Perhaps each of us at least once received an email with strange content. If you read this text, you are an Internet user and probably have an email account. Although email spam has existed since the inception of email, it is still considered the most effective means of cyberattack today. This article tells you what spam is, how to detect it, and advises on how not to avoid email scams.
What is spam?
Spam also known as junk email is an unwanted message usually sent out in bulk via email. Often these messages contain ads, phishing links, or malware. Scammers develop various misleading subject lines and content designed to trick users. Their main goal is to get the victim to click the link, or download attachments. In some cases, spam emails may look legitimate; they masquerade as emails from financial institutions, social media sites, or other well-known companies. This type of spam is better known as phishing and is one of its most common forms.
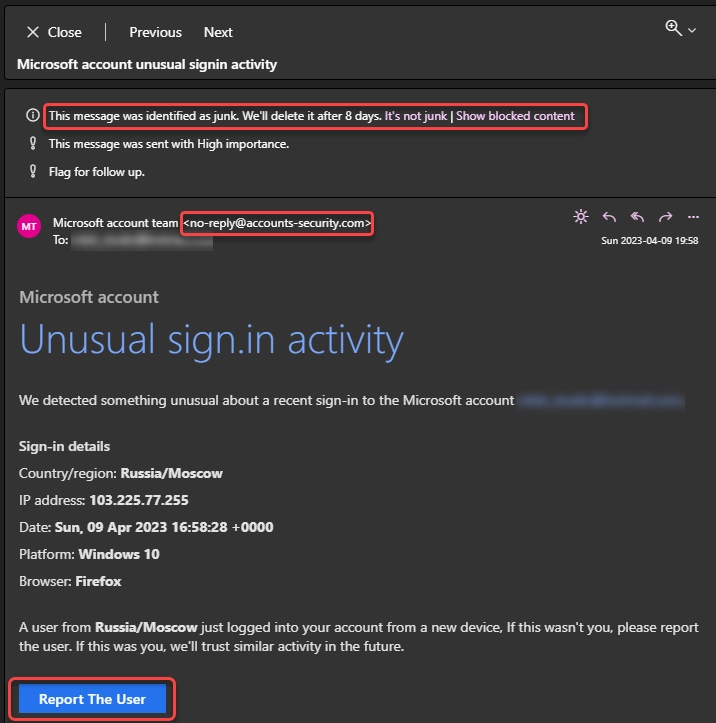
It is a classic example of spam. It has a fake sender address, a notice that it is spam, and a link button
Why is spam a problem?
At first glance, spam may seem harmless, but statistics say otherwise. Spam is a severe problem for both individuals and businesses. For example, it can be nasty and a waste of time for individuals. Furthermore, spam messages can clutter mailboxes, making finding and managing essential emails difficult. In addition, some spam messages can be dangerous because they contain viruses or links to malicious websites, which can harm your computer or steal your personal information.
In terms of business, spam can be even more problematic because it can cause serious harm to organizations. For example, it can reduce employee productivity by wasting time deleting unwanted messages and receiving large numbers of spam messages can overload mail servers. In addition, spam can contain malicious links and applications that can compromise an organization’s system security. This can all lead to leaks of confidential information, data loss, and even financial loss.
What spam is used for?
Phishing attacks try to steal personal information, such as credentials, online banking or credit card information, or other sensitive data. These scams often use social engineering techniques, such as urgency or fear tactics, to convince users to provide information. Once an attacker has this information, they can use it for identity theft, financial fraud, or other malicious purposes.
