The “I sent you an email from your account” scam employs fear tactics, falsely claiming full access to recipients’ email accounts and threatening to expose compromising videos. Scammers allege a trojan infection, promising remote control of computers and real-time surveillance.
The phishing email spreads through widespread distribution, aiming for financial gain. To counteract this threat, recipients are urged to ignore the message, label it as spam, and block the sender to fortify their defenses against potential future scams.
What Is “I sent you an email from your account” Email Scam?
The email with the subject “I sent you an email from your account” is part of a spam email campaign commonly known as a scam. Cybercriminals employ this tactic to threaten recipients by releasing compromising or humiliating videos unless their ransom demands are met. This scheme is widespread and comes in various iterations.
If you receive such an email, it is strongly advised to disregard it and not trust any claims made within the message. The email is disseminated through “email spoofing,” which involves falsifying the sender’s email address. This method allows the scammers to create an illusion that the recipient is also the email’s sender.
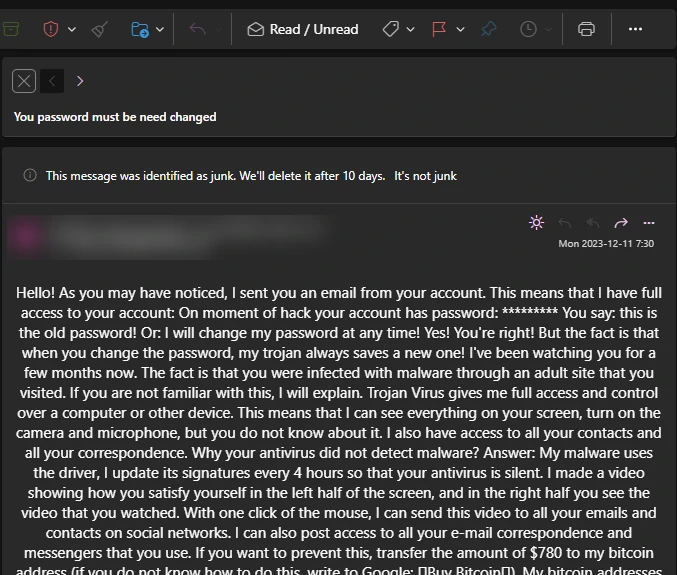
“I sent you an email from your account” Email
| Name | “I sent you an email from your account” Email Scam |
| Threat Type | Phishing, Scam, Social Engineering |
| Distribution methods | This scam is spread wide via spam email campaigns. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Similar Behavitor | “Some Bad News That You Are About To Hear” Email Scam, “Your Account Was Hacked” Email Scam |
| Fix Tool | See If Your System Has Been Affected by Your Account Was Hacked Virus |
How Does “I sent you an email from your account” Scam Work?
In this scam, cybercriminals assert that they have gained complete access to the recipient’s email account, having acquired the password. They claim that the recipient’s computer is infected with a trojan, allowing them to alter the password at will, rendering any user-generated changes ineffective. The trojan was introduced during the recipient’s visit to an adult website. Additionally, the scammers purport to have the capability to remotely control the recipient’s computer remotely, enabling real-time monitoring of activities, activation of the camera and microphone, and more.
The perpetrators behind this scam declare that they have recorded a compromising video at some point, threatening to distribute it to all of the recipient’s contacts unless a ransom of $780 in Bitcoins is transferred to a specified Bitcoin Wallet within 48 hours. Furthermore, they warn against sharing the ransom email with any other party under the threat of video proliferation. It is crucial to note that all claims regarding recorded videos, trojan infections, stolen data, etc., are entirely false. These scam emails are disseminated to a broad audience, hoping that some recipients will be deceived. Never trusting or acting upon such scams or their variations is imperative.
Is It Dangerous?
The email does not pose an immediate threat unless the recipient capitulates to its demands. The principal risk tied to this communication is financial loss. Additionally, there is a potential for an increase in similar scams targeting the individual, leveraging the success of the initial attempt by the scammers.
As reiterated earlier, our recommendation is to disregard the email. Furthermore, marking it as spam and blocking the sender serves as a protective measure, not only safeguarding the recipient but also contributing to the reinforcement of anti-spam filters. Proactively taking these measures may act as a deterrent, dissuading scammers from persistently targeting the individual’s email inbox.
