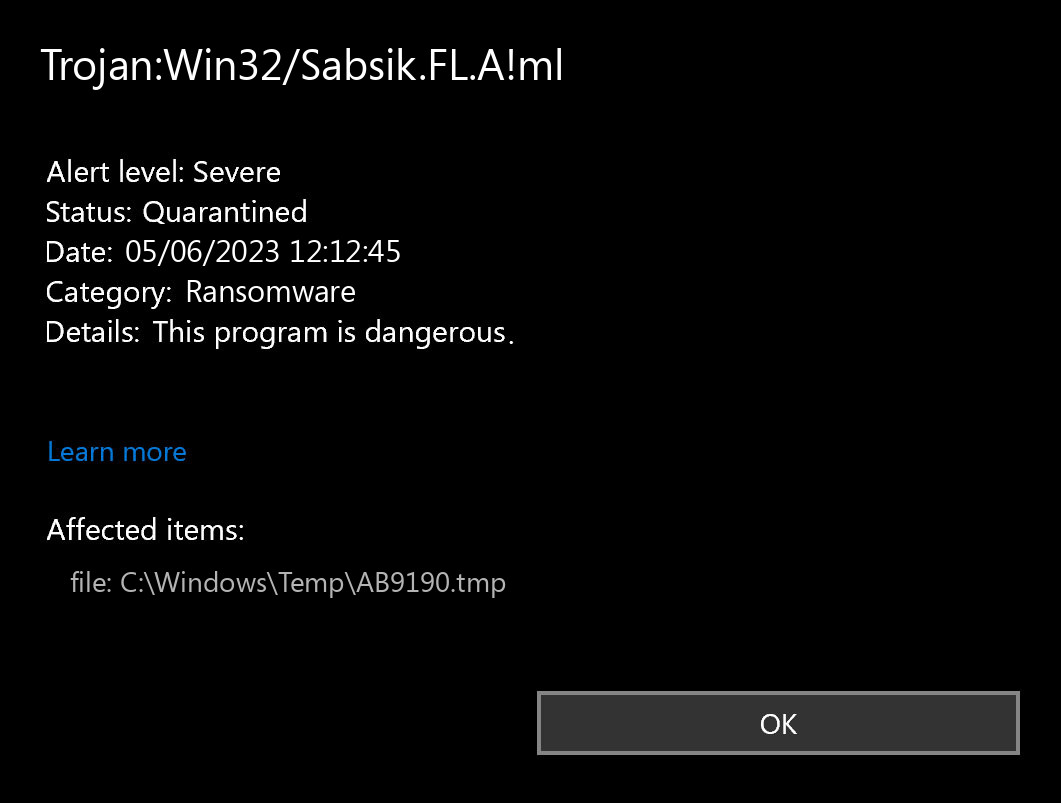
If you receive an alert indicating the detection of Trojan:Win32/Sabsik.FL.A!ml, it means that your computer is experiencing a problem. All malicious programs, including Sabsik, are dangerous without exceptions. Sabsik is a virus that targets file encryption and demands a ransom payment to regain access to the files. In simple terms, the detection of Trojan:Win32/Sabsik.FL.A!ml signifies a significant threat to your system.
All types of malware are created with one objective – to make money from you. The creators of these malicious programs do not consider morality and employ any possible tactics. In the case of Sabsik malware, they are not concerned with stealing your data or using your hardware for cryptocurrency mining. Instead, Sabsik encrypts your files and presents ransom notes demanding payments of up to $4000 for decryption.
What does the notification with Trojan:Win32/Sabsik.FL.A!ml detection mean?
The Trojan:Win32/Sabsik.FL.A!ml detection you can see in the lower right corner is demonstrated to you by Microsoft Defender. That anti-malware program is pretty good at scanning, however, prone to be basically unreliable. It is unprotected to malware attacks, it has a glitchy user interface and bugged malware clearing features. For this reason, the pop-up which states concerning the Sabsik is rather just a notification that Defender has identified it. To remove it, you will likely need to make use of another anti-malware program.
The exact Trojan:Win32/Sabsik.FL.A!ml virus is a really undesirable thing. It sits into your Windows disguised as a part of something legitimate, or as a part of the application you have got on a forum. Therefore, it makes everything to weaken your system. At the end of this “party”, it injects other malicious things – ones which are wanted by cybercriminals who manage this malware. Hence, it is likely impossible to predict the effects from Sabsik actions. And the unpredictability is one of the baddest things when it comes to malware. That’s why it is better not to choose at all, and don’t give it even a single chance to complete its task.
