Student Javier Yuste from the King Juan Carlos University of Madrid has created a free decryptor for the Avaddon ransomware – AvaddonDecrypter.
However, this solution was not universal – it could only help new victims of the malware and only worked if the victims did not turn off their computers after the attack.For example, AvaddonDecrypter dumped the infected system’s RAM and scanned the contents of the memory for data that could be used to restore the original encryption key. If the key could be recreated, free file decryption became available.
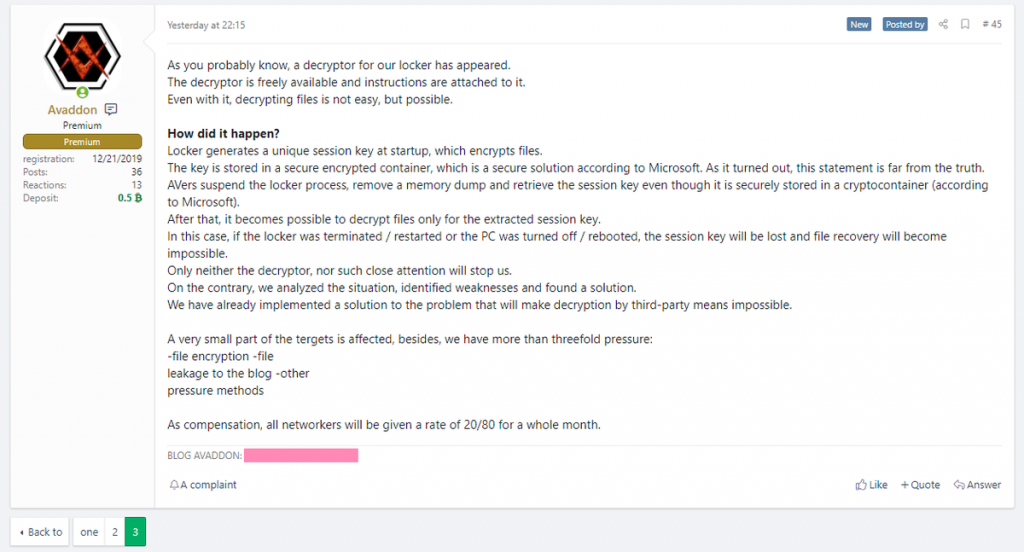
Unfortunately, the malware developers quickly noticed the release of Avaddon Decrypter. In the middle of this week, the attackers reported that they had updated their ransomware code so that Avaddon Decrypter would stop working.
The cybercriminals’ prompt reaction gave a new round to the long-standing dispute that information security specialists have been waging for a long time.
For example, some experts are convinced that decryptors that exploit various errors in the malware code should remain confidential and disseminate among victims only through closed channels. In case if such tools should still be made public, their publication should not be accompanied by any technical details and data that would tell attackers how best to fix their own code.
For example, specialists from MalwareHunterTeam accompanied the decryption by Javier Yuste with the following caustic comment.
If the decryptor is based on master decryption keys obtained from hackers’ servers, it can be published in the public domain, since criminals cannot do anything with such tools.
Let me also remind you that recently creator of the Ziggy ransomware reported that the malware stopped working. And he has published keys to recover encrypted files from victims.