified access to the storage devices. While running Linux on both virtual machine or dual boot, you have your Windows root directory (and all Windows-related files) isolated. Using the WSL allows you to control your disks from both systems simultaneously. And this ability, exactly, is a security breach, that allows the crooks to inject malware without any risks of being detected.
Malware injection through WSL: how it works?
Malicious items that were detected first by Black Lotus Labs are, in fact, small ELF files, that were acting as downloaders. After launching into the WSL environment, they connect to the command server and get the payload. It seems that this malware was designed for some specific conditions. This conclusion appeared in the Black Lotus Labs report, when they saw that no malware has been downloaded. But surely, the fact that an initial virus has successfully connected to the command server clearly shows its abilities.
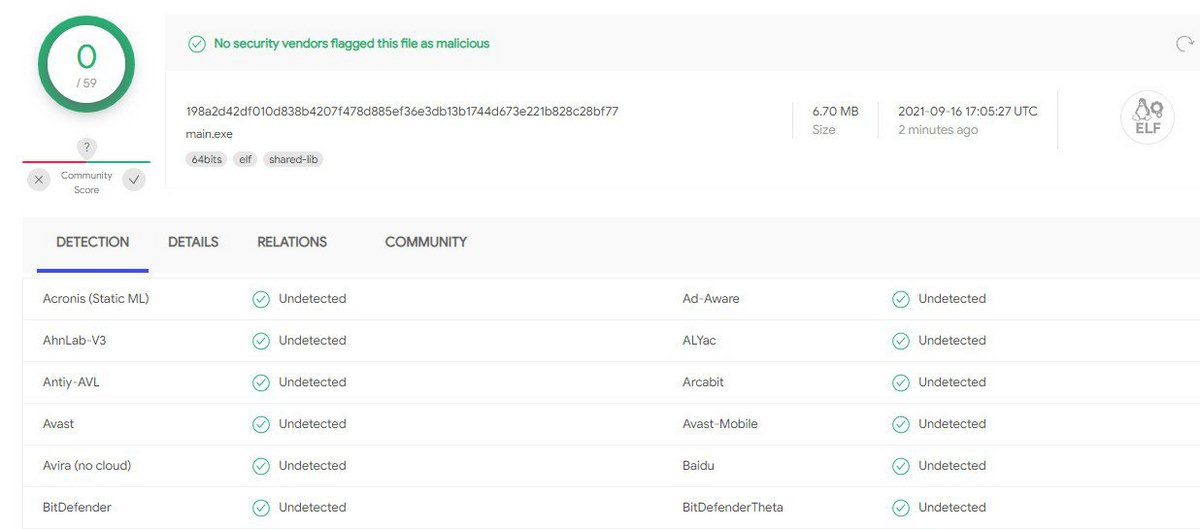
WSL malware was not detected at all (as of 09/16)
The thing that shocked the cybersecurity analysts is that this malware is almost ignored by anti-malware engines. As of 09/21, only 6 antivirus programs detected it, among more than 5 dozen ones present on VirusTotal. Even Microsoft Defender, which works on a very deep level into the system, and must see those manipulations, is not able to detect this threat.
Why can’t anti-malware software stop it?
It is hard to say about the reasons for such recklessness of antivirus programs. The only supposement that looks realistic is that antivirus programs have the preliminary guidance to trust all WSL-related files and actions. Hence, when the user launches the aforementioned malware, all security tools just think of it as of something legit.

The way WSL malware acts in your system
Another thing that possibly makes the antivirus software useless is the fact that the initial virus is Linux-based. Executable and Linkable File (ELF) cannot be run on Windows for obvious reasons. During the scans, some security tools will ignore this file following the rule “it cannot be run on Windows → it is not dangerous”. Only heuristic engines can suspect something, and at least block this malware. However, not each antivirus has the heuristic detection module, and not each will pay attention to what’s happening at WSL.
How to avoid the malware injection through WSL?
Linux is a very specific operating system, and not only because it is a UNIX-like system. It has too different architecture to compare it with Windows, when it comes to malware launching prevention. Moreover, the user base of Linux is less than 2% of the total computer market, so the “soft” malware is likely absent. Things like adware or browser hijackers are useless, hence, you will likely deal with spyware or ransomware. Those virus types try to be as stealthy as possible, so it is almost impossible to detect them before they have started their activity.
The only way to be sure that you are not launching the malware is to follow the rules of cybersecurity. Don’t use the software from untrustworthy sources, as well as programs created by a no-name organization. The smaller the company is – the less moral restrictions it has. Small software creators can barely resist when it comes to making serious money through malware injection. Keep all your anti-malware programs up to date – the countermeasures for this vulnerability will surely appear in the near future1. Those rules must be just like washing your hands – obligatory and obvious to perform.
User Review
( votes)References
- See how to repair your computer after the malware attack.



