The Nood virus, part of the STOP malware family, actively targets computer systems for file encryption and ransom demands. Once it infects a computer, it searches and encrypts various file types such as documents, videos, and photos, appending the “.nood” extension to each, which makes them inaccessible without a decryption key.
Nood Virus
Nood
🤔 The Nood virus, a member of the DJVU/STOP ransomware family, aims to encrypt accessible files before demanding a ransom of $499 to $999 in Bitcoin from its victims.
The Nood virus encrypts your files, forcing you to pay for their recovery. It encrypts a broad array of file types, marking each with a unique “.nood” extension, rendering affected files inaccessible.
Following encryption, the virus demands a Bitcoin ransom from its victims, ranging from $499 to $999, depending on how much time has passed since the attack. It leaves a text file, “_readme.txt“, containing payment instructions.
Nood Ransomware employs the Salsa20 encryption algorithm, making it extremely difficult to decrypt files without the attackers’ help.
After encrypting the files, Nood displays a ransom note, demanding payment for the decryption key. This note includes payment instructions and often threats of permanent data loss or an increased ransom if not paid promptly.
I have compiled a comprehensive list of solutions, advice, and practices for stopping the Nood ransomware and regaining access to your files. Sometimes, decryption is possible; other times, it may not be.
📌 Important Note!
Paying the ransom does not guarantee the successful recovery of your files. The individuals behind the Nood virus are not trustworthy. There have been instances where victims paid the ransom and were still denied the decryption key by the cybercriminals.