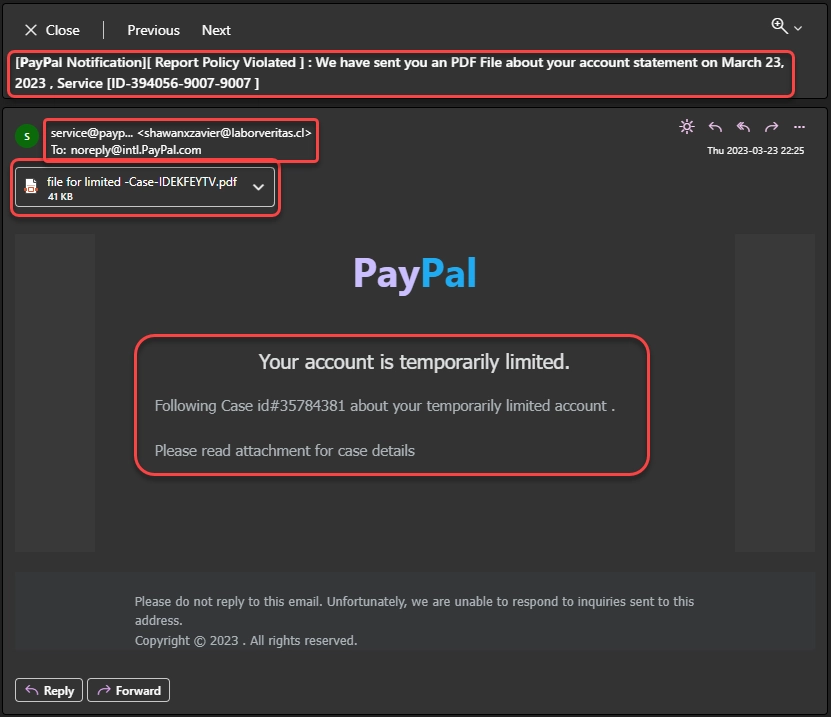
The email encourages the user to open the attachment
However, not all phishing attacks involve adding links to the message. Some of them suppose baiting you to share your personal information during the conversation. Topics in this case look less urgent, and suppose you to text the scammers back. Seeing activity from your email, fraudsters not only start chatting with you – they also mark your address as an active one. Most of crooks involved in this scheme use same databases of emails, and the marking “active” is like a red rag for a bull. So answering this, you’re risking not only with your personal data, but also with starting to receive dozens of other spam messages.
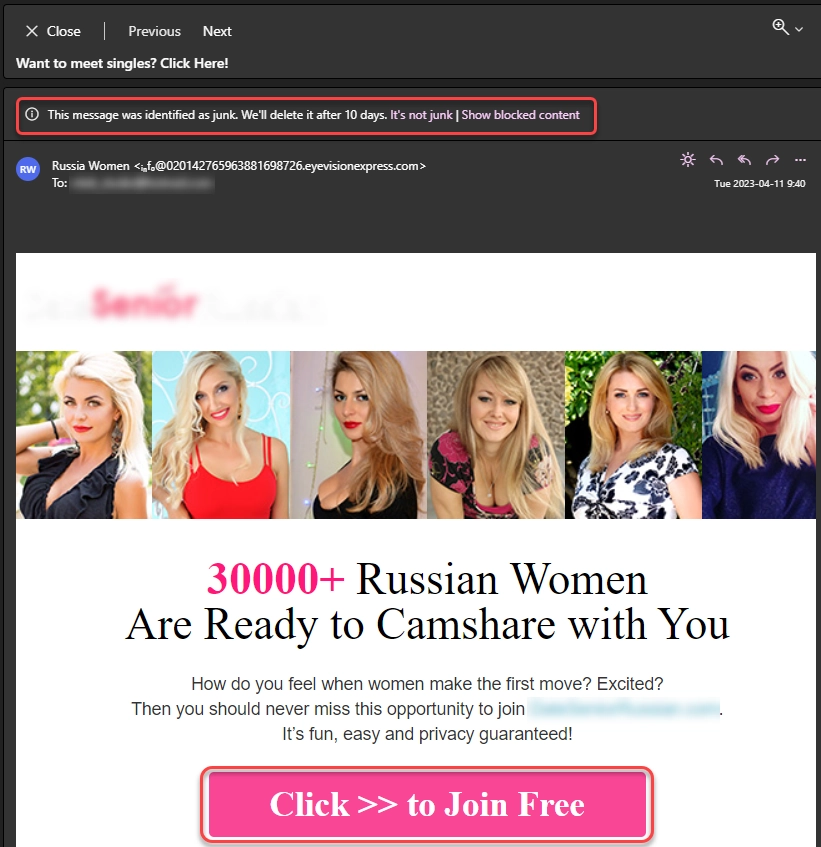
Another example of spam that is offering to click on a link
Malware spreading is another common application of spam. Scammers use spam to distribute malware through attachments or links to infected websites. Then, attackers can use this malware to steal sensitive data, such as credentials. Alternatively, they can gain access to a victim’s computer and use it to deploy a more severe infection, like ransomware.
Types of spam
Spam can come in many different forms. However, in addition to email spam, there are other forms of spam, which are listed below.
Social Media Spam
Social Media Spam is unwanted, massive, or automated postings or actions that negatively impact users’ social media experience. It can take many forms and manifest on various social media platforms such as LinkedIn, Facebook, Twitter, Instagram, and others. Examples of social media spam include:
- Unwanted comments: These are mass comments that contain links to advertising or malicious websites, promotion of products, services, or interactions for unwanted publicity.
- Fake accounts: Sometimes scammers create multiple fake accounts to mass subscribe to other accounts, like, repost, or comment. They usually do this for mass promotion or a negative impact on the community.
- Automated messages: These are automated messages or actions such as automatic friend requests, messages in pm, or comments to promote products, services, or interactions for mass promotion.
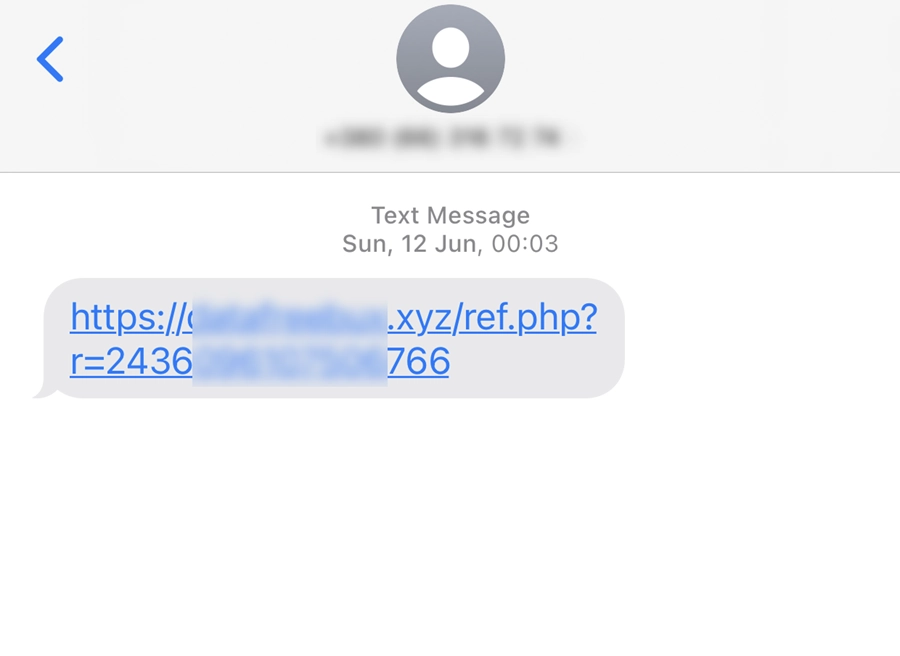
SMS spam
SMS spam is unsolicited text messages that arrive on cell phones without the recipients’ consent. Such announcements usually contain advertising offers, fraudulent schemes, links to malicious websites, and other unwanted content. SMS spam can be bulk messaging to many mobile numbers or sending automated messages using specialized programs or bots.
Messenger spam
Messenger spam is unwanted messages that spammers send out via messengers. Here everything is the same as in the previous paragraph. The only difference is that messengers such as WhatsApp, Telegram, Viber, and Facebook Messenger are the platform for sending messages.
Spam on forums and blogs
Spam on forums and blogs is unwanted messages that often have nothing to do with the topic. Instead, spammers post comments on public forums, communities, or blogs to spread advertising, malicious content, phishing, offensive or inappropriate content, or other forms of abuse. Spamming on forums and blogs can be automatic, using spam bots, which I will talk about in the next paragraph, or manual, where spammers post themselves.
