Information security experts have warned that a hacked version of the red team tool Brute Ratel is being distributed on Russian-speaking and English-speaking hacker forums. If Chitan Nayak, the creator of the toolkit, used to claim that if abuse was detected, he could identify the violator and revoke the license, now this will no longer work.

Chitan Nayak
Let me remind you that the first abuses of the Brute Ratel Command and Control Center (Brute Ratel C4 or BRc4) were discovered in the summer of 2022 and later were used by Russian hackers. Since BRc4 is largely focused on evading detection by EDR and antivirus solutions, almost all security products do not detect malware in it. Because of this feature, the researchers called the Brute Ratel “uniquely dangerous.”
Brute Ratel currently costs $2,500 per user for an annual license, and customers are required to provide a work email address and pass verification before obtaining a license. Since the verification is performed manually (although it is not known exactly how), in the summer of 2022, the question arose before the experts, how did the attackers even get a license?
Then Chitan Nayak told Bleeping Computer reporters that the license was leaked by a disgruntled employee of one of his clients. The developer assured that the payloads allow him to see who they belong to, so he was able to identify and promptly revoke the license.
However, even then it was reported that the abuse of Brute Ratel was not an isolated case.
According to information security experts, the Conti ransomware operators generally acquired Brute Ratel licenses, creating special shell American companies for this purpose.
Apparently, now hackers will no longer have to resort to such tricks. The fact is that information security expert Will Thomas, known under the nickname BushidoToken, found that a hacked copy of Brute Ratel (version 1.2.2) has already been circulating among attackers on hacker forums since mid-September.
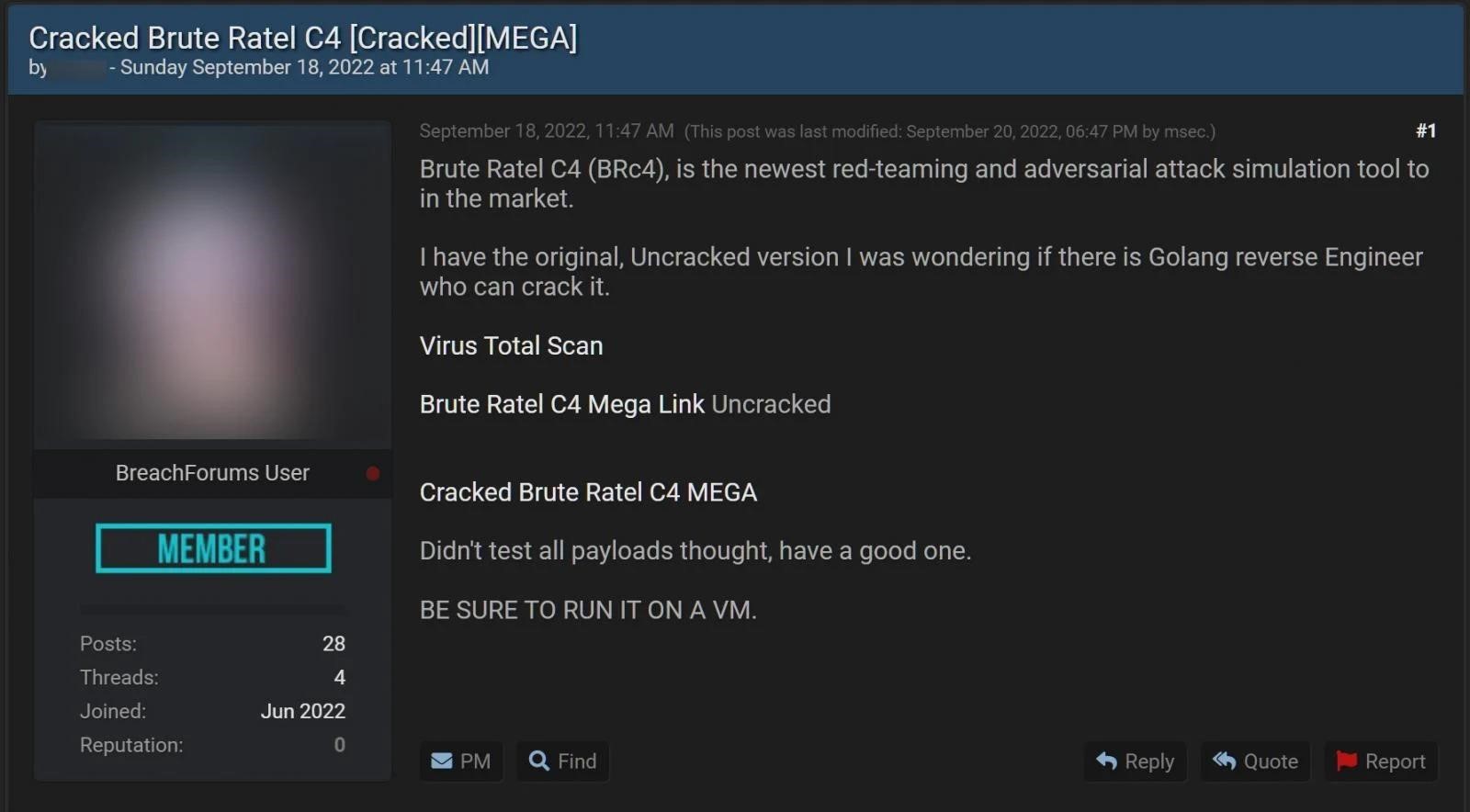
Thomas writes that this version of Brute Ratel does not require a license key to be entered at all, and does not look counterfeit to him or his colleagues at Curated Intel. According to the expert, attackers are already actively sharing screenshots with each other, which show how they are testing the toolkit.