Nood uses a unique key for each victim, except:
- When Nood cannot connect to its command and control server (C&C) before starting the encryption, it resorts to using offline keys. These offline keys, the same for all affected users, allow some files encrypted by the ransomware to be decrypted.
Similar to other DJVU ransomware variants like Wiaw and Lkfr, Nood encrypts a wide range of common file types and appends the “.nood” extension. For example, a file named “1.jpg” becomes “1.jpg.nood” and “2.png” to “2.png.nood“.
Following encryption, the virus generates a special text file named “_readme.txt” and places it in every folder with encrypted files, as well as on the desktop, ensuring victims notice it immediately.
The image below offers a visual representation of files with the “nood” extension:
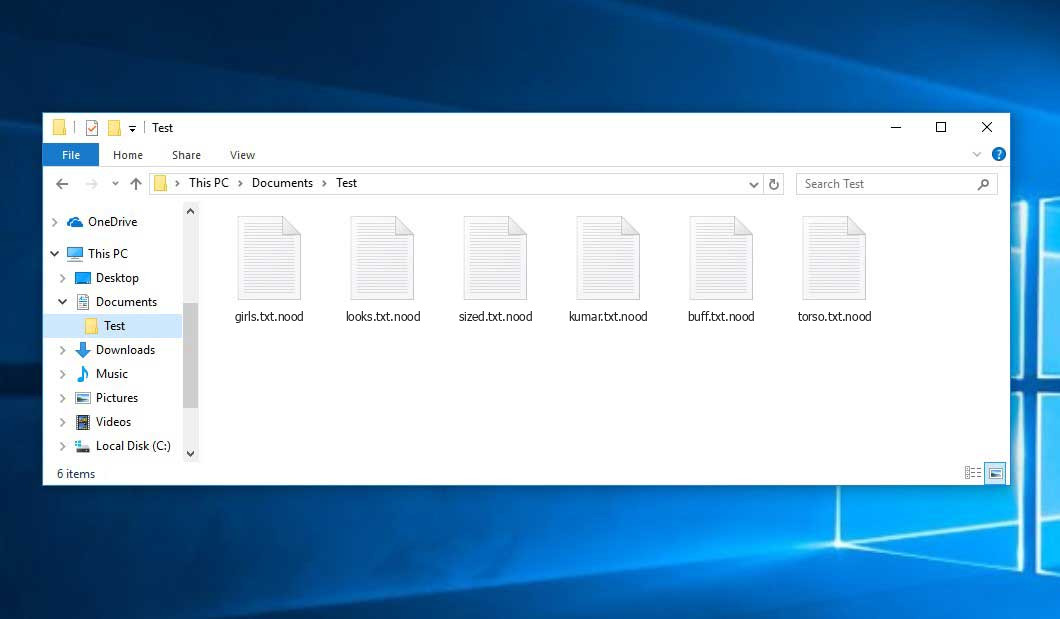
Encrypted Files by STOP/DJVU Ransomware
| Name | Nood Virus |
| Ransomware family1 | DJVU/STOP2 ransomware |
| Extension | .nood |
| Ransomware note | _readme.txt |
| Ransom | From $499 to $999 (in Bitcoins) |
| Contact | support@freshingmail.top, datarestorehelpyou@airmail.cc |
| Detection | Malware.Heuristic.2046, Trojan:Win32/Vundo.A, Trojan:Win32/Conhook.D |
| Symptoms |
|
| Fix Tool | To remove possible malware infections, scan your PC: 6-day free trial available. |
This message demands payment for restoring files via a decryption key:
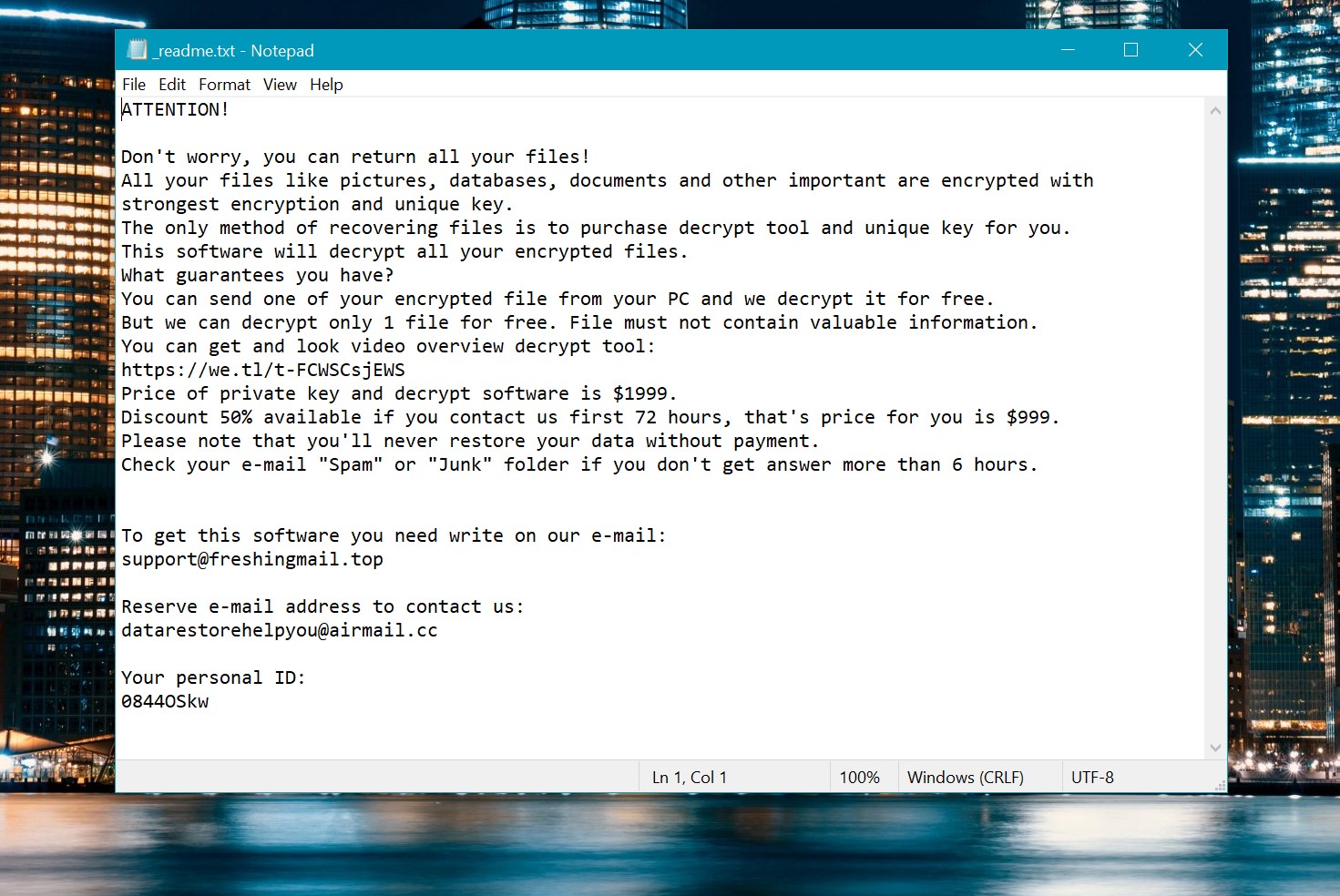
_readme.txt (STOP/DJVU Ransomware) – The intimidating warning that demands users pay the ransom to decrypt their encrypted data, filled with these irksome cautions.