How to Remove Malware from Your PC?
Although scammers’ claims are usually false, it’s better to be safe than sorry. We suggest scanning your device to ensure that there is no malware present. The most efficient way to do so is by using anti-malware software. I recommend GridinSoft Anti-Malware as it is a fast, lightweight, and effective security solution that can easily repel threats. You can try it out during a 6-day free trial period.
While it is possible to remove the threat manually, we do not recommend doing so. Malware tries to gain persistence by creating numerous instances of itself, making it nearly impossible to trace all the parts. Therefore, manual removals may take time and may not be entirely efficient. I have compiled the best removal practices for malware in the guide below.
Remove malware with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common malware as shown from our tests with the software, and we assure you that it can remove malware as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
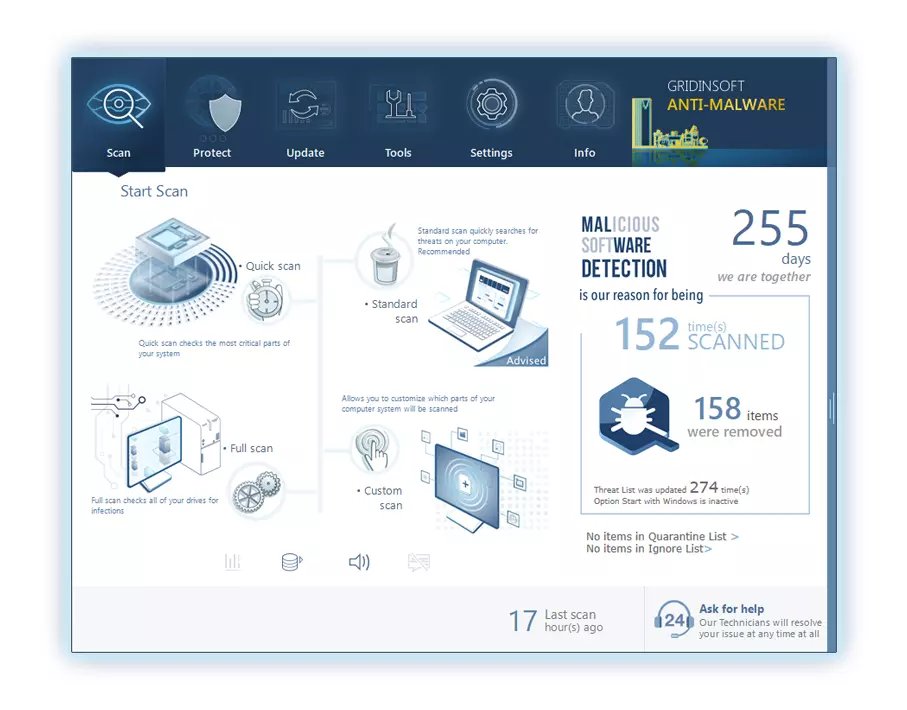
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
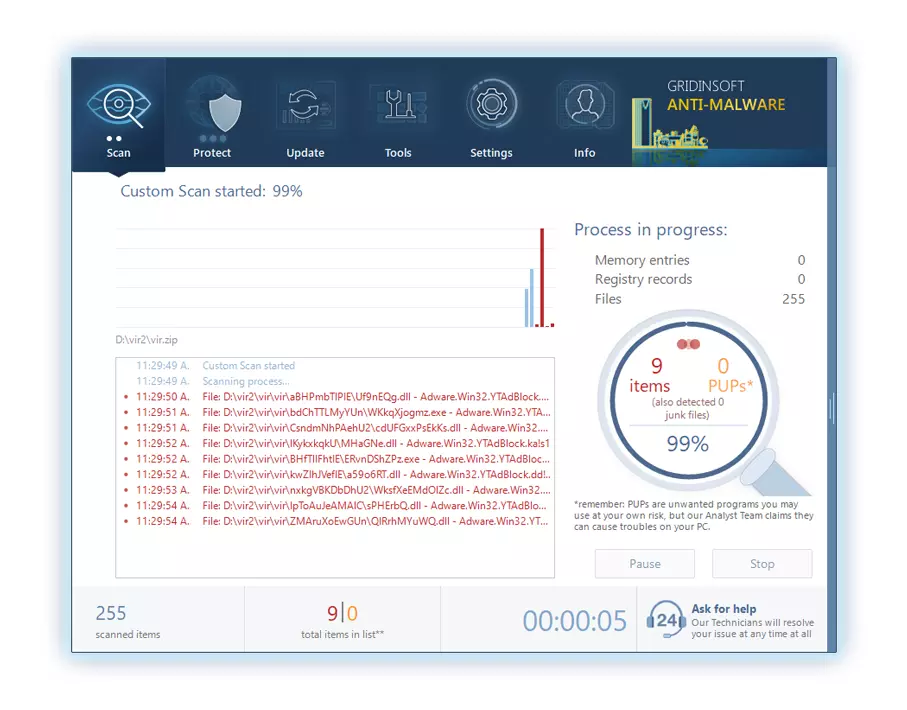
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
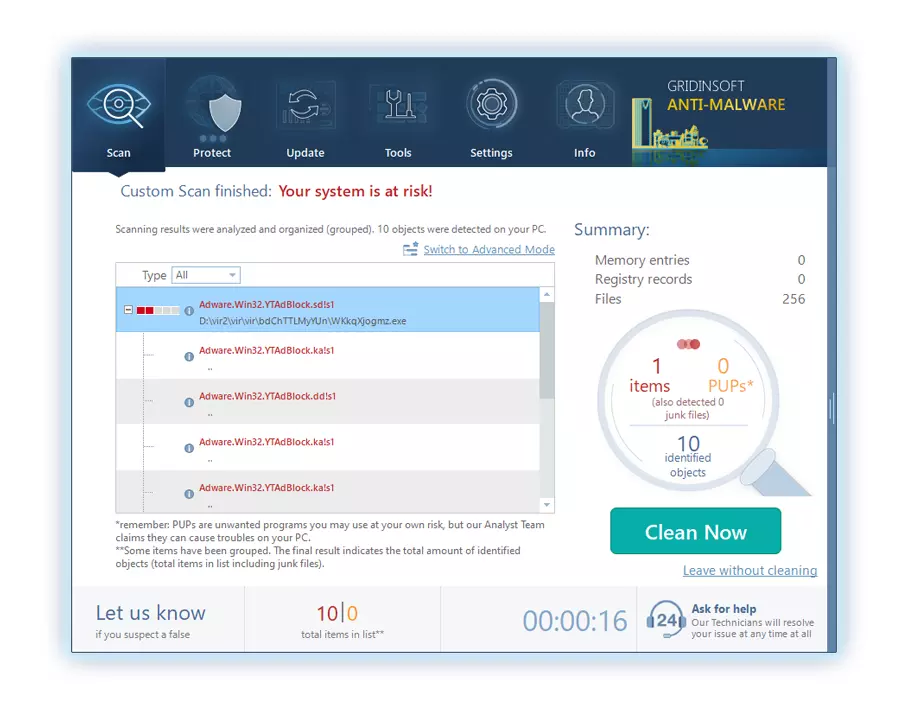
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
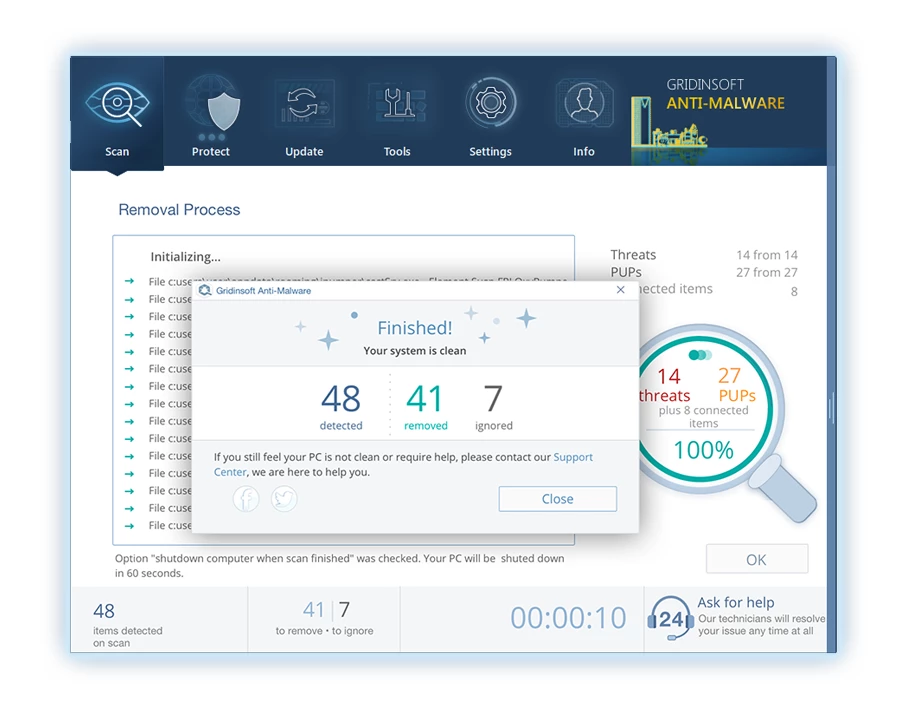
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “malware” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
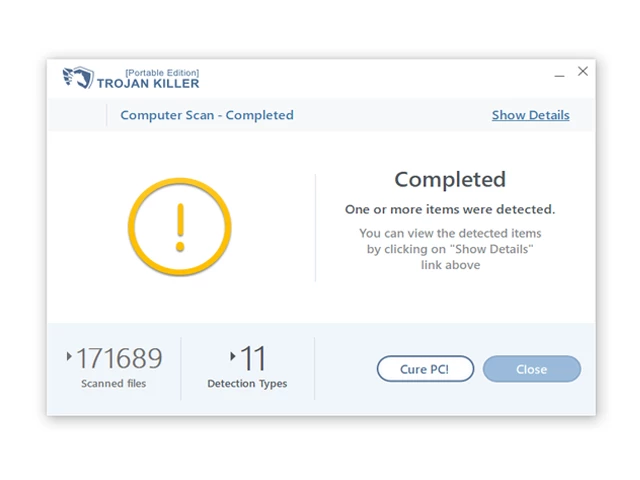
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
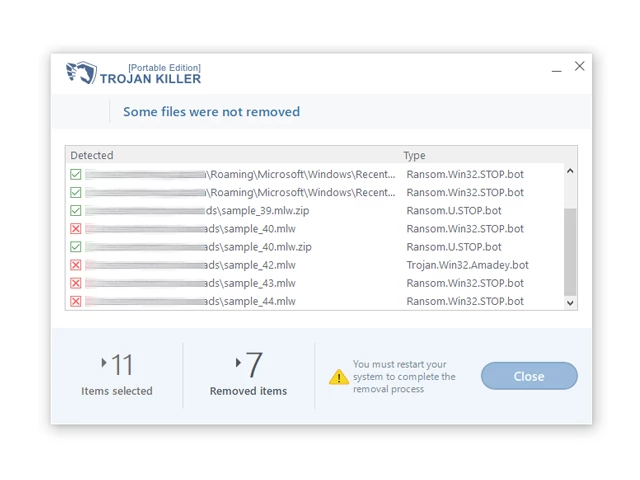
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing malware and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Frequently Asked Questions (FAQ)
The only risk of this email is financial loss and an increase in similar scams in the future.
The chance of threats being true is minimal. They are often scammers trying to fool naive users. Search for the scam text on Google – you will see info about thousands of same spam messages. There is no way someone can have that much compromising materials.
Ignore, or even delete in from the inbox. Never reply scam messages, regardless of their contents. By replying to a message, you confirm that your mailbox is valid. Even if the current scam is unsuccessful, the scammers will know that this address is “live” and try to pull off other schemes.
How to Remove "I sent you an email from your account" Email Scam
Name: I sent you an email from your account Email Scam
Description: The "I sent you an email from your account" scam employs fear tactics, falsely claiming full access to recipients' email accounts and threatening to expose compromising videos. Scammers allege a trojan infection, promising remote control of computers and real-time surveillance. The phishing email spreads through widespread distribution, aiming for financial gain. To counteract this threat, recipients are urged to ignore the message, label it as spam, and block the sender to fortify their defenses against potential future scams.
Operating System: Windows
Application Category: Malware

