According to CyCraft, a Taiwanese security company, the Chinese hack group APT10 (aka Stone Panda, MenuPass and Bronze Riverside) has been attacking the local financial sector for many months, exploiting a vulnerability in an unnamed security product that is used by about 80% of local financial institutions.
It is believed that the attacks began at the end of November 2021 and are still ongoing.The name of the product being exploited by the hackers has not yet been revealed due to an ongoing investigation by law enforcement agencies, as well as attempts by specialists to release and distribute patches to local financial institutions.
The attacks went unnoticed for so long as they were initially misclassified. The fact is that IN November 2021 attacks hackers used a vulnerability in the software that was missed, but the use of credential stuffing tactics was noticed, which APT10 used as a cover and as a way to gain access to some trading accounts, which were then used to carry out large transactions in the stock market.
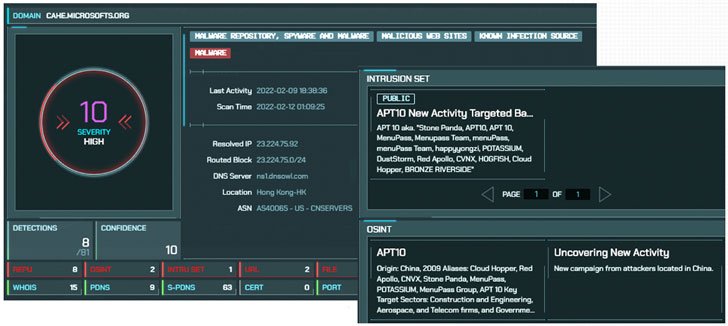
Now the researchers say that it was all just a “screen”. In fact, APT10 exploited a vulnerability in an unnamed security product, injected the ASPXCSharp web shell, and then used the Impacket tool to scan the target’s internal network. After that, the attackers used the reflective code loading technique to run malicious code on local systems and install Quasar RAT open-source malware, which allowed hackers to gain remote access to the infected system using RDP reverse tunnels.
Let me remind you that we also wrote that Chinese hackers attacked Ragnarok Online Developers, and also that DeadRinger attack targets telecommunications companies in Southeast Asia.
