Earlier this week, Microsoft issued a warning about a new zero-day vulnerability in Windows MSHTML (aka Trident), the proprietary Internet Explorer browser engine.
It has been reported that the issue is already being exploited in real attacks against Office 365 and Office 2019 users on Windows 10, but there is no patch for it yet.The vulnerability was identified as CVE-2021-40444 and affects Windows Server 2008-2019 and Windows 8.1-10 (8.8 out of 10 on the CVSS scale). Although MHTML was primarily used for the Internet Explorer browser, it is also used in Office applications to render web-based content within Word, Excel, and PowerPoint documents.
As Microsoft representatives explained, using this bug, an attacker can create a malicious ActiveX component that will be used by a Microsoft Office document and processed by MHTML. In fact, the attacker only has to convince the user to open such a malicious file, after which the attack can be considered a success.
At the same time, it was reported that you can protect against attacks if Microsoft Office works with the default configuration and documents are opened through Protected View or Application Guard for Office 365. Thus, Protected View is a read-only mode in which most editing functions are disabled, and Application Guard isolates untrusted documents, preventing them from accessing corporate resources, the intranet, and other files on the system.
As CERT/CC analyst Will Dormann has told Bleeping Computer reporters, the danger is still there and it’s all about Mark of the Web (MoTW), that is, the mark that documents receive from the Internet. If this checkbox is present, Protected View will trigger and Office will open the document in read-only mode, effectively blocking the exploit (unless the user allows editing himself).
Dormann warns that users often ignore such warnings, and worse, there are many situations where a document does not receive a MoTW tag at all.
Likewise, if the document is in a container such as an ISO file, a Windows user can simply double-click the ISO to open it. But Windows does not treat the content as coming from the Internet. So, again, there is no MotW and no Protected View.
This attack is more dangerous than macros because any organization that chooses to disable or otherwise restrict the execution of macros is still vulnerable to arbitrary code execution as a result of simply opening Office documents. says Dormann.
In addition, the expert discovered that the vulnerability could also be exploited using RTF files, which are not protected by Office Protected View.
Inspired by @buffaloverflow, I tested out the RTF attack vector. And it works quite nicely.
WHERE IS YOUR PROTECTED MODE NOW? pic.twitter.com/qf021VYO2R— Will Dormann (@wdormann) September 9, 2021
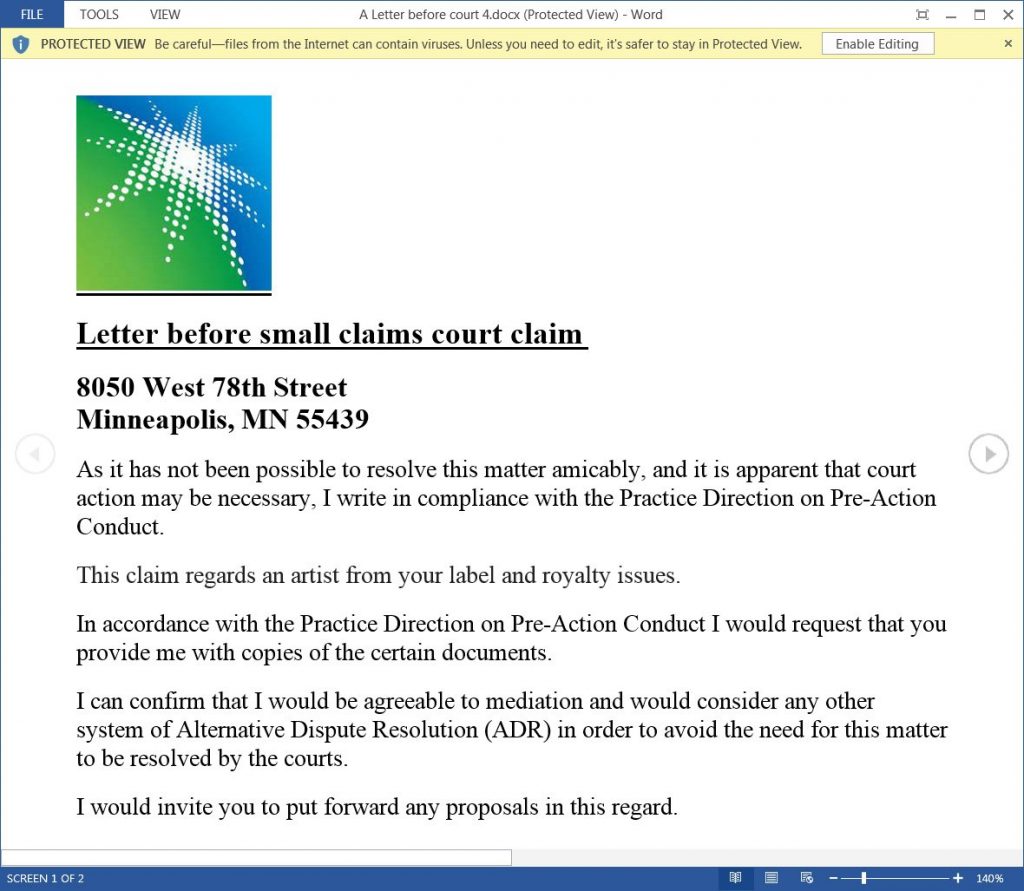
Another well-known information security researcher, Kevin Beaumont, studied the malicious Word document to better understand how the exploit for CVE-2021-40444 works. For example, one of the known malicious attachments used in attacks is the document “A Letter before court 4.docx”. Since the file is downloaded from the Internet, it receives the MotW tag and opens in Protected View.
However, if the user clicks the “Allow Editing” button, the exploit uses MHTML and loads the “side.html” file hosted on the remote site, which is loaded as a Word template.
When the MHTML URL is “noticed” by Internet Explorer, it triggers the HTML download, and the obfuscated JavaScript code exploits CVE-2021-40444, creating a malicious ActiveX control. This ActiveX control will download the “ministry.cab” file from the remote site, extract the “Championship.inf” file (actually a DLL) and execute it as a Control Panel CPL file.
Trend Micro researchers, who also studied these attacks, write that the main payload in this case is the Cobalt Strike beacon, which will allow an attacker to gain remote access to the device.