Security firm Imperva reported that they recently copd with a ransomware DDoS attack targeting an unnamed website that peaked at 2.5 million requests per second.
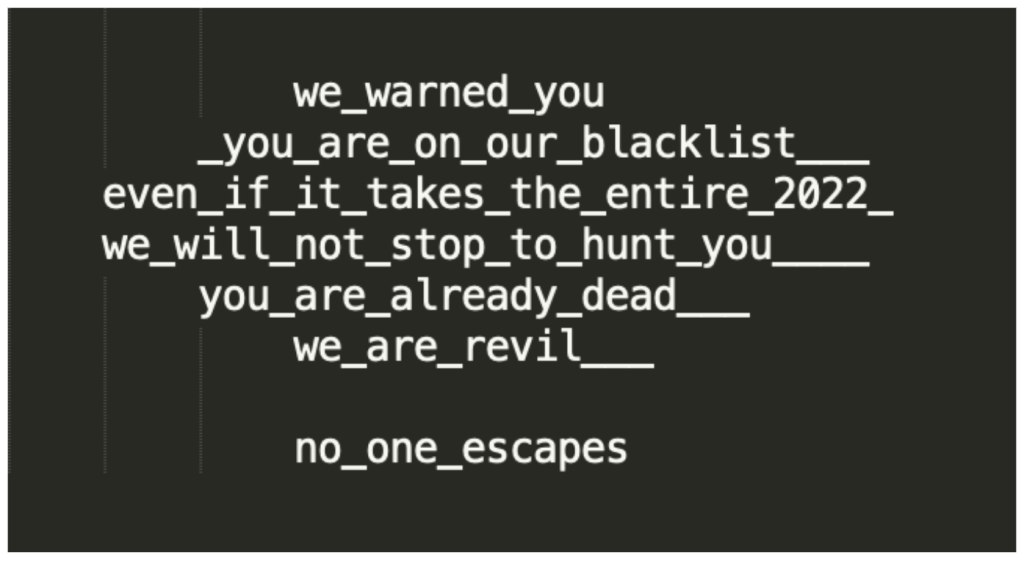
The researchers say that an unnamed organization affected by the aforementioned attack received several ransom notes, including those integrated into the attack itself.
More about this source textSource text required for additional translation information
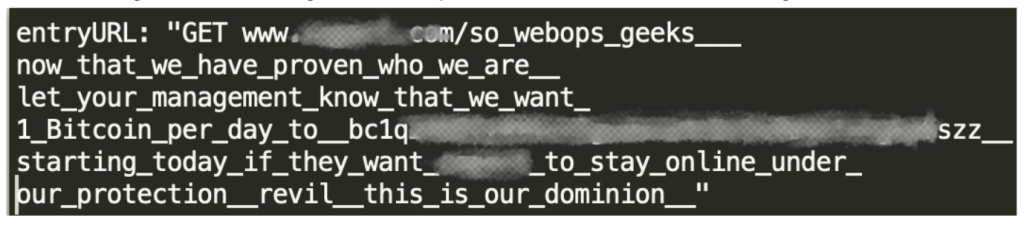
The attackers wanted the company to make a payment in bitcoin, otherwise they threatened to take it offline, which would cause the victim to lose “hundreds of millions of market capitalization.”
At the same time, the attackers called themselves REvil, that is, the name of the infamous extortionist group, whose activities were stopped by law enforcement officers at the beginning of this year.
The 2.5 million requests per second attack reportedly lasted less than a minute, with one of the subsites operated by the same victim company experiencing a similar attack that lasted for about 10 minutes and constantly changed vectors to prevent possible mitigation.
Imperva believes that the attack came from the previously infamous Mēris botnet, which continues to use the already patched vulnerability in Mikrotik routers (CVE-2018-14847) for its operations.
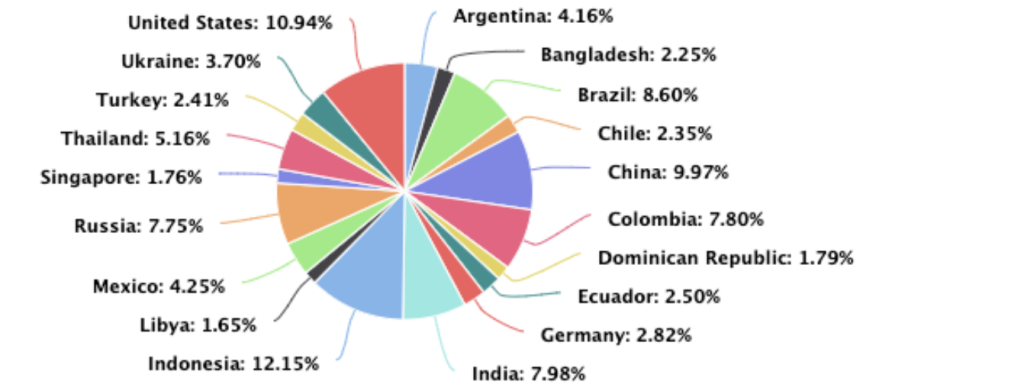
The main source of attack was Indonesia, followed by the US, China, Brazil, India, Colombia, Russia, Thailand, Mexico and Argentina.
Let me remind you that we also talked about the fact that TsuNAME vulnerability can be exploited for DDoS attacks on DNS servers.