Dharma Ransomware
The Dharma Boom: how works shy, but most successful ransomware of recent years
Recently, names of ransomware related to high-profile hacks of large companies, theft of personal information of celebrities and politicians, and multimillion-dollar ransom demands have been widespread on resources devoted to information security. Examples include Maze, ReVIL/Sodinokibi, and WastedLocker. However, the most successful service in this area is not the ransomware Dharma, which is spreading on underground forums by the ransomware as a service (RaaS) business model.
Introduced in 2016, Dharma is truly one of the most profitable ransomware programs today due to its service business model. This is supported by studies like “Color by numbers: Inside a Dharma RaaS attack” from Sophos and Covewar publications.
With multi-million dollar ransoms and big sacrifices, WastedLocker is now the hero of the news, so it’s easy to forget that threats like Dharma are alive, doing well, and allow cybercriminals to attack slightly smaller targets to make a fortune — $ 8,000 at a time.senior analyst at Sophos, Sean Gallagher
McDonald’s of cybercriminal underworld
The researchers write that Dharma can be compared to a franchise for a fast-food enterprise like McDonald’s since the malware can be purchased and used by anyone who can follow criminal instructions on how to cause the most damage.
Ease of use is at the heart of the Dharma RaaS business model. Clients are offered a package of scripts and tools that do not require special technical skills to use.
The subscription price for the service is $2 thousand. Customers do the dirty work themselves – they hack into the enterprise network and install ransomware, while the service operators receive passive income.
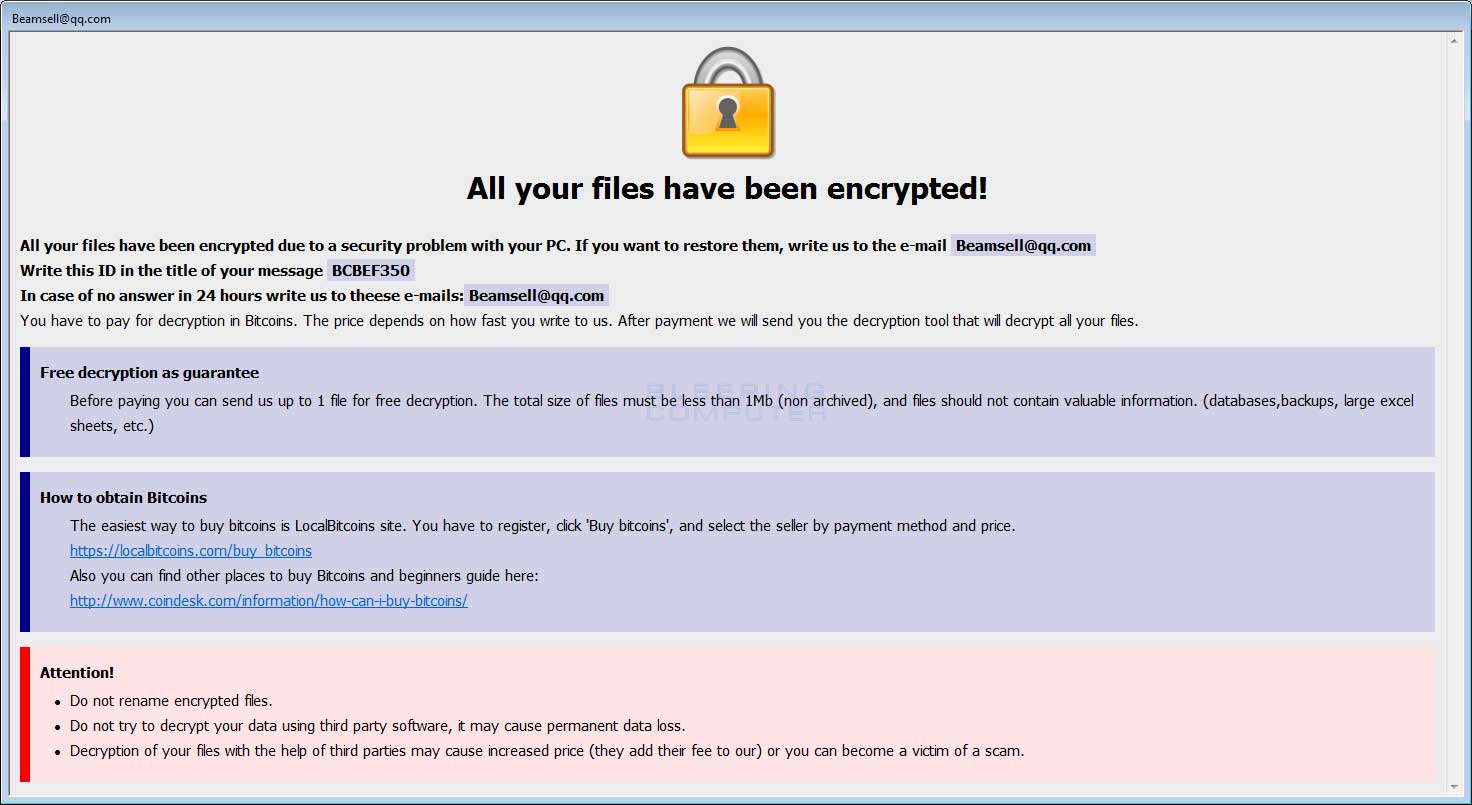
Message from the Dharma
A Brief History of the Dharma
The ransomware was initially launched under CrySiS in the summer of 2016.
