Information security specialists have discovered serious vulnerabilities in GPS trackers, which are used in about 1.5 million cars in 169 countries around the world. We are talking about the device MiCODUS MV720, which contains six vulnerabilities at once.
Experts from BitSight say that vehicles equipped with these GPS trackers are used by many Fortune 50 companies, as well as governments, military, law enforcement, aerospace, shipping and manufacturing companies.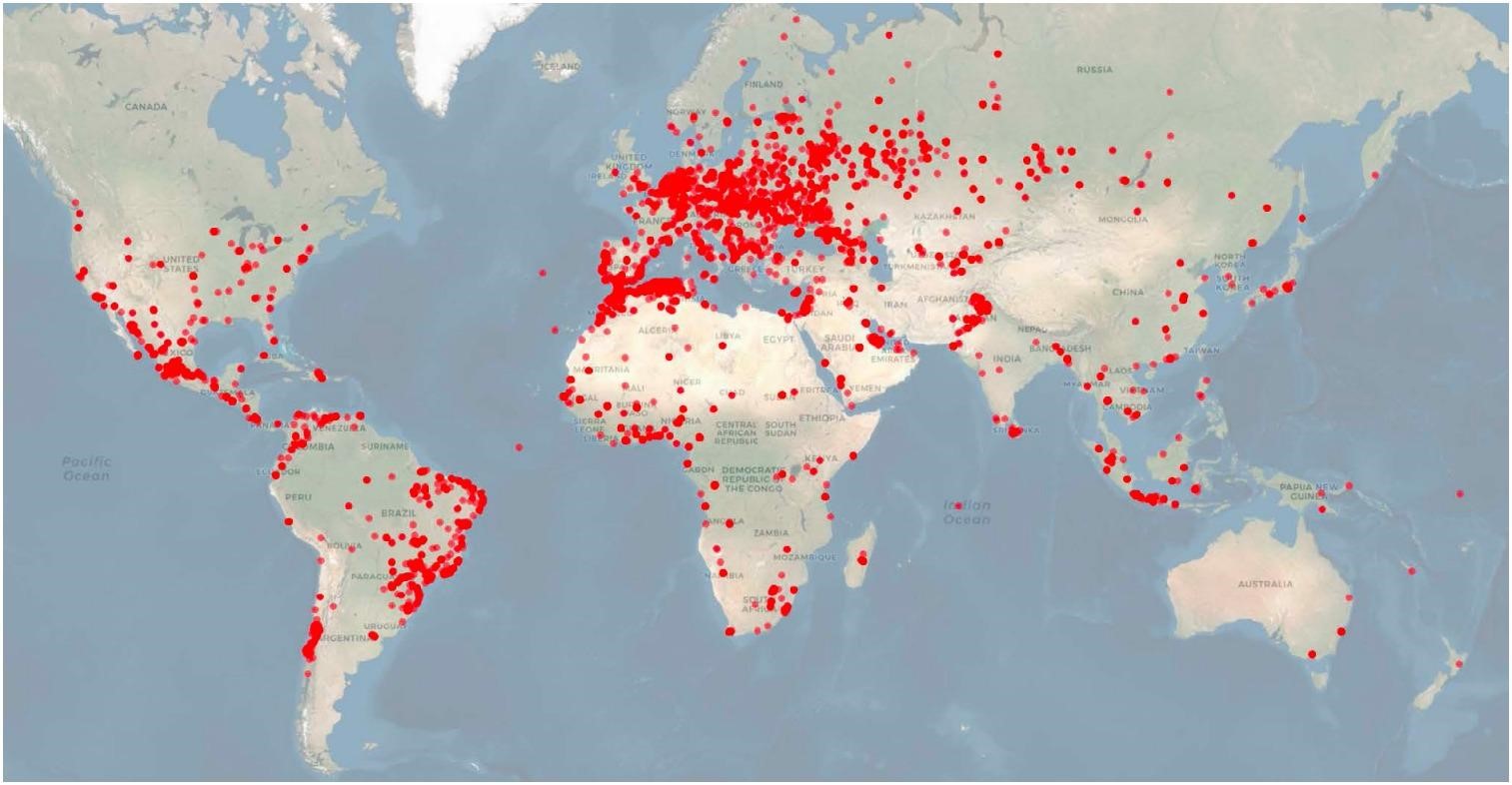
MiCODUS MV720 users on the map
Let me remind you that we also said that GPS devices may behave unpredictably in the coming days due to a bug in the GPS Daemon, and also that Audi and Volkswagen customer data put on sale.