The Nood ransomware executes a series of operations on the victim’s computer, starting with launching winupdate.exe. This deceptive process mimics a Windows update notification to mislead the victim into thinking the system slowdown is due to an update.
Simultaneously, the ransomware activates another process, named with 4 random characters, which scans the PC for target files to encrypt. It then proceeds to eliminate Volume Shadow Copies from the system with the following CMD command:
vssadmin.exe Delete Shadows /All /Quiet
With Volume Shadow Copies gone, restoring the computer to its previous state through System Restore Points becomes nearly impossible. The ransomware creators deliberately remove any built-in Windows recovery methods that could allow victims to retrieve their files for free. Moreover, they alter the Windows HOSTS file by adding and redirecting a list of domains to the localhost IP, causing the victim to encounter a DNS_PROBE_FINISHED_NXDOMAIN error when attempting to visit any of the blocked sites.
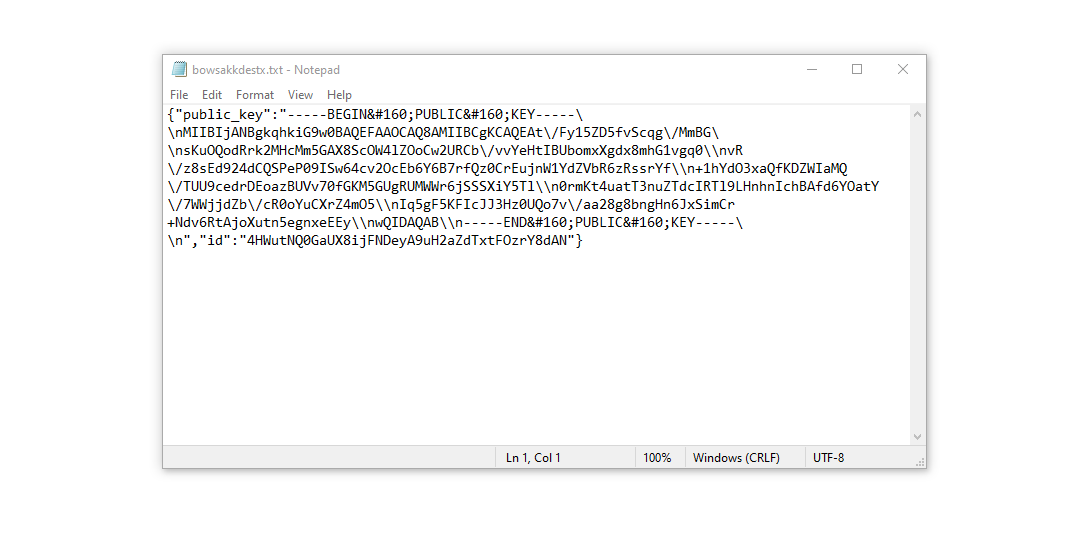
This tactic aims to prevent victims from accessing online guides that could help counter the ransomware attack. By blocking certain websites, the attackers obstruct victims’ access to valuable information. Additionally, the malware leaves two .txt files on the victim’s system, revealing attack-specific details — the public encryption key and a personal ID, named bowsakkdestx.txt and PersonalID.txt.
