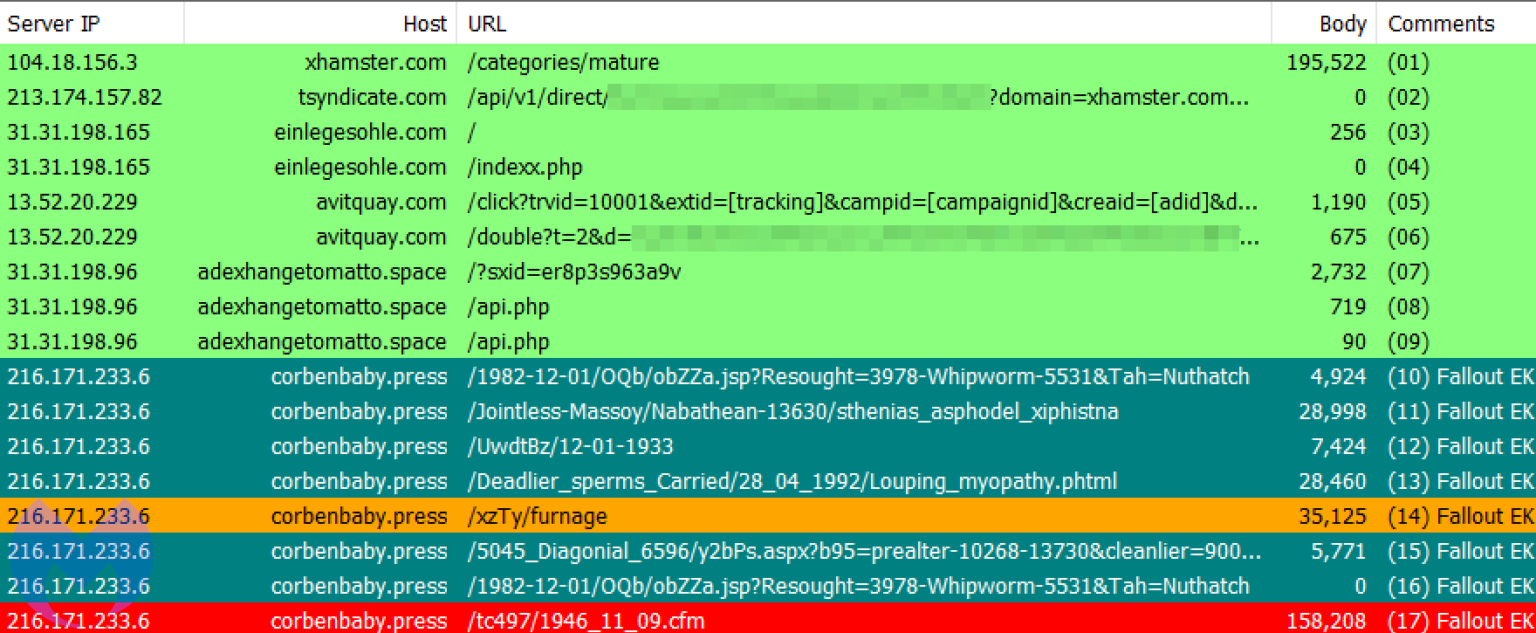
Malwarebytes has discovered the Malsmoke group, whose malicious ads have infiltrated virtually all ad networks that partner with porn sites. Mostly IE and Adobe Flash Player users were affected.
Most of the hackers injected their ads on porn sites, and the ads redirected victims to malicious sites that hosted the Fallout and RIG exploit kits.As a rule, the attackers acted through small sites, but finally they hit the real jackpot and placed their ads even on the xHamster portal, one of the largest porn sites in the world, which attracts billions of visitors monthly.
We saw possibly the largest campaign to date on top site xhamster[.]com from a malvertiser we have tracked for well over a year. This threat actor has managed to abuse practically all adult ad networks but this may be the first time they hit a top publisher”, — say Malwarebytes specialists.
The researchers note that the exploit kits mainly exploited various vulnerabilities in Adobe Flash Player and Internet Explorer (for example, CVE-2019-0752 and CVE-2018-15982) and thus installed various payloads on victims’ machines, including Smoke Loader, Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted”, — also write Malwarebytes experts.
Let me remind you that information security experts write about a significant decline in the popularity of exploit kits since 2018. The fact is that using them is becoming more and more difficult, because modern browsers are no longer so easy to compromise, especially after the massive abandonment of Flash and the slow death of IE. However, this does not stop hackers.
Despite the advice from Microsoft and security experts, we can see that a number of users (both home and corporate) around the world have not yet switched to a modern and fully supported browser. As a result, exploit kit authors are surviving the last drops of vulnerabilities in Internet Explorer and Flash Player”, — summarized Malwarebytes in their report.
Let me remind you that recently Emsisoft experts were surprised to discover ransomware program that is not interested in a cash buyback. Instead, the Ransomwared malware requires an intimate photo.