Threat Summary:
| Name | Sabsik Ransomware |
| Detection | Trojan:Win32/Sabsik.FL.A!ml |
| Details | Sabsik is attached to another program (such as a document), which can replicate and spread after an initial execution. |
| Similar behavior | Trojan:Win32/Wacatac.H!ml, Wacatac.B!ml, Phonzy.A!ml, Ulthar.A!ml |
| Fix Tool | See If Your System Has Been Affected by Sabsik Ransomware |
Malware Behaviour
- Executable code extraction. Cybercriminals often use binary packers to hinder the malicious code from reverse-engineered by malware analysts. A packer is a tool that compresses, encrypts, and modifies a malicious file’s format. Sometimes packers can be used for legitimate ends, for example, to protect a program against cracking or copying.
- Creates RWX memory. There is a security trick with memory regions that allows an attacker to fill a buffer with a shellcode and then execute it. Filling a buffer with shellcode isn’t a big deal, it’s just data. The problem arises when the attacker is able to control the instruction pointer (EIP), usually by corrupting a function’s stack frame using a stack-based buffer overflow, and then changing the flow of execution by assigning this pointer to the address of the shellcode.
- A process attempted to delay the analysis task.;
- The binary likely contains encrypted or compressed data. In this case, encryption is a way of hiding virus’ code from antiviruses and virus’ analysts.
- Executed a very long command line or script command which may be indicative of chained commands or obfuscation;
- A scripting utility was executed;
- Uses Windows utilities for basic functionality;
- Attempts to stop active services;
- Attempts to repeatedly call a single API many times in order to delay analysis time. This significantly complicates the work of the virus analyzer. Typical malware tactics!
- Attempts to execute a powershell command with suspicious parameter/s;
- Creates a hidden or system file. The malware adds the hidden attribute to every file and folder on your system, so it appears as if everything has been deleted from your hard drive.
- Network activity detected but not expressed in API logs. Microsoft built an API solution right into its Windows operating system it reveals network activity for all apps and programs that ran on the computer in the past 30-days. This malware hides network activity.
- Anomalous binary characteristics. This is a way of hiding virus’ code from antiviruses and virus’ analysts.
- Uses suspicious command line tools or Windows utilities;
- Ciphering the records situated on the sufferer’s hard drive — so the user cannot access the files;
- Spawning ransom notes all over the system;
File Details
File Info:
crc32: EA835E34md5: 0db6e597c05b028d19faddb24c46e089name: 0DB6E597C05B028D19FADDB24C46E089.mlwsha1: a6763061a806d4aab8790fd30bcd1e89aac9e497sha256: 26ab5d2dcd0594537874a28ac4a644e761aaa1d841d57d53d20b98bfae178f4asha512: deb9954ecdd97b838925b033a57f6155e9a334dda3cd0ccb723f90c27d754f5db8a95a1777e422ede02760c8963b715f916be2f46fdaf9db1ed05e77af218da1ssdeep: 6144:MBlkZvaF4NTB9/OXOwCtdIr2PyV1MOAA1e:MoSWNTfcOxtdIyPxO5etype: PE32 executable (console) Intel 80386, for MS WindowsVersion Info:
0: [No Data]
Other Detection Names
| GridinSoft | Trojan.Sabsik |
| Bkav | W32.AIDetect.malware1 |
| Elastic | malicious (high confidence) |
| ALYac | DeepScan:Generic.Ransom.Mole.83D10BE2 |
| Cylance | Unsafe |
| Sangfor | Trojan.Win32.Save.a |
| BitDefender | DeepScan:Generic.Ransom.Mole.83D10BE2 |
| Cybereason | malicious.7c05b0 |
| Symantec | ML.Attribute.HighConfidence |
| APEX | Malicious |
| Cynet | Malicious (score: 100) |
| MicroWorld-eScan | DeepScan:Generic.Ransom.Mole.83D10BE2 |
| Ad-Aware | DeepScan:Generic.Ransom.Mole.83D10BE2 |
| Sophos | ML/PE-A |
| BitDefenderTheta | Gen:NN.ZexaF.34690.nuW@aKxN7Vj |
| McAfee-GW-Edition | BehavesLike.Win32.Generic.dc |
| FireEye | Generic.mg.0db6e597c05b028d |
| Emsisoft | DeepScan:Generic.Ransom.Mole.83D10BE2 (B) |
| SentinelOne | Static AI – Suspicious PE |
| eGambit | Unsafe.AI_Score_99% |
| Microsoft | Trojan:Win32/Sabsik.FL.A!ml |
| Arcabit | DeepScan:Generic.Ransom.Mole.83D10BE2 |
| GData | DeepScan:Generic.Ransom.Mole.83D10BE2 |
| Acronis | suspicious |
| MAX | malware (ai score=88) |
| Rising | Malware.Heuristic!ET#99% (RDMK:cmRtazqXzEtf+YgiE6sIKOcrDdAM) |
| MaxSecure | Trojan.Malware.300983.susgen |
Is Trojan:Win32/Sabsik.FL.A!ml dangerous?
