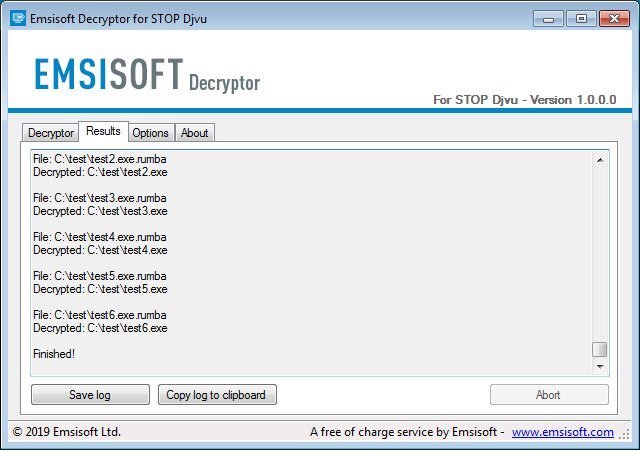
Emsisoft experts, together with ransomware expert Michael Gillespie, have released a free STOP Trojan decryptor. The utility works with 148 malware variants and decrypts files locked no later than August of this year.
Although STOP is less known than GandCrab, Dharma, and other ransomware Trojans, in this year it accounts for more than half of the detected attacks. Moreover, the next rating participant, the aforementioned Dharma, lags behind him by this indicator as it was detected four times less often.A significant role in the prevalence of STOP is played by its diversity: in the most active periods, experts found three or four new versions daily, each of which hit several thousand victims”, – says Michael Gillespie.
To date, the family includes about 160 representatives, and the total number of affected users is approaching half a million. Most of the attacks are in Europe and South America, India and Southeast Asia. The threat also affected the United States, Australia and South Africa. The encryptor bypasses Russian users by checking the language settings of the affected system before starting work.
STOP victims most often receive it bundled with pirated and free software. The malware not only encrypts user files, but also installs malicious browser extensions, clickers, and other unwanted programs. At the beginning of 2019, experts reported that one of the STOP versions distributes the Azorult Trojan, which can steal user information and deliver other malware to the computer.
Read also: Researchers Create Free Nemty Ransomware Decryptor
A published decryptor is not the first attempt to approach this encryptor. Previously, researchers found offline keys in the code that the malware uses without connecting to the management server. This find in some cases helps to restore the files to their original form, but over time, attackers have changed the encryption mechanism. The experts also developed the still relevant decryptor for the Puma ransomware, which is part of the STOP family.
The development of Gillespie and Emsisoft specialists uses a characteristic feature in the work of STOP – the malware creates an encryption key based on the first five bytes of the affected object. This allows experts to recreate the key using the source file. In addition, for some files, the code starts from the same sections – for example, Microsoft Office documents coincide with ZIP archives in this. As a result, decryption of one object allows you to work with other formats.
How to decrypt attacked files?
To use the descriptor, the user needs to train the program – download the same document in encrypted and original form through the online interface. Such pairs need to be selected for each file format that needs to be restored. Trained in this way, the utility will then be able to decrypt all objects of the corresponding formats.
The creators of the decryptor specify that their program is trained on objects weighing up to 150 KB. Experts recommend searching for such documents in e-mail – attachments that the user also saved on the hard drive may be saved in letters.
At the end of the training, a link to the decryptor will appear. The user needs to download and run it, accept the terms of the license agreement, and then specify the folders with locked files. The creators of the utility emphasize that decryption can take a long time, and the program requires an Internet connection throughout the process.
According to experts, the decryptor can return data from 70% of STOP victims. For other users, experts recommend archiving encrypted data and wait for new utilities to appear.