Check Point compiled a report on the brands that are most frequently used in phishing attacks in Q1 2021 and found that phishers still appreciate Microsoft and DHL. Cybercriminals most often imitated these companies in order to win over users and get the information they need.
Most often, during such attacks, cybercriminals try to imitate the official website of a well-known company using a domain name, URL, and design similar to the original.Fake websites often contain a form designed to steal credentials, billing information, and other personal information.
In the first quarter of 2021, as in the previous quarter, cybercriminals most often used the Microsoft brand. 39% of all phishing attempts involving well-known companies were associated with this particular company (slightly less than in the fourth quarter – then this figure was 43%). This shows that cybercriminals are still targeting those who work remotely.
In second place is DHL (18% of all attempts): hackers continue to exploit the growing demand for online purchases.
The company’s report demonstrates that hackers are more likely to continue to exploit IT. It is also interesting that banking is in third place, as this time it replaced retail in the top leaders, as two banking brands, Wells Fargo and Chase, entered the top ten. This shows how cybercriminals are leveraging the rise of digital payments, dependence on online banking, online shopping and home delivery.
Top brands most frequently used by cybercriminals in phishing attacks:
- Microsoft (39% of all attempts at phishing attacks using brand names worldwide);
- DHL (18%);
- Google (9%);
- Roblox (6%);
- Amazon (5%);
- Wells Fargo (4%);
- Chase (2%);
- LinkedIn (2%);
- Apple (2%);
- Dropbox (2%).
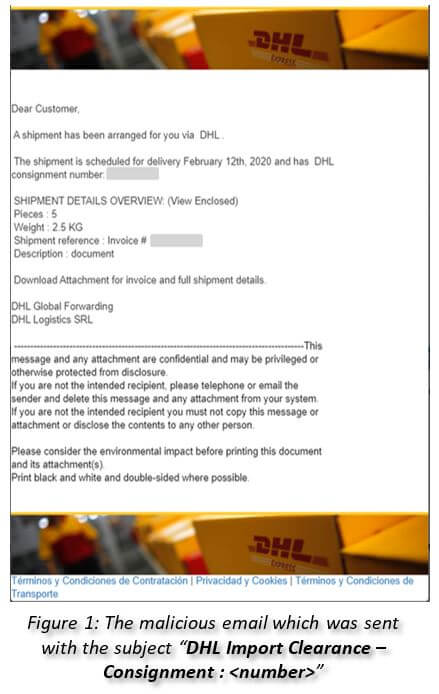
Researchers cite several examples of phishing emails exploiting well-known brands. For example, experts attach a phishing email to the report that used the DHL brand. The message tried to download a remote access trojan (Agent Tesla) onto the user’s computer.
An email with the subject line “DHL Import Clearance – Consignment:
Another email targeted the theft of Wells Fargo user account data. It came from a fake email address [email protected] and had the subject “Your Online access has been disabled“. The attacker tried to trick the victim into clicking a malicious link that redirects the user to a fraudulent page that looks like the real Wells Fargo site. After clicking on the link, the user was asked to enter his username and password.
We also talked about how cybercriminals are actively using the coronavirus theme in phishing attacks and, for example, Gmail blocked 18 million phishing emails related COVID-19 over the week.
