The researchers had at their disposal a PowerShell script used by the operators of the ransomware Pysa, and the experts were able to assess what data hackers are interested in and are trying to steal during attacks.
Typically, ransomware operators infiltrate the target network and start with limited access to one device. They then use various tools and exploits to steal other credentials used in the Windows domain or gain elevated privileges.After gaining access to a Windows domain controller, they search for and steal various information from the victim’s network before encrypting the devices.
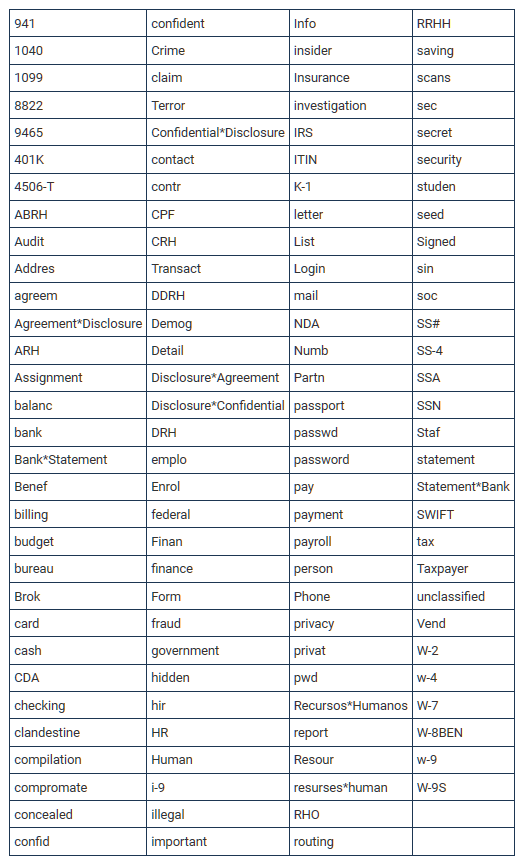
Bleeping Computer journalists write that the other day MalwareHunterTeam specialists shared with them a script that the Pysa ransomware operators use to find and steal data from the attacked server.
The script is designed to scan each drive looking for data folders that match specific strings. If the folder matches the search criteria, the script will upload the files to a remote server controlled by the attackers.
As can be expected, the script looks for files associated with a company’s financial or personal information, including audit and banking information, credentials, tax forms, social security numbers, and SEC documents. It also searches for other keywords, including crime, investigation, fraud, bureau, federal, hidden, secret, illegal, terror (terror). The complete list can be seen below.
The publication reminds that recently a disgruntled partner of the group shed light on the work of another ransomware, Conti. The docs tell you how to access someone else’s network, side-move, expand access, and then steal data before encrypting it.
After gaining control of a Windows domain controller, the grouping partners were prompted to search for the following keywords, according to his published data:
- Cyber;
- Policy;
- Insurance;
- Endorsement;
- Supplementary;
- Underwriting;
- Terms;
- Bank;
- 2020;
- 2021;
- Statement.
Let me remind you that we talked about the fact that Conti ransomware attacks Ireland’s Health Service Executive.
