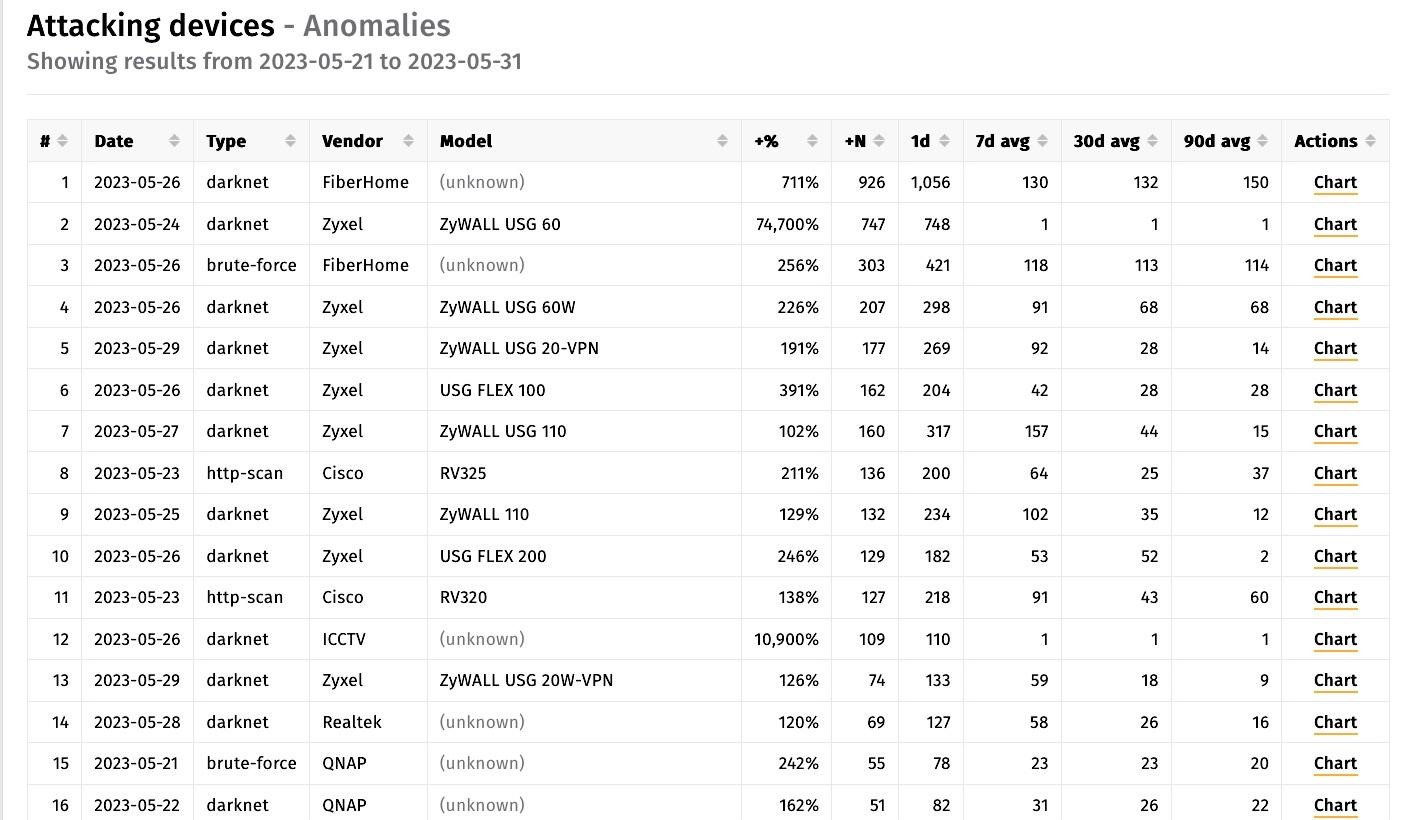
Experts have warned that hackers already exploit the critical vulnerability CVE-2023-28771 in Zyxel firewalls. In particular, the Mirai botnet is actively using the fresh bug.
Let me remind you that TRAPA Security specialists discovered the problem that received a rating of 9.8 points out of 10 possible on the CVSS vulnerability rating scale.Let me remind you that we also wrote that Zyxel Patches Critical Vulnerabilities in Its Firewalls and VPNs, and also that Hackers Attacked Critical Vulnerability in Zyxel Firewalls.
And also the media reported that Mirai Botnet Comes with new 11 Exploits to Attack Enterprise Devices by Zyxel.
The bug, fixed at the end of April, was related to incorrect handling of error messages in some versions of the firewall and allowed an unauthenticated attacker to “remotely execute commands by sending custom packets to a vulnerable device.”
The problem affected:
- ATP (ZLD V4.60 to V5.35, fixed in ZLD V5.36);
- USG FLEX (ZLD V4.60 to V5.35, fixed in ZLD V5.36);
- VPN (ZLD V4.60 to V5.35, fixed in ZLD V5.36);
- ZyWALL/USG (ZLD V4.60 to V4.73, fixed in ZLD V4.73 Patch 1).
As specialists from the US Infrastructure and Cyber Security Agency (CISA) have now warned, a fresh problem is already being used by hackers with might and main.
Information security specialists from Rapid7, Shadowserver, and well-known specialist Kevin Beaumont revealed information about these attacks.
For example, one of the malware clusters that uses CVE-2023-28771 is a Mirai-based malware that launched its attacks on May 26, 2023.
Such malware is usually used to launch DDoS attacks, but it can also perform other tasks.
The researchers note that the attacks use a publicly available PoC exploit for this vulnerability.
Shadowserver experts warn device owners that any vulnerable device that has not yet received patches should be considered compromised. The fact is that, according to Shadowserver data collected over the past 10 days, 25 of the 62 most active “downward attacks” (that is, attempts to hack into other devices connected to the Internet) came from the IP addresses of Zyxel devices.