In the SQLite DBMS, researchers discovered a serious vulnerability that got into the source code back in October 2000. The problem could allow attackers to cause malfunction of the prgrams or to manipulate them.
SQLite is used almost everywhere, from warships to smartphones and other programming languages. The open-source database engine has a long history of reliability and high security: many of the CVEs that are natively tied to SQLite don’t actually affect the operation of the DBMS at all.
Let me remind you that we also wrote that Attackers Hack into Microsoft SQL Servers and Turn Them into Proxies.
The problem was discovered by Trail of Bits specialists, who, however, write that it was assigned the identifier CVE-2022-35737 and a score of 7.5 points on the CVSS scale.
The researchers say that the bug can be exploited on 64-bit systems, and “the possibility of exploitation depends on how the program is compiled.”
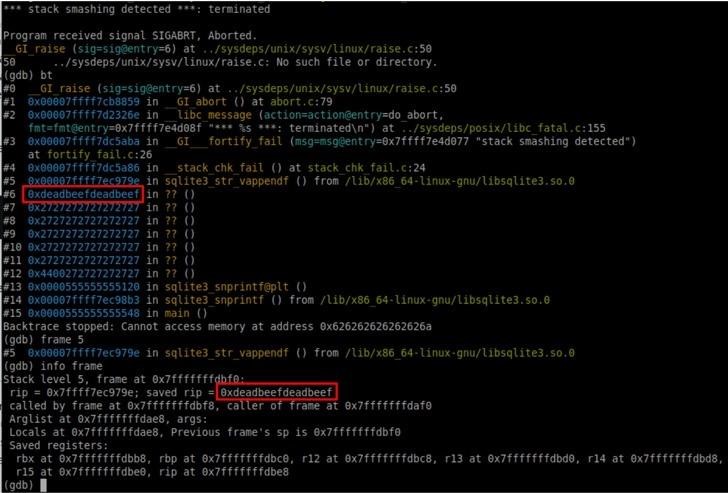
The problem is related to integer overflow, which occurs when an extremely large input string is passed as parameters to SQLite implementations of printf functions, which in turn use another function to handle string formatting (sqlite3_str_vappendf). In this case, the attack is feasible only if the format string contains the substitutions %Q, %q or %w.
Interestingly, this is a bug that may not have seemed like a bug at the time RDBMS was created (and has been present since 2000 in the SQLite source code), when systems were mostly 32-bit architectures.
The issue affected SQLite versions 1.0.12 to 3.39.1 and was fixed with the release of version 3.39.2 released on July 21, 2022.