Furthermore, STOP/DJVU variants often install the Vidar password-stealing Trojan on infected systems, which boasts a broad set of harmful capabilities:
- Running malicious software to gather sensitive data.
- Stealing login credentials for Steam, Telegram, and Skype accounts.
- Accessing and manipulating files without the victim’s consent.
- Extracting cryptocurrency wallets.
- Allowing hackers to remotely control the victim’s computer for nefarious purposes.
- Collecting browser cookies, saved passwords, and browsing history.
The STOP/Djvu ransomware uses the Salsa20 encryption algorithm. If your files were encrypted with an online decryption key, the chances of recovery are slim. Each victim’s online key is unique, making a suitable match difficult to find.
Securing the online decryption key otherwise is nearly impossible, as it resides on a server controlled by the Nood virus distributors. To get the unlocking key, victims must pay $999 and contact the fraudsters via email (support@freshingmail.top).
The message by the ransomware states the following information:
ATTENTION! Don't worry, you can return all your files! All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. Do not ask assistants from youtube and recovery data sites for help in recovering your data. They can use your free decryption quota and scam you. Our contact is emails in this text document only. You can get and look video overview decrypt tool: https://we.tl/t-hPAqznkJKD Price of private key and decrypt software is $999. Discount 50% available if you contact us first 72 hours, that's price for you is $499. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: support@freshingmail.top Reserve e-mail address to contact us: datarestorehelpyou@airmail.cc Your personal ID: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
How to Remove Nood Ransomware
Download the Removal Tool
Click below to download GridinSoft Anti-Malware:
Install Anti-malware
After downloading, open the setup-antimalware-fix.exe file to start the installation of GridinSoft Anti-Malware.
Click “Yes” when the User Account Control prompts you to allow GridinSoft Anti-Malware to make changes to your device.
Start the Installation
Run the Anti-Malware Tool
GridinSoft Anti-Malware will launch automatically after installation.

Scan Your Computer
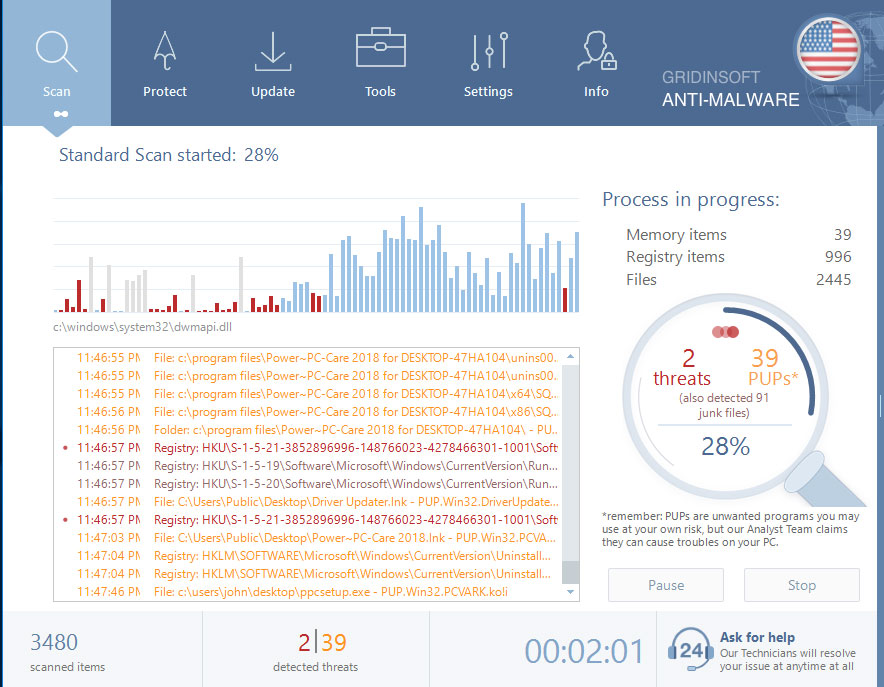
Allow GridinSoft Anti-Malware to scan your computer for infections. This comprehensive scan may take 20-30 minutes. Check the scan progress periodically.