CrySis was a so-called ransomware-as-a-service (RaaS) operation. The author of CrySiS created a service where clients (other criminal groups) could make their versions of the ransomware to distribute to victims. Usually through spam campaigns, exploit kits, or brute force attacks on RDP endpoints.
After someone leaked the CrySiS master decryption keys in November 2016, CrySiS RaaS was relaunched two weeks later under the name Dharma.
However, some Dharma decryption keys also leaked to the network in March 2017. Still, Dharma operators did not rebrand this time. Instead, they continued to work without interruption, turning their RaaS into one of the most extensive ready-made solutions for ransomware in the underworld.
Over the years, there has been a constant stream of new versions of the Dharma. The ransomware received updates, new customers signed up to distribute it, and many unique variations of the Dharma were spread throughout the world.
With the updates of criminal underground in 2018 and 2019 – from the massive spread of ransomware (via email spam) to targeted attacks (on corporate networks) – the Dharma also has changed.
In the spring of 2019, on the network appeared a new strain called Phobos, which is used mainly for targeted attacks. Security researchers at Coveware and Malwarebytes immediately noted that Phobos is almost identical to Dharma.
Nevertheless, the “good old” Dharma did not rest after the release of Phobos either.
The number of downloads to the ID-Ransomware service remained at
50/50 for Dharma and Phobos throughout 2019″
Michael Gillespie, creator of ID-RansomwareJakub Kroustek, head of threat intelligence at Avast, only discovered three new versions of Dharma in the spring of 2020, which means that criminal groups still believe the Dharma code to be reliable and continue to use it even now, more than three years after its launch.
John Fokker, head of cyber investigations at McAfee, told ZDNet that the Dharma code has been circulating in the hacker underground for quite some time and is only now emerging on quite open forums: for example, in March 2020, the source code of one of the ransomware versions was put for sale on a Russian-speaking hacker forum.
Gillespie, who has released dozens of ransomware decryptors in the past and even received an FBI award for his efforts, told ZDNet that he had been unable to find decryption flaws in Dharma.
Dharma Epidemic Mechanism
Due to its accessibility, Dharma has become the center of a criminal ecosystem based on the “syndication” business model. Dharma RaaS vendors offer their technical expertise and support by managing internal systems that support ransomware attacks.
Affiliates (often entry-level cybercriminals) pay to use RaaS and conduct targeted attacks themselves using a standard set of tools. Other actors provide stolen credentials and other tools on criminal forums that allow attacking the Remote Desktop Protocol, the predominant initial hacking tool for Dharma subjects. (According to statistics provided by Coveware, RDP attacks are the main cause of approximately 85% of Dharma attacks.)
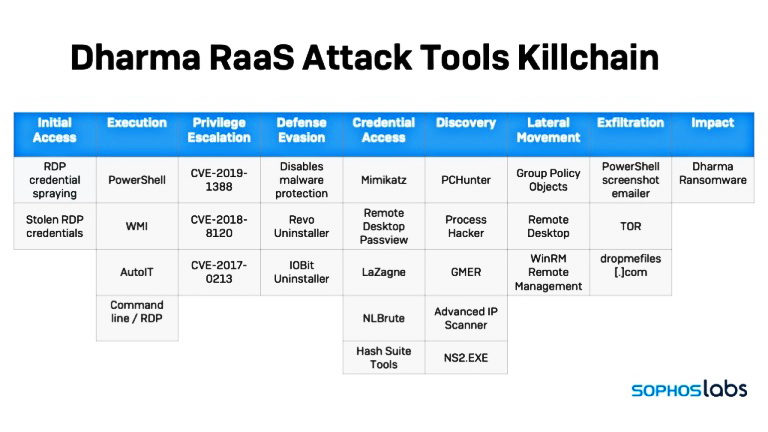
You can find some technical details in our previous Dharma review.
Over the past year, Dharma subjects’ ransom demands were lower compared to other major types of targeted ransomware. For example, in December 2019, when the average ransomware demand rose to $191,000, the average Dharma ransom demand was only $8,620. This is partly due to the types of targets hit by the Dharma (mainly small and medium-sized businesses) and partly to the attacking affiliates’ skills, experience, and location. Either way, Dharma operators are mitigated lower ransomware demands by the number of victims, as Dharma remains one of the most profitable ransomware families, according to Coveware.
How to prevent Dharma infection
Most of these attacks from Dharma partners can be prevented by patching and securing RDP servers with VPN with multi-factor authentication. Organizations need to be vigilant against phishing credentials, especially as they adjust to new working settings when more and more employees work remotely. In addition, attention is required to the access provided to service providers and other third parties for business purposes.
Frequently Asked Questions (FAQ)
How did I get infected with Dharma Ransomware?
Dharma ransomware mostly comes via RDP, so please disable it or
change the default port for RDP. Sometimes Dharma comes via utilized email phishing to remote into a network via an employee’s computer or utilized malicious attachments, downloads, application patch exploits, or vulnerabilities to gain access to a network.
What are Dharma ransomware file extensions?
You can find a full list of the latest Dharma ransomware versions in the list below on this page.

















