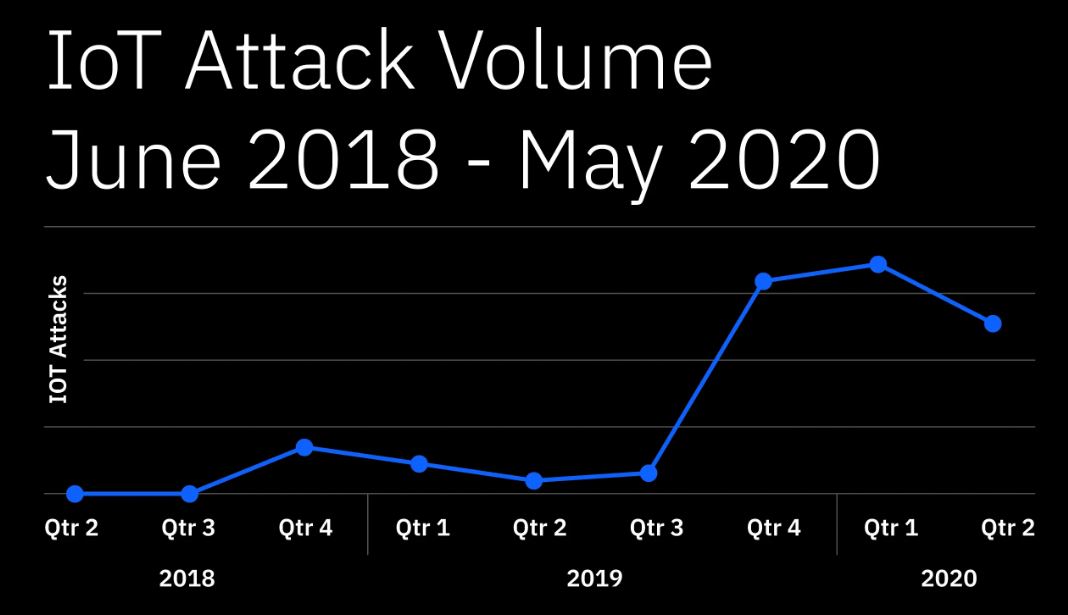
IBM experts examined the Mozi botnet, which is based on the Mirai and Gafgyt code. Researchers claim that this botnet generated 90% of all IoT traffic between October 2019 and June 2020. At the same time, the number of IoT attacks recorded during this time was 400% higher than the total number of IoT attacks over the past two years.
The researchers note that the significant increase in IoT attacks could also be attributed to the large number of IoT devices, which account about 31 billion worldwide.Analysts have been watching Mozi for four years and describe it as a P2P botnet based on the Distributed Hash Table (DHT) protocol, spread through exploits and weak passwords (via Telnet). Qihoo 360 Netlab researchers also followed it, and we already talked about the fact that Mozi botnet attacks Netgear, D-Link and Huawei routers.
The success of Mozi specialists explain by the fact that it exploits command injection and misconfigurations of IoT devices. Thus, almost all of the studied attacks began with command injection and wget, and then the malware changed the rights to facilitate interaction between hackers and the affected system.
The attacks mainly targeted the MIPS architecture: the mozi.a file was loaded and then launched on vulnerable devices.
For infecting devices Mozi exploits many different vulnerabilities: CVE-2017-17215 (Huawei HG532), CVE-2018-10561 and CVE-2018-10562 (GPON routers), CVE-2014-8361 (Realtek SDK), CVE-2008-4873 (Sepal SPBOARD), CVE-2016-6277 (Netgear R7000/R6400), CVE-2015-2051 (D-Link devices), command injection into Eir D1000 wireless routers, RCE without authentication in Netgear setup.cgi, command execution in MVPower DVR, DLink UPnP SOAP command execution, and RCE bug affecting several CCTV-DVR vendors.
Moreover, as mentioned above, for hacking credentials are brute-forced through Telnet according to previously prepared list.
The researchers write that they are increasingly concerned with hacker attacks on corporate IoT devices and reminded to change the default device settings.