A hacker who breaks into a vulnerable MV720 will be able to use the tracker to track the vehicle, be able to immobilize it, or simply collect route information and manipulate the data. According to the researchers, such hacks can have serious consequences for the national security of different countries.
The experts studied the specific model of MiCODUS because it is an inexpensive (about $20) and very popular device that has cellular-enabled tracking features and can also be used for potentially dangerous activities, including turning off the fuel supply.
Not all vulnerabilities discovered by BitSight have received a CVE identifier yet, but they are described as follows.
CVE-2022-2107 (CVSS score 9.8): A hard-coded master password on an API server that allows a remote and unauthenticated attacker to take control of any MV720 tracker, cut off fuel, track users, and disable alarms.
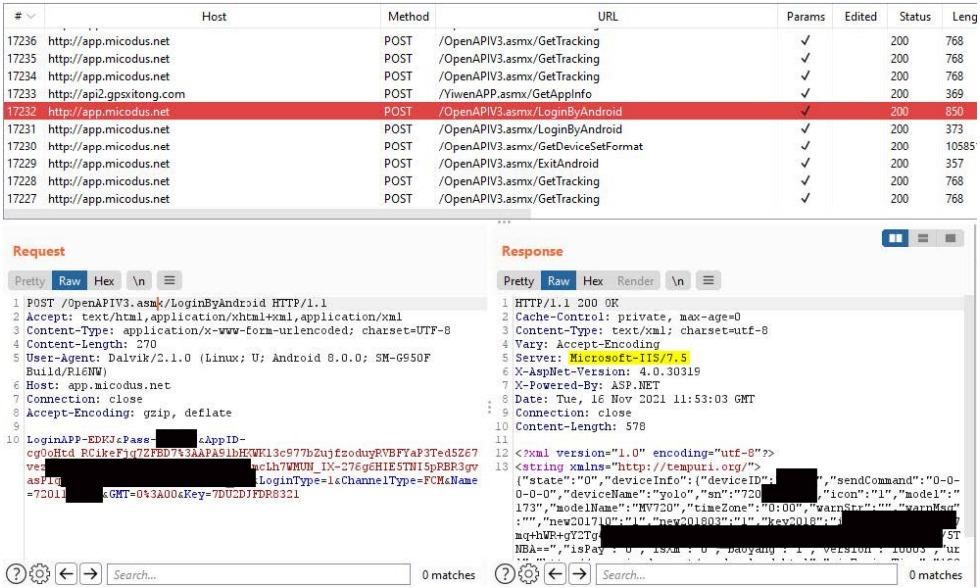
CVE-2022-2141 (CVSS score 9.8): A broken authentication scheme that allows anyone to send commands to a GPS tracker via SMS and execute them with administrator rights.
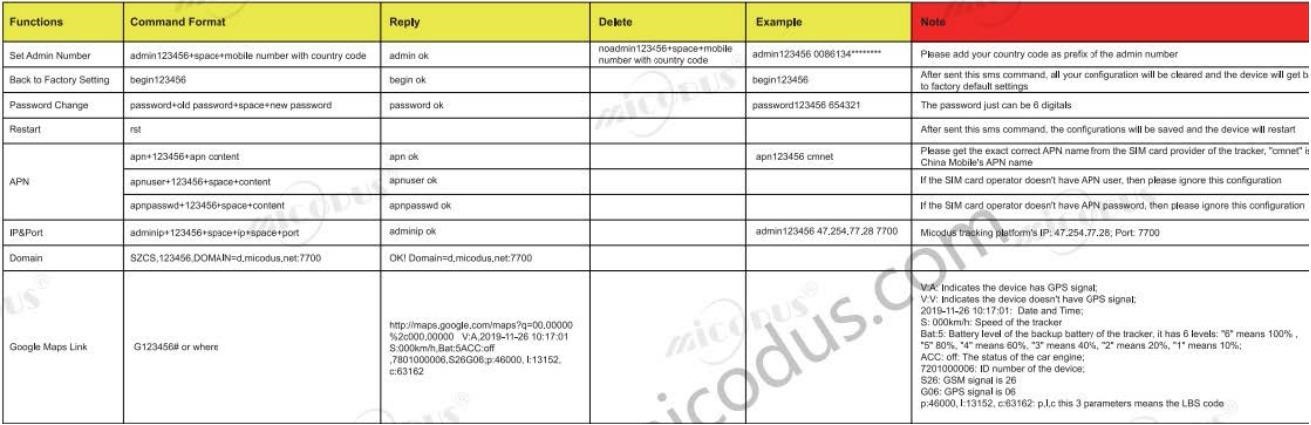
Supported SMS Commands
CVE Not Assigned (CVSS 8.1): Weak default password (123456) on all MV720 trackers, and user is not required to change it after initial device setup.
CVE-2022-2199 (CVSS score 7.5): An XSS vulnerability on the main web server that could allow an attacker to gain access to user accounts, interact with applications, and view all information available to a specific user.
CVE-2022-34150 (CVSS score 7.1): An insecure direct link to an object on the main web server that allows a logged-in user to access the data of any ID in the server’s database.
CVE-2022-33944 (CVSS score 6.5): An insecure direct link to an object on the main web server that allows unauthorized users to generate Excel reports on GPS tracker activity.
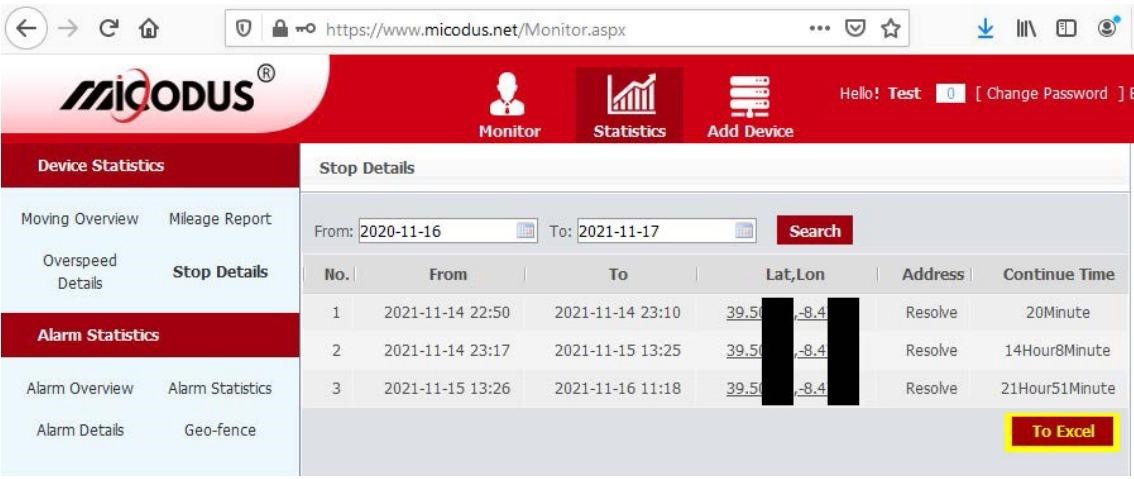
During their research, BitSight experts developed five PoC exploits for five vulnerabilities that received identification numbers and demonstrated the exploitation of bugs in real conditions.
Interestingly, the researchers found the described vulnerabilities as early as September 9, 2021, after which they tried to immediately contact MiCODUS engineers, but this was not so easy. Repeated attempts to get in touch with the company and find a person who could accept the vulnerability report were unsuccessful. As a result, on January 14, 2022, BitSight representatives shared all the technical details about the vulnerabilities with the US Department of Homeland Security and asked them to contact the vendor themselves.
Unfortunately, MiCODUS MV720 GPS trackers are currently still vulnerable to the above problems, as the manufacturer has not yet released patches.
Also, the US Cybersecurity and Infrastructure Security Agency (CISA) has already prepared its own security bulletin warning that MiCODUS devices may pose a threat.