As I have actually stated , non-harmful malware does not exist. And Trojan:Win32/Sabsik.FL.A!ml is not an exception. This malware alters the system settings, modifies the Group Policies and Windows registry. All of these elements are crucial for correct system operating, even in case when we are not talking about system safety. Therefore, the malware which Sabsik contains, or which it will inject later, will squeeze out maximum profit from you. Cyber burglars can steal your personal information, and then sell it at the black market. Using adware and browser hijacker functions, embedded in Trojan:Win32/Sabsik.FL.A!ml virus, they can make revenue by showing you the advertisements. Each view gives them a penny, but 100 views per day = $1. 1000 victims who watch 100 banners per day – $1000. Easy math, but sad conclusions. It is a bad choice to be a donkey for crooks.
How did I get this virus?
It is hard to line the origins of malware on your computer. Nowadays, things are mixed, and distribution ways utilized by adware 5 years ago can be utilized by spyware nowadays. But if we abstract from the exact distribution method and will think of why it works, the reply will be very simple – low level of cybersecurity awareness. Individuals press on promotions on strange websites, open the pop-ups they receive in their browsers, call the “Microsoft tech support” believing that the weird banner that says about malware is true. It is very important to understand what is legitimate – to stay away from misconceptions when trying to figure out a virus.
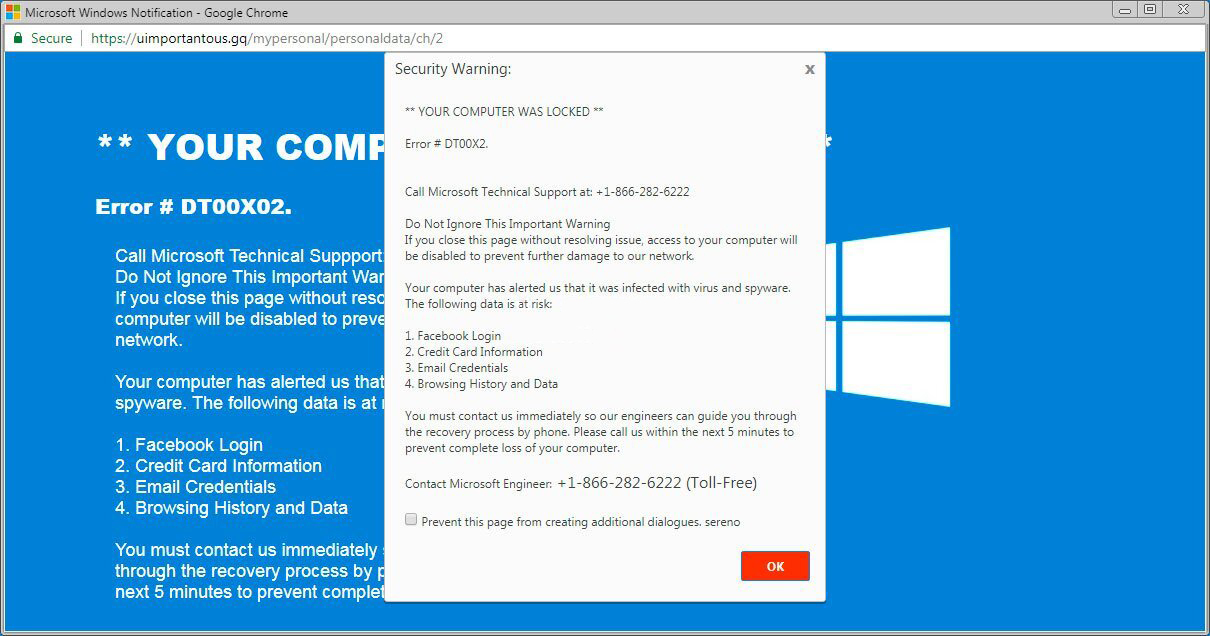
The example of Microsoft Tech support scam banner
Nowadays, there are two of the most widespread ways of malware distribution – lure e-mails and injection into a hacked program. While the first one is not so easy to avoid – you must know a lot to understand a counterfeit – the second one is very easy to solve: just don’t use cracked apps. Torrent-trackers and various other providers of “totally free” applications (which are, in fact, paid, but with a disabled license checking) are just a giveaway point of malware. And Trojan:Win32/Sabsik.FL.A!ml is just within them.
How to remove the Trojan:Win32/Sabsik.FL.A!ml from my PC?
Trojan:Win32/Sabsik.FL.A!ml malware is incredibly hard to erase by hand. It places its documents in multiple places throughout the disk, and can restore itself from one of the elements. In addition, various changes in the registry, networking setups and Group Policies are pretty hard to discover and return to the original. It is much better to utilize a special program – exactly, an anti-malware app. GridinSoft Anti-Malware will definitely fit the most ideal for malware removal goals.
Why GridinSoft Anti-Malware? It is very light-weight and has its detection databases updated practically every hour. In addition, it does not have such bugs and exposures as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for clearing away malware of any kind.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Sabsik the default option is “Delete”. Press “Apply” to finish the malware removal.