Eliminate Detected Threats
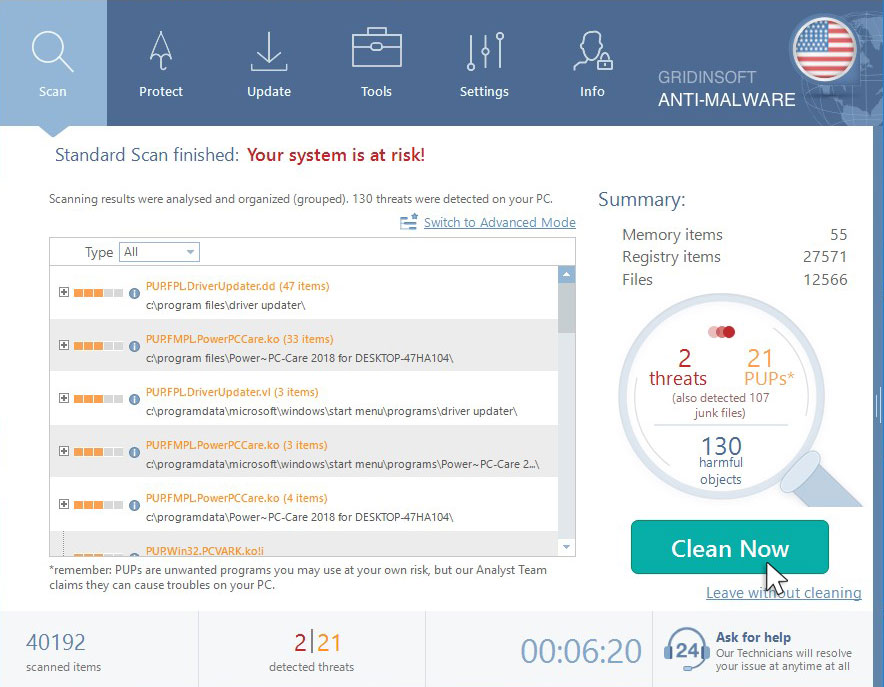
Click “Clean Now” to remove the threats detected by GridinSoft Anti-Malware.
Use Trojan Killer for Special Cases
If Nood ransomware blocks anti-malware setup files, consider using a removable drive with pre-installed antivirus software.
Very few security tools can install on USB drives. Those that can often require an expensive license. In such cases, I recommend Trojan Killer Portable by GridinSoft. It comes with a 14-day free trial that includes all features of the paid version, which should be sufficient to eliminate the malware. For more details, visit Trojan Killer Portable.
Video Guide
How To Decrypt .nood Files?
Restoring Large Files
If you’re dealing with large files (2GB or more), try removing the .nood extension and then attempt to open them. Due to encryption flaws, the malware might not encrypt or correctly mark large files, making recovery possible for these particular cases. Please share your experience in the comments to help others.
Recent STOP/Djvu variants emerged around the end of August 2019 after the criminals behind them upgraded their tactics. Consequently, STOPDecrypter became obsolete and was succeeded by the Emsisoft Decryptor for STOP Djvu Ransomware, developed by the cybersecurity experts at Emsisoft.
Access the free decryption tool here: Decryptor for STOP Djvu.
Initiate the Decryption Process
Begin by downloading the Emsisoft decryption tool. Remember to run it with administrator rights and agree to the license terms by clicking “Yes“:
Once you agree to the terms, the decryptor’s main interface will appear:
Select Targets for Decryption
The decryptor, by default, targets all accessible directories on connected drives, including network drives. Use the “Add” button to include any additional locations you wish to decrypt.
Depending on the ransomware family, decryptors may offer various specific options within the Options tab. Review and adjust these settings to suit your needs. Below, you can find a detailed list of these options currently available.
