Afghanistan became the main target for ransomware attacks around the world in the past month, according to analysis of data from the Atlas VPN group.
The recent seizure of power in Afghanistan by the Taliban has brought chaos to the country. This attracted the attention of various cybercriminals like bees to honey – the mess is an ideal environment to get rich. Ensuring the safety of employees and clients of various companies will be extremely difficult on the territory under Taliban rule.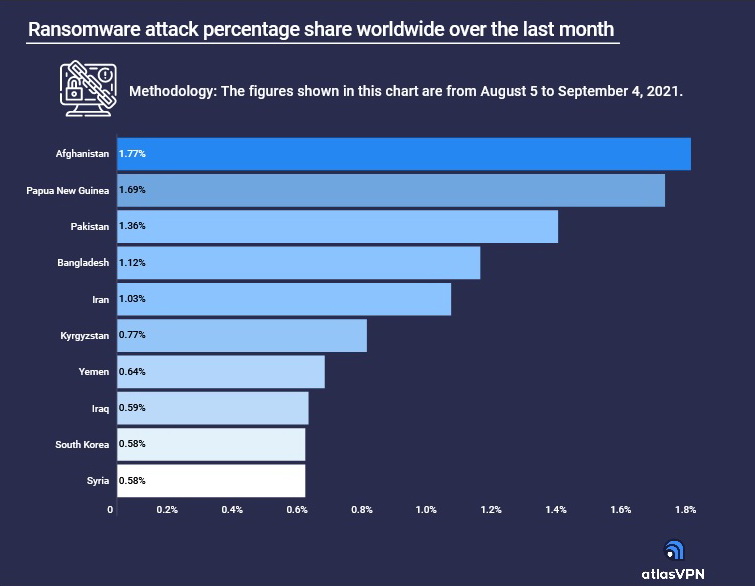
The data is based on the Kaspersky Cyberthreat Map, which collects worldwide statistics on various cyberattacks. The numbers analysed in this report refer to the period from August 5 to September 4, 2021.
Over the past 30 days, cybercriminals have carried out 1.77% of all ransomware attacks in Afghanistan.
The hackers noted that business in the country is now very vulnerable. Many professionals are unable to return to work or have left Afghanistan with the US military. The Taliban advance made it difficult for local small companies to operate due to constant supply chain and transportation disruptions.
Most ransomware works in a similar way, encrypting user information and requesting a ransom to unblock it. However, hackers prefer to use different types of malware depending on their technical level and what kind of business or person they are targeting.
Atlas VPN also compiled a rating of malware that is now involved in attacks on Afghanistan and other countries.
- The malware Trojan-Ransom.Win32.Wanna.m was used in 14.64% of ransomware attacks in the past month, making it the most popular. This family belongs to the WannaCry type of malware that encrypts user files. It spreads by exploiting a vulnerability in the Server Message Block (SMB) protocol.
- Next comes the ransomware Trojan-ransom.win32.Crypmodadv.gen, which hackers used in 9.79% of attacks. Once the Trojan is introduced, it will encrypt the victim’s computer by placing a ransom note with the requested amount. It is usually spread through phishing emails or hidden in malware.
- Next comes the ransomware Trojan-Ransom.WIN32.Phny.a, which was used by 9.32% of cybercriminals. The infection encrypts documents on the victim’s hard drive and blocks access to the computer until the person pays the ransom.
- Finally, we have Trojan-Ransom.win32.Crypren.gen and Trojan-Ransom.Win32.Wanna.zbu malware, which were used in 5.64% and 5.13% of ransomware attacks, respectively.
Let me remind you that we also talked about the fact that DeadRinger attack targets telecommunications companies in Southeast Asia.
