ESET has announced the discovery of a new Crutch malware, the authorship of which is attributed to the hack group Turla. According to researchers, the malware is not completely new and has been used by hackers since 2015.
Crutch was found on the Foreign Ministry’s network in an unnamed EU country, and experts believe that this malware is only used against specific targets, which is typical for many Turla tools.Apparently, Crutch was created specifically to collect and steal confidential documents and other files that could be of interest to hackers. The malware uploaded the stolen information to Dropbox using accounts controlled by the hacker group.
Crutch is attributed to the Turla hack group due to its similarity to the Gazer (aka WhiteBear) backdoor, which was used by cybercriminals between 2016 and 2017. So, experts found that hackers used the same RC4 key to decrypt payloads, identical file names, almost identical PDB paths, and so on.
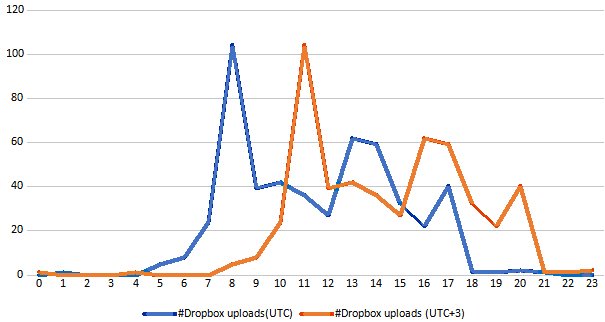
In addition, based on the timestamps of 500 ZIP archives that contained the stolen documents and were uploaded by Dropbox between October 2018 and July 2019, experts found that the hackers’ working hours correspond to the UTC +3 time zone, which is in Russia.
ESET’s report states that Turla used Crutch as a second stage backdoor, i.e. it used it on already compromised machines, after the first stage implants such as Skipper. And in some cases, Crutch was used months after the initial hack.
Earlier versions of the malware reportedly linked to a hardcoded Dropbox account using the official HTTP API to fetch commands and download results, but the newer version (Crutch v4) can automatically download files found on local and removable drives using Wget for Windows.
Let me also remind you about njRAT trojan that installed malicious npm packages on infected machines.