Begin Decryption
After setting your desired locations, press the “Decrypt” button to start decrypting your files. The interface will switch to a status view, showing real-time progress and statistics of the decryption process:
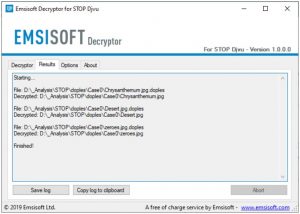
Upon completion, the decryptor will alert you. For documentation or further assistance, save the report by clicking “Save log”. This log can also be copied to your clipboard for easy sharing via email or messages.
How to Restore .nood Files?
Ransomware doesn’t always spell doom for your files…
The Nood ransomware employs a meticulous encryption strategy: it encrypts files byte by byte, duplicates them, and then deletes the original without overwriting it. This means the original file’s data isn’t erased from your drive. The sectors that previously contained the file may still have the data, even though it’s no longer part of the file system and is at risk of being overwritten. Fortunately, with the right tools, you have a chance to recover these files.
Despite the setback with my encrypted files due to an online algorithm, my backup drive, which I initially thought was fully compromised, held a surprise. Although every folder seemed infected at first, I was able to recover nearly 80% of my 2TB storage.
Digging deeper, I noticed the ransom note in each folder. Files directly within these folders were encrypted, but, interestingly, files in subfolders within these folders remained untouched. This pattern held true for my C and D drives, but my backup drive was different: having subfolders saved most of my data.
It seems creating subfolders on a backup drive can create a loophole. I was fortunate to recover an additional 10% of my data from another drive. My experience shows that structured data storage can inadvertently protect against such encryption.
This discovery might offer hope to others in similar predicaments.
Jamie Newland
Recovering Your Files with PhotoRec
PhotoRec stands out as a robust, free tool initially designed to retrieve files from damaged disks or to recover accidentally deleted files. Over time, it has evolved to support the recovery of over 400 different file types, making it a powerful ally in the fight against the Nood ransomware.
Begin by downloading PhotoRec. While the tool is completely free, its developer notes that file recovery is not guaranteed. PhotoRec comes bundled with TestDisk, another utility by the same developer. Despite the archive bearing the TestDisk name, rest assured, PhotoRec is included within.
To launch PhotoRec, locate and open the “qphotorec_win.exe” file. An installation is unnecessary as the program contains all required files in the archive, enabling its use directly from a USB drive—offering a handy solution for assisting friends or family afflicted by the Nood ransomware.
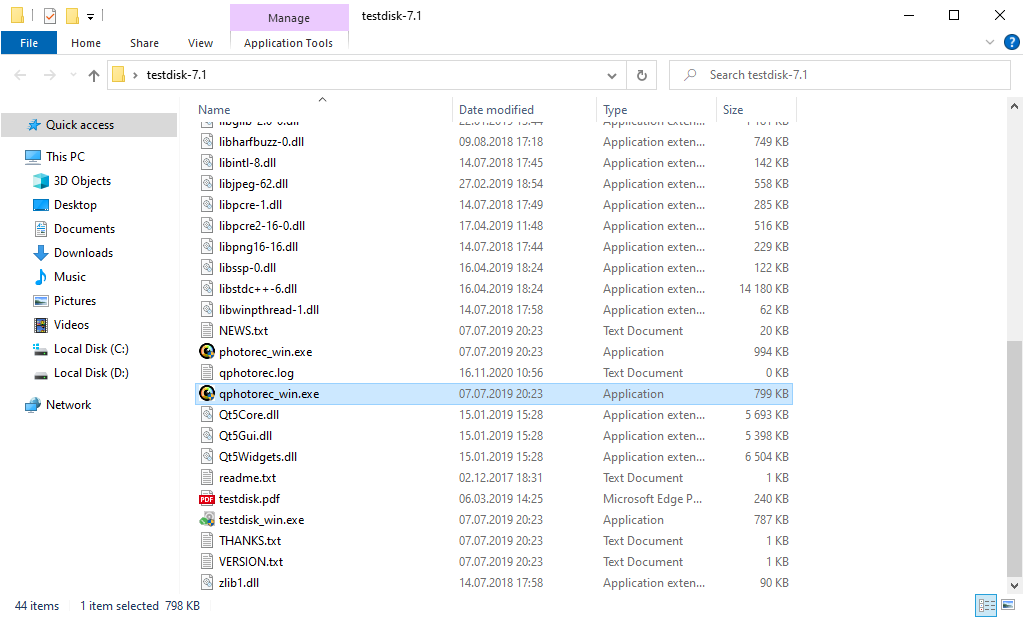
At startup, you’ll be presented with a list of drives. This overview might seem daunting at first, but the essential menu is just above. Click the bar to select the disk impacted by the ransomware.