Spam bots
Spam robots, known as spam bots, are automated programs that send mass messages on various online platforms. They work autonomously, can perform many tasks without human involvement, and can create accounts, post messages, and send out emails in large numbers. Spam bots use various methods and techniques, such as changing IP addresses, varying the text and structure of messages, using different types of spam content, etc., to avoid detection and blocking.
How do I detect spam?
There are several ways to identify spam messages. Here are some red flags that are clear signs of spam:
- Unfamiliar sender: If you receive a message with strange content from someone you don’t know or don’t recognize, it may be spam.
- Standard greeting: The message begins with a generic greeting, such as “Dear Customer” or “Hello, Friend,” instead of a name call, which is not typical of respectful companies.
- Misspelled words or bad grammar: Many spam messages are poorly written or contain misspelled words. It’s because English is often not the native language of scammers.
- Promises of money or prizes: Spam messages often promise cash or prizes in exchange for doing an action or providing personal information. (For example, the Nigerian Prince scam).
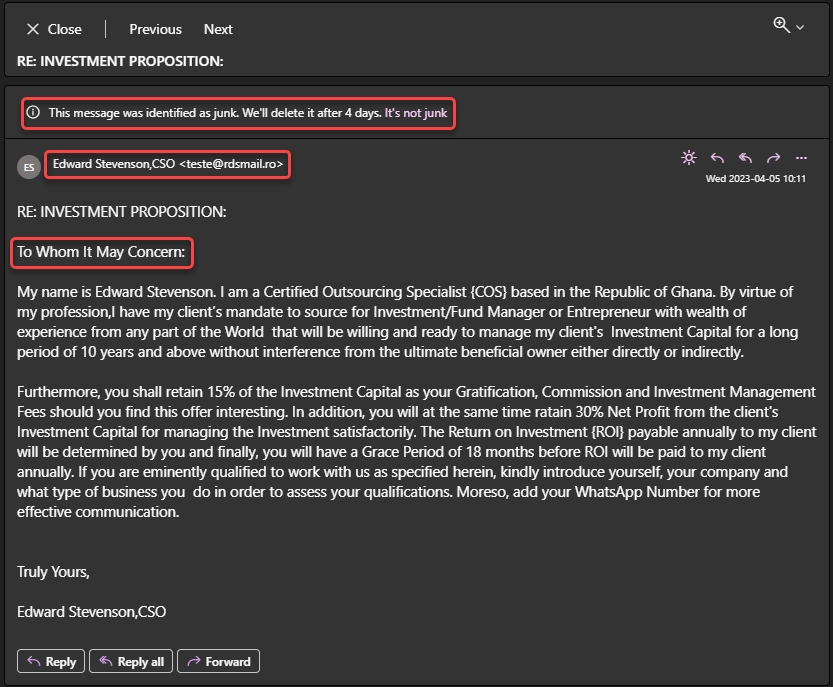
- Urgent or threatening tone: In some spam messages, scammers may use social engineering to get you to take immediate action.
- Suspicious links or attachments: Spam messages may contain suspicious links or attachments that lead to malicious websites.
How do I prevent spam?
Preventing spam can be difficult. However, here are a few steps you can take to minimize the risk of receiving spam messages:
- Use spam filters: Most email providers today have powerful AI-based filters that can help you weed out spam. Check your email settings and make sure filters are enabled and configured correctly.
- Avoid posting your email address publicly: To avoid getting your mailbox address into spam databases, avoid posting your email address on publicly available sites or forums. If you can’t avoid posting, use an alternate address that you don’t use for personal correspondence.
- Don’t reply to spam emails: If you reply to a spam email, you will confirm that your address is valid. This will be a signal to scammers that they can send more spam.
- Don’t sign up for suspicious mailing lists: Do not sign up for questionable mailing lists or enter your email address on unknown sites. Very often, such services sell email databases or become victims of data leakage.
- Use a separate email address to sign up for sites: You can create a different email address that you will use only to register for sites. Then, if you start getting spam at this address, you can easily replace it with a new one.
- Be careful when registering on sites: Carefully read the terms of use and refuse to receive advertisements and newsletters if unsure of the site’s reliability.
User Review
( votes) ![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian