Windows 11 brought a huge pack of updates, including performance boosting and interface changes. But as often happens in software development, the vast majority of changes remain unspoken and unseen. This time, that happened with security updates in Windows 11.
Security features in Windows 11
In my overall review on Windows 11, I have mentioned the updated Microsoft Defender1. As it was said in that article, it became less vulnerable and much more power-efficient. However, those changes are not even a quarter of all things that happened with Defender in this update.
New look of Microsoft Defender
Microsoft changed their system security paradigm to “Zero Trust”. Earlier, system security mechanisms were trying to secure the system from external malware, assuming that programs installed by users are not malicious. In Windows 11 (and in Windows 10 21H2 as well), Defender brings much harder heuristic and behavior analysis than ones that were used before.2
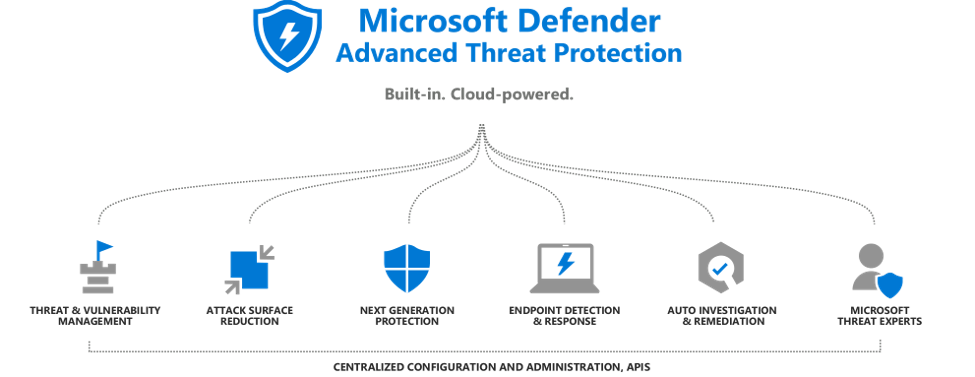
Attack Surface Reduction
New mechanisms in Microsoft Defender are generally aimed at corporate networks but can be implemented on the individual system. First notable element is Attack surface reduction3. That feature allows much more harsh control over the potentially dangerous elements. In that case, the Defender pays additional attention to the programs which try to connect to the undefined server and download something. Microsoft antivirus checks with extreme precision are programs, that were never used before in the certain corporate network, and obfuscated scripts.
Those improvements are the retaliatory step from Microsoft, made to give the threats no chance at all. Instead of chasing the separate vulnerabilities4, they decided to prevent the launch of malicious code at its start. It will be effective but does not cancel the importance of vulnerability patching.
Network security
Some of the modern attacks are executed through malicious landing pages that use exploits to inject malware. Earlier, the Microsoft anti-malware solution used the standard method of network monitoring. It was effective against known malicious or phishing sites, but useless for preventing the 0-day attacks.
Updated security features allow the Defender to check the website activity in the sandbox, before allowing the user to interact with it. Of course, such actions will be done only with untrustworthy pages – ones that use compromised or dubious domains, use the unsecure connection or so. Currently, fraudsters cannot distinguish the sandbox from a real system, so such protection is very effective.
Controlled Folder protection
Creating a safe space inside of the system, which will be accessible only by the user or the defined programs, was circulating in the cybersecurity world for the last several years. Some cybersecurity vendors offer their solutions for a broad market, but those products aim at corporations and cost a lot.

Microsoft specified the need for the TPM 2.0 module not just to make the list of supported CPUs smaller. Exactly, the Controlled Folder feature is needed to make a safe zone inside of the file system. This area can be accessed and edited only by the user who created it, and also by the allowed programs. In that folder, you can keep important data of any sort, and it will be invulnerable to any malware – ransomware, spyware, stealers, or others.
New functionality for Endpoints in Windows 11
Besides the global improvements, Microsoft also published the Microsoft Defender for Endpoint (MDFE). That feature consists of specific facilities that allow the enterprise security team to trace, detect and remove the threats. Microsoft offers cloud storage to provide the full picture of any cybersecurity incident, where the logs are kept. On that cloud, the data is analyzed by AI-based mechanisms that are studied on the enormously big base of different threats. MDFE promises to become a perfect solution for corporate security – if it will work as they claim, of course.
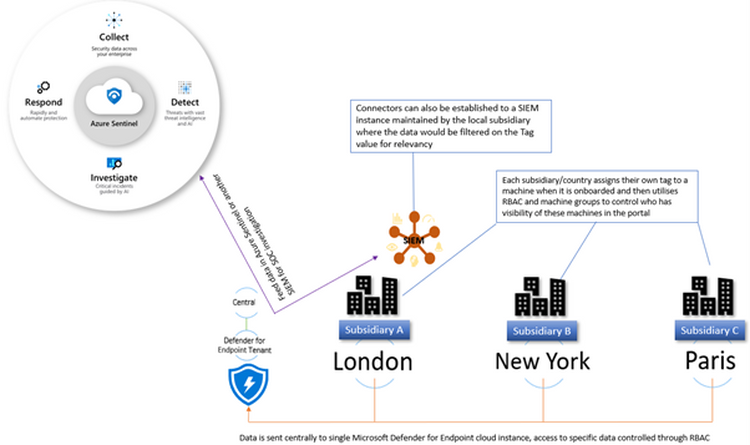
Windows Defender for Endpoint. That’s how it works.
Application control in Windows 11
Exploiting the vulnerabilities in various applications or protocols is one of the most widespread ways of malware injection. Windows Defender Application Control (WDAC) – the new submodule of the Defender – is called to put it down. As was mentioned, previously, the security system in Windows assumed that the code of applications that run on a user’s PC is trustworthy. Now, the WDAC will scan the applications for possible malicious code circulating inside. That step indeed cuts the ability of exploitation – even if someone succeeds in malware injection through the exploit, the attack will be stopped by the Defender.
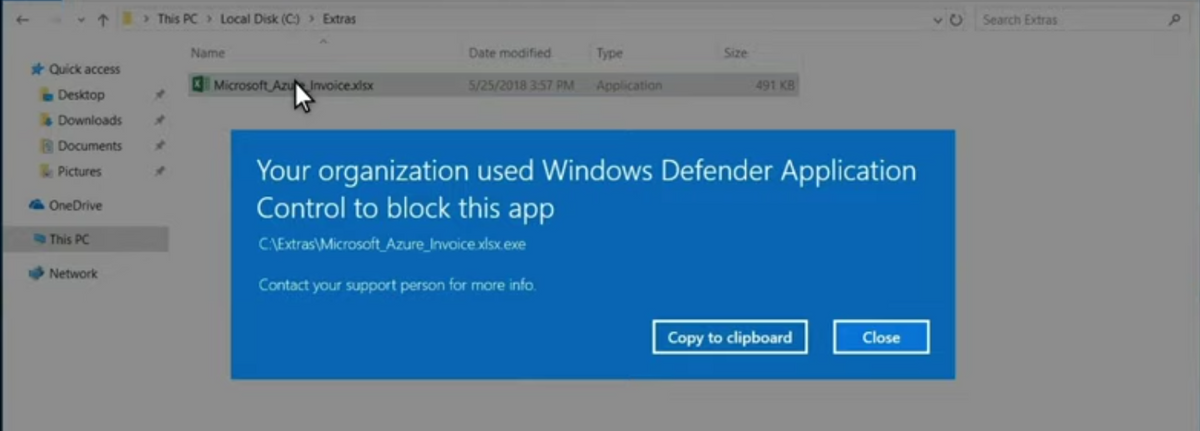
Notification from Windows Defender Applicaiton Controle (WDAC)
Even though these steps are pretty harsh and may inflate the performance, they are pretty effective. Nonetheless, Microsoft also published another tool for application controlling – AppLocker. That thing may be used both instead of and complementary to WDAC. It will be very useful in inconvenient situations – for example, when you sometimes need to escalate the privileges for the app. WDAC will likely block this attempt, assuming that it may be a malicious code execution. AppLocker allows users to select the apps that must have exclusions for some actions.
Windows Defender Application Guard
This part of an updated Defender is named similar to the WDAC, but their functions have much more differences than abbreviations. WDAG creates a shell around the program, which allows it to check for possible malicious elements in the code. It is a sort of a sandbox – but with another purpose, and with the maximum virtualization. A lot of viruses can distinguish the normal sandboxes (or other testing environments) from a real system. The WDAG creates not just an irresistible shell – it also makes everything for apps to think that they are launching in a normal system.
Currently, Application Guard protects:
Microsoft also offers the AppContainer – a specific environment for program execution. It acts like a sandbox – an area that allows it to execute the program’s code without giving it the ability to interact with the system and other PC components. It is quite similar to the functionality that is offered by Docker – a widely-used containerization tool. It is very useful for app developers because previously they were forced to use Docker through the WSL, dual-boot, or even a virtual machine.
User Review
( votes)References
- Testing the Microsoft Defender in real world.
- Detailed report on the alterations to Windows security facilities.
- Read more detailed information about this technology on the Microsoft site.
- Microsoft products lead among all other programs for the number of vulnerabilities.


Muy buen trabajo la verdad que los sistemas operativos de windows tienen muchos puntos débiles no soy experto pero tengo que tener la computadora dentro de una caja fuerte,cada semana intentos y ataques por muchos sitios y maneras, las personas particulares o no saben nada o algo de todos los factores,de invasión de tus datos o de el daño que pueden hacer por eso de que haces un muy buen trabajo, para que las personas de calle estemos un poco mas informadas,muchas gracias por tus servicios y información, un saludo.