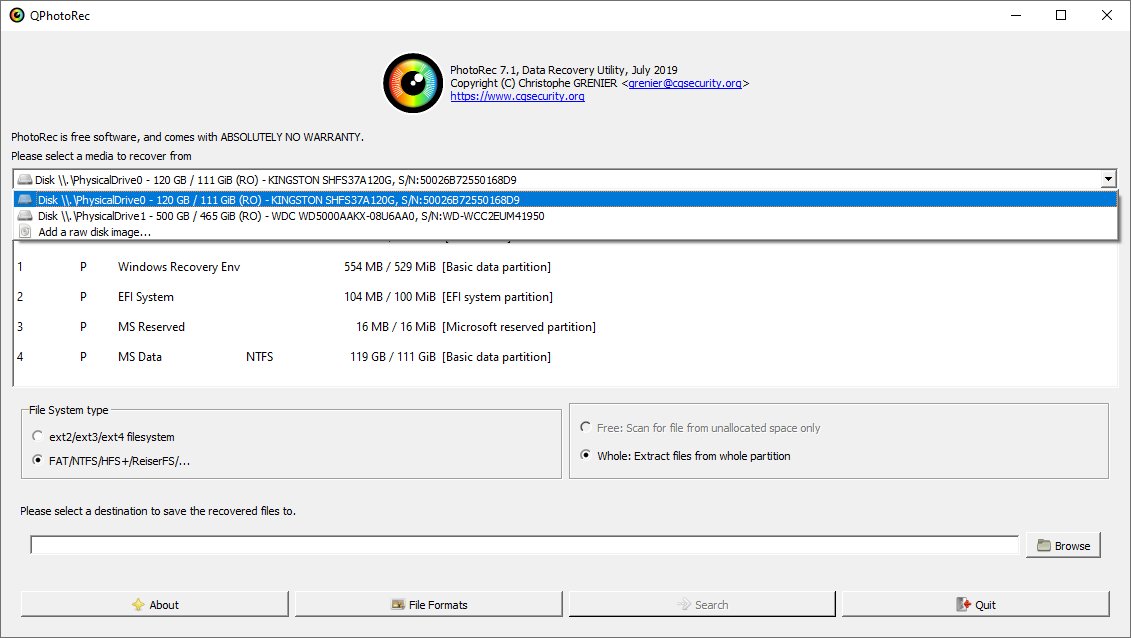
Next, specify the destination folder for the recovered files. You’ll find this option at the bottom of the PhotoRec window. Opting to save them to a USB drive or another form of removable media is recommended.
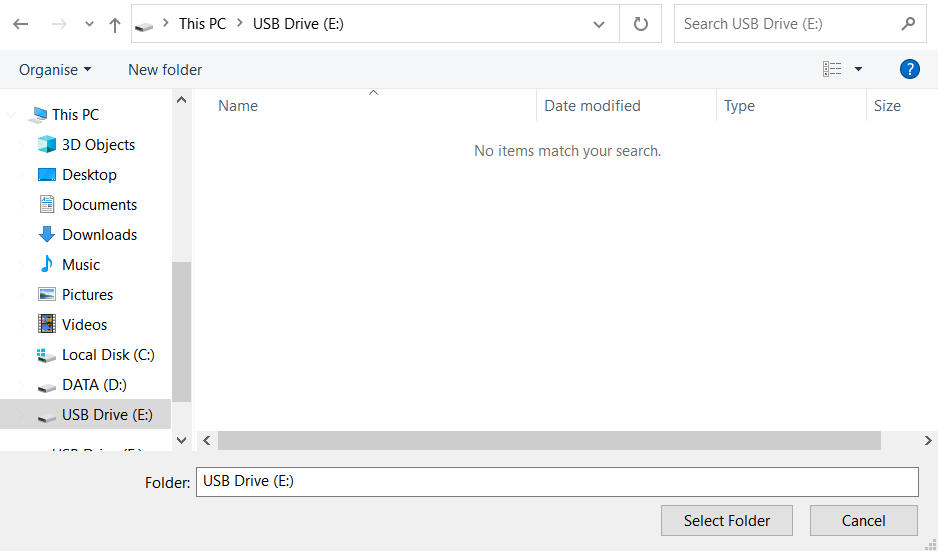
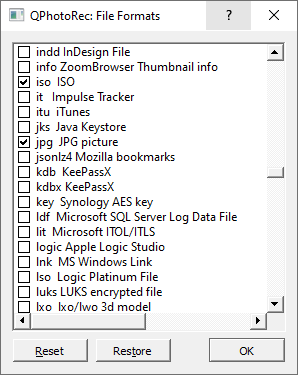
Then, select the file formats you wish to recover. This setting is also at the bottom. As previously mentioned, PhotoRec supports recovery of about 400 file formats.
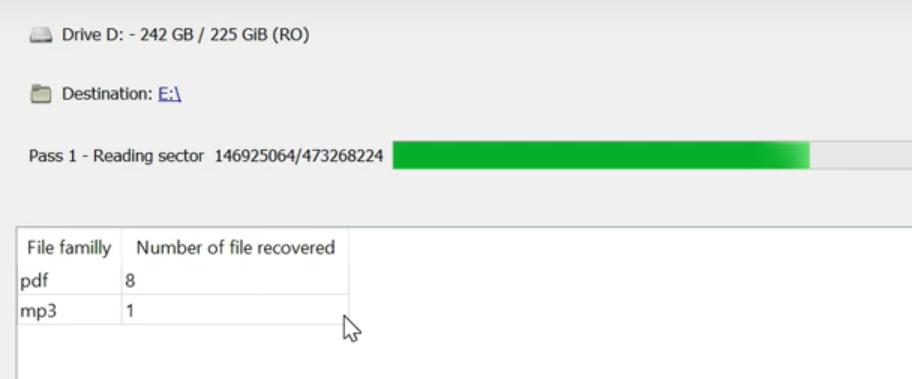
Finally, initiate the file recovery process by clicking the “Search” button. You will be directed to a screen displaying the scan and recovery outcomes.
Nood files recovery Video Guide.
Frequently Asked Questions
🤔 How can I open “.nood” files?
Unfortunately, there’s no direct way to open files with a “.nood” extension as they are encrypted by ransomware. You cannot access the encrypted contents without decrypting them first.
🤔 The virus has blocked my infected PC: I can’t get the activation code.
In such cases, you should use a memory stick that already has Trojan Killer installed. For more information, visit our Trojan Killer page.
🤔 The decryptor didn’t decrypt all my files, or not all of them were decrypted. What should I do?
It’s important to remain patient in this situation. If you’re dealing with a new version of the STOP/DJVU ransomware, the decryption keys might not be available yet. Keep an eye on our website for updates on new keys or decryption tools.
🤔 What can I do right now?
The Nood ransomware typically encrypts only the first 150KB of files. For example, some larger MP3 files might still be playable in media players like Winamp, minus the first 3-5 seconds due to encryption. To recover, you can:
- Redownload encrypted files from the internet.
- Request copies of shared pictures from family and friends.
- Retrieve photos from social media or cloud services such as Carbonite, OneDrive, iDrive, Google Drive, etc.
- Find attachments in saved emails.
- Look for files on older computers, flash drives, external drives, camera memory cards, or iPhones that were synced with the infected computer.
If you’re still struggling to remove the infection, I recommend downloading GridinSoft Anti-Malware. Your experiences and solutions are valuable to others facing similar problems. Please, share your story in the comments below. Your insights can offer hope and demonstrate that no one has to face this challenge alone. Together, we can find a solution.
User Review
( votes)References
![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian