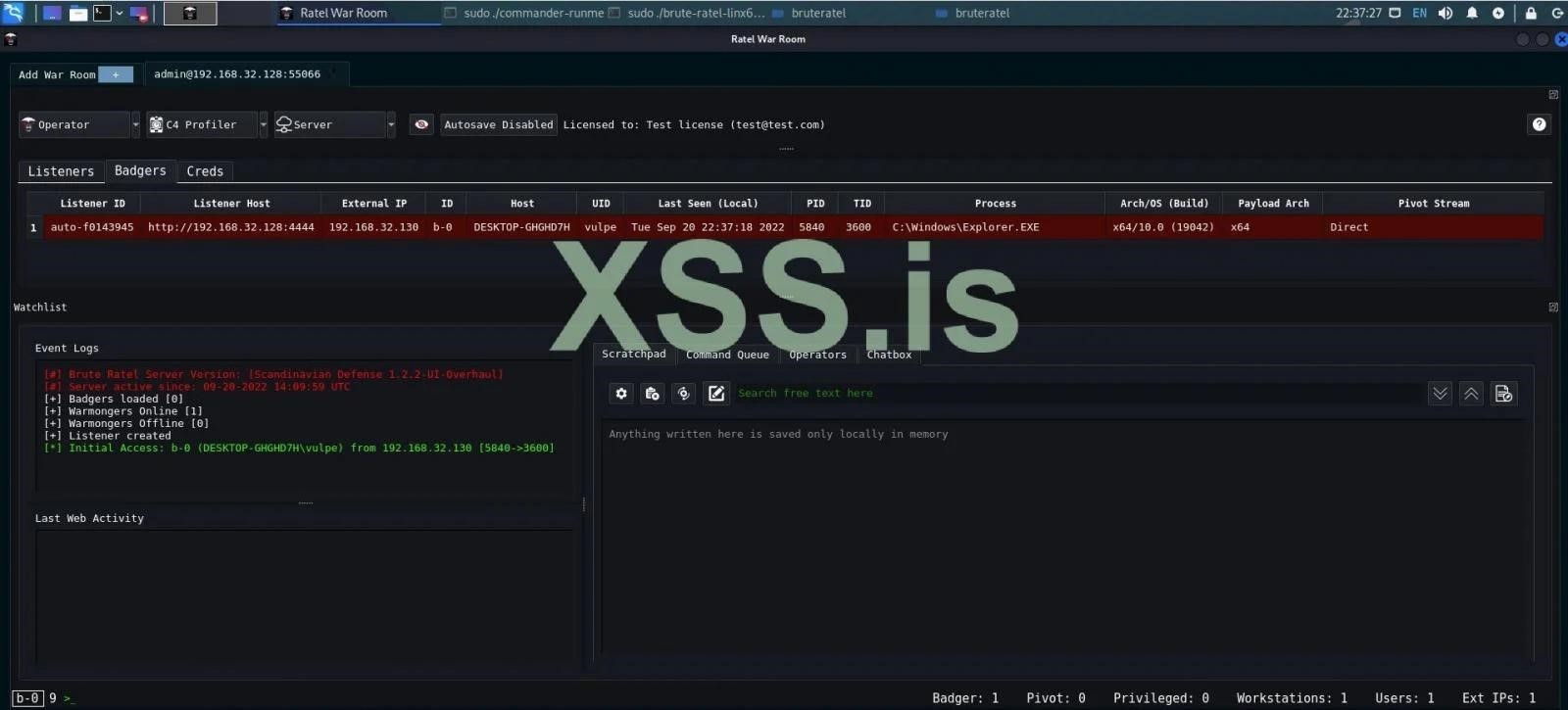
Chitan Nyak confirmed to reporters that an unhacked version of the toolkit was previously uploaded to VirusTotal, which was then hacked by the Russian-speaking hacker group Molecules to remove the license check.
Alas, this means that in the near future more attackers will start using the Brute Ratel instead of or along with the Cobalt Strike. At the same time, Will Thomas emphasizes that the toolkit is able to generate shellcode, which is currently extremely poorly detected by security solutions.
