Last weekend, hackers successfully attacked and defaced the website of the Ministry of Construction, Housing and Communal Services of Russia.
The hackers defaced the resource, changed the site’s title to a slogan with a Ukrainian greeting, and left a message on the main page saying that the site had been hacked by the DumpForums[.]com group.
Let me remind you that we also wrote that NB65 group attacks Russia with the modified Conti ransomware, and also that Hackers Attack Russian Defense Contractor Through MHTML Bug.
In the note, the attackers demanded to pay a ransom of 0.5 bitcoin until June 7, 2022, otherwise threatening to publish the data of the ministry’s employees in the public domain.
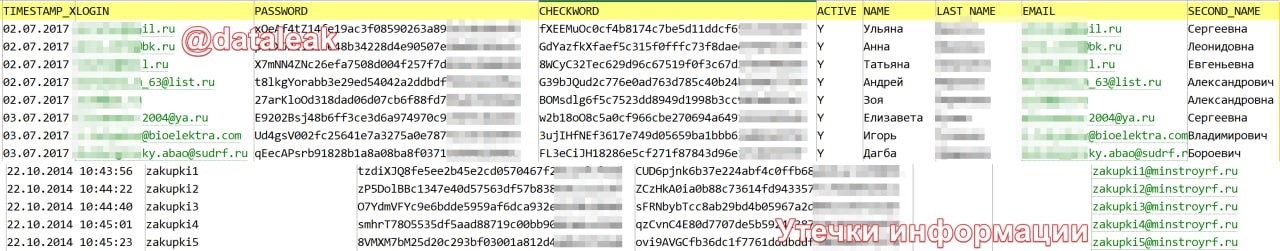
According to Data Leakage & Breach Intelligence (DLBI) specialists, the data of registered users from the hacked Bitrix CMS was “leaked”. As evidence, the hacker provided a file containing 115,993 lines, including full name, logins, email addresses, hashed passwords (MD5 with salt) and registration dates from 08/14/2014 to 05/08/2022.
At the same time, representatives of the ministry told the media that nothing threatens user data and that they are protected.
Information security specialists noticed that a table of internal accounts of Rostelecom was published on the darknet. The company confirmed the fact of leakage of data from internal accounts, and assured that the possibility of external penetration into the infrastructure is excluded.
Yesterday, Data Leakage & Breach Intelligence (DLBI) specialists reported that the same source that recently distributed dumps of the Skolkovo School of Management, the Yakut portal Ykt.Ru, and the Delivery Club delivery service, published a table of Rostelecom’s internal accounts on the darknet.
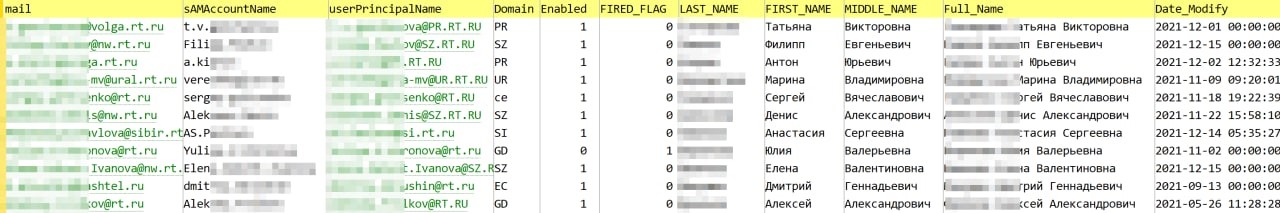
The dump includes 109,300 lines, which contain: full name, email addresses in the rt.tu domain and subdomains, position data, phone numbers (work and mobile), login and domain, record creation date (from 19.01.2021 to 15.12 .2021), signs of a dismissed and active employee.
Rostelecom representatives reported that the company is already conducting an audit on the fact of leakage of data from internal accounts, and the possibility of external penetration into the infrastructure is excluded.
