Stop/Djvu Decryptor is a specialized tool developed by Emsisoft, designed to assist in the recovery of files encrypted by the Stop/Djvu Ransomware. Stop/Djvu Ransomware is a type of malware that encrypts victims’ files using a strong encryption algorithm, making them inaccessible without the decryption key. The Decryptor tool aims to decrypt the files without having to pay the ransom to the cybercriminals.
The Stop/Djvu Decryptor
The Stop/Djvu Decryptor works by leveraging certain vulnerabilities or weaknesses in the encryption process employed by the ransomware. It attempts to recover the original files by reversing the encryption applied by the malware. The tool is regularly updated to address new variants of the Stop/Djvu Ransomware and enhance its effectiveness.
It is important to note that while the Decryptor has been successful in decrypting files for some victims, it may not work in all cases, especially if the ransomware used a particularly strong encryption method or if the files have been damaged. Therefore, it is recommended to always maintain proper backups of important files and implement preventive measures to protect against ransomware attacks.
What is Stop/Djvu Ransomware?
STOP/DJVU Ransomware encrypts victims’ files using the Salsa20 encryption algorithm, which is a robust cipher that poses a significant challenge to decryption without the correct key. The encrypted files are then given new extensions, such as “.bhui”, “.ahui”, “.bhtw”, “.bhgr”, among others.
The cybercriminals responsible for STOP/DJVU Ransomware demand a ransom payment to provide the decryption key needed to unlock the encrypted files. They typically leave a ransom note in the form of a text file on the desktop or within every folder containing encrypted files. The note provides instructions for paying the ransom and strongly advises against any attempts to remove the malware or decrypt the files without the proper decryption key.
It’s important to emphasize that paying the ransom does not guarantee the provision of the decryption key. There have been instances where cybercriminals failed to deliver the decryption key even after receiving the ransom payment. Therefore, taking preventive measures is essential to protect against ransomware attacks.
To safeguard your computer against STOP/DJVU Ransomware and other forms of ransomware, it is crucial to follow safe computing practices. This includes keeping your operating system and software up to date, refraining from opening suspicious email attachments, and only downloading software from reputable sources. Additionally, regular backup of important files to an external device or a cloud-based storage platform is highly recommended.
First and foremost, it is crucial to remove the malware from your PC to prevent it from locking your device or repeatedly encrypting your data. If your current antivirus software fails to remove this malware, you can use GridinSoft Anti-Malware to effectively delete it.
If your system was infected through the Windows Remote Desktop function, it is strongly recommended to change the passwords for all authorized remote users and thoroughly inspect local user accounts for any additional accounts that may have been created by online fraudsters.
Additionally, you can explore: 15 Reasons to Choose Gridinsoft Anti-malware
Warning: This application needs to be connected to the web while active to get the decryption guidelines from the server.
If you suspect that your computer has been infected with STOP/DJVU Ransomware, you should immediately disconnect from the internet to prevent the malware from spreading to other devices. Then, seek the assistance of a professional malware removal service to safely remove the malware from your system.
The Known Stop/Djvu Decryptor Updates
Updated 19 August 2021
The offline/private key for the .moqs variant of the STOP ransomware was added to the Emsisoft server.
Updated 12 Jule 2021
The .omfl, .geno, .nile .maas variants offline key was recovered by Emsisoft.
Updated 02 Jule 2021
The .sspq, .iqll, .ddsg variants offline key was recovered by Emsisoft. Any victims of these 3 variants that had files encrypted by the offline key can recover their files.
Updated 31 May 2020
The .covm variant offline key was recovered by Emsisoft and added to the Emsisoft Decryptor server.
Updated 01 May 2020
Emsisoft has announced that the offline keys for .opqz, .nppp and .npsk have been recovered and uploaded to the Emsisoft Decryptor server.
Updated 06 Feb 2020
Emsisoft has announced that the offline keys for .alka and .repp have been recovered and uploaded to the Emsisoft Decryptor server.
Updated 20 Jan 2020
Emsisoft Decryptor has obtained and uploaded to server new OFFLINE KEYS for the .nbes, .mkos STOP (Djvu) variant ransomware.
Updated 06 Jan 2020
List of the New Stop/Djvu variants for 148 variants that Emsisoft can decrypt.
.shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote
Updated 02 Dec 2019
List of the New Stop/Djvu variants that Emsisoft can decrypt. FOR OFFLINE KEY ONLY!
.gero, .hese, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .noos, .kuub, .reco, .bora, .nols, .werd, .coot, .derp, .meka, .mosk
Updated 25 Nov 2019
Emsisoft Decryptor has obtained and uploaded to server OFFLINE KEYS for the following new STOP (Djvu) variant:
.gero, .hese, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .noos, .kuub, .reco, .bora, .nols, .werd, .coot, .derp, .meka, .mosk, .lokf, .peet, .mbed, .kodg
Updated 9 Nov 2019
Decryptor v.1.0.0.1 by Emsisoft currently can decrypt NEW Stop/Djvu variant with file extension:
.gero, .hese, .seto, .peta, .moka, .meds, .kvag, .karl, .nesa, .noos, .kuub, .reco, .bora, .coot, .derp
Terms: Files encrypted with OFFLINE KEY.
There are certain limitations regarding what files can be restored. Speaking of all versions of STOP Djvu, you can properly decrypt the information if they were ciphered through an offline key available with the developers of the Emsisoft Decryptor. As for Old Djvu, the files can also be decrypted using encrypted/original file pairs provided to the STOP Djvu Submission portal. Keep in mind that this does not apply to New Djvu that was elaborated after August 2019.
What is a “file pair”?
This is pair of files that are identical (as in they are the precise same data), except one duplicate, is encrypted, and the other is not. STOP Djvu Submission portal can analyze the differences between an encrypted file and an original copy of the same file, allowing it to determine how to decrypt that file. For most victims with an older variant of STOP/Djvu, submitting file pairs will be the only way to get their files back.
Restoring Your Files
- Begin by downloading the decryption tool from the same website that developed this “How To” guide. You can find the DJVU Decryption Tool here: https://www.emsisoft.com/ransomware-decryption-tools/download/stop-djvu.
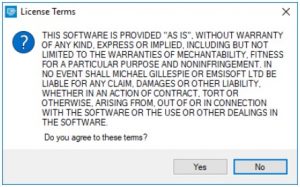
- Launch the decryption utility as an administrator and agree to the license terms by clicking the “Yes” button. Here is an example of the license terms:
- After accepting the license terms, the main user interface of the decryptor will appear. Here is an example of the user interface:
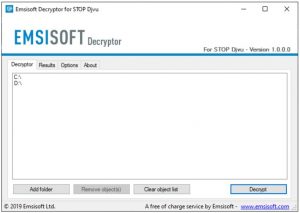
- The decryptor will automatically populate the available locations to decrypt based on the default settings. This includes the currently connected drives, as well as network drives. If you want to add extra locations, you can use the “Add” button.
- The decryptor may offer various options specific to the malware family. You can find the currently available options in the Options tab, where you can activate or deactivate them. A detailed list of the active options will be provided.
- Once you have added all the desired locations for decryption to the list, click the “Decrypt” button to initiate the decryption process. The main screen will display the status view, showing the active process and the decryption statistics of your data. Here is an example:
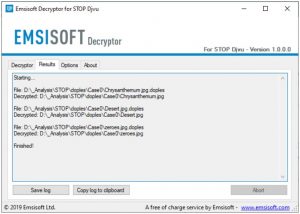
- Once the decryption process is completed, the decryptor will notify you. If you need a report for your records, you can save it by selecting the “Save log” button. You also have the option to copy the report to your clipboard and paste it into emails or forum messages, if necessary.
Decryptor options
The decryptor at this moment performs the following options:
- Keep encrypted files
Because the ransomware does not store any data regarding the unencrypted documents, the decryptor does not guarantee that the decrypted file will be identical to the initially encrypted one. Hence, based on the default settings, the decryptor will, for safety reasons, not delete any encrypted documents after they have been decrypted. If you would like the decryptor to delete any ciphered documents once they have been decrypted, it is possible to deactivate this feature. Note that this may be applicable if the space on your hard drive is limited.
Frequently Asked Questions
The decryptor requires version 4.5.2 or newer of the Microsoft .NET Framework, which could mean your version of the .NET Framework is out of date. We recommend installing the latest version of the .NET Framework (4.8 at the time of writing this) and then trying the decryptor again.
When you run the decryptor, it looks for encrypted files. Therefore, it will say “Starting” until it can find some. If the decryptor remains stuck on “Starting” for a long time, this means it cannot find any encrypted files.
JPEG/JPG images have a format oddity that causes file pairs to be specific to each picture source rather than the file format in general. As an example, if you have pictures from two different cameras, and submit a file pair from the group of pictures from one of the cameras, then the decryptor will only be able to decrypt files from the camera that the file pair came from. Therefore, to decrypt all JPEG/JPG images, you will need to submit file pairs from every source you’ve obtained those pictures from.
It’s an indication of a DNS issue. Our first recommendation is to reset your HOSTS file back to default. Microsoft has an article about this:
https://support.microsoft.com/en-us/help/972034/how-to-reset-the-hosts-file-back-to-the-default
The STOP Djvu ransomware encrypts only the first 150KB of files. So MP3 files are rather large. Some media players (Winamp, for example) may be able to play the files, but – the first 3-5 seconds (the encrypted portion) will be missing.
You can try to find a copy of an original file that was encrypted:
- Files you downloaded from the Internet that were encrypted, and you can download again to get the original.
- Pictures that you shared with family and friends that they can send back to you.
- Photos that you uploaded on social media or cloud services like Carbonite, OneDrive, iDrive, Google Drive, etc.)
- Attachments in emails you sent or received and saved.
- Files on an older computer, flash drive, external drive, camera memory card, or iPhone where you transferred data to the infected computer.
If not, you can try to restore files through the system function – Restore Point.
Also, try removing the ransomware extension on a few BIG files and opening them. The STOP/Djvu ransomware read and did not encrypt the file or bugged and did not add the FileMaker. If your files are huge (2GB+), the latter is most likely.
How to decrypt DJVU Ransomware files? Emsisoft Decryptor
Name: Emsisoft Decryptor
Description: The STOP Djvu ransomware encrypts victim's files with Salsa20, and appends one of dozens of extensions to filenames. For all versions of STOP Djvu, files can be successfully decrypted if they were encrypted by an offline key. Unfortunately, this tool will not work for every victim as it can only recover files encrypted by 148 of the 160 variants. This will enable approximately 70% of victims to recover their data. For people affected by the remaining 12 variants, no solution currently exists and we are unable to offer further assistance at this point in time. For that those who find themselves in this position archive the encrypted data in case a solution becomes available in the future.
Offer price: 0.0
Operating System: Windows
Application Category: System Tools
User Review
( votes)

![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian


how can i decrypt.lokffile
my system is affected yesterday
Has you found any solution for *.lokf decryption?
i have been attacked by ransomware malware named as .grod but these decryption tool was unable recover i tried too many times but i have deleted all ransomware txt file note, but i have kept grod extension encrypted files.
Can you help me for solutions? how to decrypt (.nbes file extension). Decrypt tool plss send link
Do you get any solution for .repp or .alka ?
If you get ple. share the solution on my email id.
ALKA and REPP keys were uploaded to the server. Try to decrypt your files.
pls. help me Emsisoft decryptor error
File: D:\ADFC Thesis of Easter Sundie Go\chapter 1-Curriculum Vitae(1).docx
No key for New Variant online ID: Y0GUXVfDzXykUzjO1EA5Ijcdkx9kk0HVOFKOO2Mr
Notice: this ID appears to be an online ID, decryption is impossible
File: D:\ADFC Thesis of Easter Sundie Go\chapter 1-Curriculum Vitae.docx.maas
No key for New Variant online ID: Y0GUXVfDzXykUzjO1EA5Ijcdkx9kk0HVOFKOO2Mr
Notice: this ID appears to be an online ID, decryption is impossible
File: D:\ADFC Thesis of Easter Sundie Go\Cover page-Abstract.docx.maas
No key for New Variant online ID: Y0GUXVfDzXykUzjO1EA5Ijcdkx9kk0HVOFKOO2Mr
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
how to decrypt .lokf file
Can you help me for solutions? how to decrypt .leto file
如何解密. lokf 文件
Dear Sir please notify me when you find out the decryptor for .toec files
Help me recovery .peet file plz sir..
File: C:\Users\Intel\AppData\Local\VirtualStore\bootTel.dat.peet
Error: Unable to decrypt file with ID: Strrlu4I2lSR2MXSMhhjvtYyjDZoz2JeMnRC8Vlz
Please help me to decrypt .peet file sir.
thank you in advance….
Buenas tardes alguien encontró alguna solucion para los archivos encriptados con .peet por favor su ayuda
Please help me to decrypt .grod file
Please help me to decrypt .peet file
my laptop files are with .grod extension
can they get back ?
My Laptop files are with .grod extention
can they get back my files???
I tried all the steps for cleaning the disk but when I tried decrypting the files it’s giving me an error message saying ” File: C:\IAM\IDCard\@IAMIdcardReader\META-INF\mozilla.sf.mbed
Error: Unable to decrypt file with ID: M068r10e1jXXBvKaI0EEhsfcIcpGpSvtM7MMSb7C”
please help
How to decrypt .mbed file
Plz help for .rote file decryption
Hello Riaz,
Did you have OFFLNE or ONLINE key?
Please help me with .rote file encryption
Hi,
My case is the same .rote, how do I find out the key whether it’s online or offline?
Abrir no Google Tradutor
0187Asd374y5iuhld8vqlSswfRM10lCmckClRtShnwcsZaWzZnsPeYbt1 please help me with this.
I am affected with. mbed virus in 24 november. I formatted my hard drive to remove this malware but I copy my data in a flash drive. How can I recover this?
0187Asd374y5iuhld8vqlSswfRM10lCmckClRtShnwcsZaWzZnsPeYb(t1)
The 2 characters at the end of your ID indicated offline keys.
the decryptor should succeed.
How to decrypt with online key?
Your personal ID:
0187Asd374y5iuhldvNcHb6xYzdPYyT3OD2I8NPf4YVulG7KnSG6nOYnf
i got something like this.
Dear sir! How is offline or online key? I can’t decrypt .rote and .zobm file
please help me to recover my data I have infected with .mbed viru all data has renamed as ex.mbed
this personal id showing (lpDUUK8nM5OpJf4hschFRqUA1h6IdrS9m2G04O2u) this key is online or offline ?
The ROTE offline key was uploaded to the server. Try to decrypt.
Please help me to decrypt .zobm files
Thank you!
did you find how to decrypt .zobm file?
I have encrypted the files with .zobm, your program is not good!
The ZOBM offline key was uploaded to the server. Try to decrypt.
I have encrypted the files with .zobm
how can decrypt .mbed file …?
Hi, please help me to decrypt “.besub” files.
Sir brendan, mine is offline… but it did not work… for .mbed and .kodg
File: C:\Users\MW-568\Desktop\ELECTRICAL AS-BUILT (APPROVED)\TRAFFIC SIGNAL SYSTEM\plot.log.kodg
Error: Unable to decrypt file with ID: brxg3geyekANuxIrTK7UhCzXVlwB11z3QI4v0kLf
Por favor, ajude-me a descriptografar arquivos .zobm
Obrigado!
i cant decrypt my files (mbed)
Error: Unable to decrypt file with ID: e366ourl3OXCRQLmBMs7IyAMk8zXv7aAQne3jZib
PLZ help me sir
i have same problem!!! can you fixed?
hi, I was infected by zobm extension, can someone please help me decrypt them.
My Personal ID: 0186Asd374y5iuhldlFpXqCNILEQ3egDmMmSJFcHZvB3hGV5LIntUnXA6
How do you do it… can you help with me…???
i need help please
.msop
fls39xOIf6qVdhBxK3DV0CuhMLXIzFs9mdWxNNFu
por favor ayudenme a descrytar archivos .MSOP
Hi Team,
My system had been affected by .zobm,
Error: Unable to decrypt file with ID: DqK0BBnF9Lj28CUj6jDf8DraPSeyME7aNfULJQlL
But my id is “0186Asd374y5iuhldDqK0BBnF9Lj28CUj6jDf8DraPSeyME7aNfULJQlL”.
Can anyone help how can i update the correct id and try? it will work or not.
Please help.
Thanks
The error message of decryptor just indicates that the files where encrypted by an online key, and therefore, the decrypter can do nothing with it.
another posible solution please?
Any solution to retrieve data?
is there any solution? npsk online id
hello sir
I have covm files encrypted, I downloaded Emsisoft decryptor, but it appear a message:
File: D:\Folder nou\#Root\dȘâ\US\Manual\Manual facut\Manual Patchuri 1.docx.covm
No key for New Variant online ID: Aj4DYLhRbVif3awg5qwa8vVudb5q5xwYbQP7nnku
Notice: this ID appears to be an online ID, decryption is impossible
Is any chance to decrypt these files?
Is there any decryption tool foe MSOP ransomwar?
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-iLkPxViexl
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
datarestorehelp@firemail.cc
Reserve e-mail address to contact us:
datahelp@iran.ir
Your personal ID:
0188yTllsd1c0dEgAXI7DmdHxntxwyafMW9L2DVq497vdvdPl6
I booted up my computer as usual to find that all my files are .msop.
I was confused so I searched it up, then realized that all my family files around (400 gb) of family memories are all gone
Please help ASAP as these files mean the world to me
send me an email as i don’t usually use my computer
joshua.mabelin@gmail.com
Myall files are encrypt by .hets extension. Please help me to decrypt my all file.
File: C:\Users\hp\Desktop\BBS\070619 Waste segregation.docx.peet
Error: Unable to decrypt file with ID: TADFEt2RoicLhQUUei8fUrJqSwIxSDg3Ry3KvXZU
I have been caught by a ransomware named .hets and that’s the overall situation
Need help….
Windows 10 pro x64 v.1903
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-iLkPxViexl
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
datarestorehelp@firemail.cc
Reserve e-mail address to contact us:
datahelp@iran.ir
Your personal ID:
0189jYs9dfS4pspiucokZaYFFkd0QhLma3TMVtZDFJNH8tLPb
I need same help, please email me when you find a solution
I have the same issue ..Did you manage to have yours fix. What is the best solution
.msop ?
can’t decrypt .msop
my ID end by t1…. offline key
please help
I tried to decrypt the files infected by .hets, but the result are error..
Please how should i do ?
HETS file? When?
sir plz solution of .hets virus remove and data recover plz help me
when I decrypt Using emisoft it result
error: Unable to decrypt file with ID :
sir,
my computer was infected on 22nd july 2019 with .lapoi and .darus ransomeware and i tried all decrytors but alas ! still my files are infected and not able to decryt any of them. my pc was infected online.in every folder a readme.txt file is saved with the below message :-
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-o7ClqIH7RS
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
gorentos@bitmessage.ch
Reserve e-mail address to contact us:
gorentos2@firemail.cc
Our Telegram account:
@datarestore
Mark Data Restore
Your personal ID:
123Asd3768237Ihsdfz9OAcVW0tTCbzRDE1dGytwxFpoVPOL12P0ARrolw
Your personal ID:
123Asd3768237Ihsdfz9OAcVW0tTCbzRDE1dGytwxFpoVPOL12P0ARrolw
pls, do any solution for the same …. looking forward for ur response.
Thanking You.
Please help me to decrypt .rote file
To get this software you need write on our e-mail:
datarestorehelp@firemail.cc
Reserve e-mail address to contact us:
datahelp@iran.ir
Your personal ID:
0189jYs9dUAFLknMshpsJvvU4Q9TWd27sVXMX1va4SWlxklWH
Running the Decryptor says:
“Error: Unable to decrypt file with ID: UAFLknMshpsJvvU4Q9TWd27sVXMX1va4SWlxklWH”
HELP PLEASE. THANKS.
0191gtd374y5iuhldrUhvfOlyVNoWjzDKR6P2K6EsF1kmAQkdjf8jm1YU
pls help to decript gesd files
thx really much
.gesd & .merl
Unable to decrypt file with ID: faHY5b0rE7WF3812d6rLZyCH6MlfPpBd3R58Y9C5
Can you help me for solutions? how to decrypt (.nbes file extension). Decrypt tool plss send link
hi Mr.Brendan Smith
with .nbes extention file, how can i do? hep me please!!
Thank you!
please reply me fast
hi
ID: BgSbufbweoasiar1xS9SetDmQDtgAanmugnLL69Y
Hi.. pls help me.. what should i do
.redl extension files
Hey bro did u get a decryptor toold for it ???
Hi again, I also need to decrypt some photos, now they are all in “derp” format, how can I recover them?
Thanks
ID: HCeA2dNBm5NTYgkL55gwSkQX4KguAvx4SVr4UO5p
Help, I get an error in decryption. are with extension “GESD”
File: F:\rekening\TODDOPULI\NO7AIR JUL.pdf.redl
Error: Unable to decrypt file with ID: fqRUa75GWSCiRtQodikx9vMAvi2xauu0iAPjJPmA
Hey Bro did you get a decryptor tool for it ???
Can you help me to de-encrypt the file with .zobm extension and my ID is 0186Asd374y5iuhldJUhnz325rD0iy4qQ9YhPUBulvjVMxnl4I44ywrst
i download Emsisoft Decryptor for STOP Djvu but after download i cant open file , i get run as administrator and i wait..wait.. and still not open 🙁 i use win 10 pro help please
please help me
my folders and files are infected by ransomware ( .nbes)
I have tried all ways but no solution
please help me
Hi,
I was infected in ~Feb. 2019…but the tool can’t decrypt my files. any help?
Tnx
Your personal ID:
0176Asd374y5iuhlddoJEwqHhDfqtFKREYsWIi6RFomr2oPg8FJ9CEXxu
HELP ME,
My folders and files are infected by RANSOMWARE (.GROD)
Persnoal ID: 4TLM5qAxLgxdow9SRGNbjI0y1MkrjtsTam7eVlFF
please help me .redl extension not able to decrypt
Is there a decryptor for .nbes virus? If yes, please notify me.
My important files were captured with this one, I am incapable of presenting my final dissertation due to this.
Please help me!
please help me .redl extension not able to decrypt
personal ID: 0196Asd374y5iuhldJw8Bb06WDSMt3SMrfhkTPArAs6ocQJ2STPEtvO6z
Please help me decrypt files infected with .meds can’t open all my files. Thanks…
Hi,
how to decrypt .nbes ramsome ware, kindly assist
please help me to download any descriptor for .kodc file
ca marche pour NBES fil merci boucoup
ça marche pour NBES fil merci beaucoup
My PC was infected with .REHA
Unable to decrypt Old Variant ID: 7757TLxCRXnSjhJoq4TruFpvTlag0OKn6hPITYt1
thank you
When using EMSISOFT it show – Unable to decrypt Old Variant ID: 7757TLxCRXnSjhJoq4TruFpvTlag0OKn6hPITYt1
help me to derypt .rsp files
File: D:\6e7171a48b3a2533f7429377b4b6aa28_2.jpg.topi
Unable to decrypt Old Variant ID: c6pa3Xz0QpgVHBZGcq5lTIcEFNWiebhrsKnz2vxO
First 5 bytes: FFD8FFE000
Starting…
File: RosadosVentos.jpg.hets
Unable to decrypt Old Variant ID: UAFLknMshpsJvvU4Q9TWd27sVXMX1va4SWlxklWH
First 5 bytes: FFD8FFE000
But in the _readme says: ID: 0189jYs9dUAFLknMshpsJvvU4Q9TWd27sVXMX1va4SWlxklWH
Need some help for almost 3TB of data. Many thanks.
I am facing the same problem with TOPI. How did u decrypt your files.
.redl not working this toole and ans this No key for New Variant online ID: nDBk4AMcKuXwHwJGRUD0HgAP4UJPSDOgbjgBvoIO
Notice: this ID appears to be an online ID, decryption is impossible
Hey bro did u get a decryptor toold for it ???
help me out my old study notes project and my family photos which are really important affected by npsg virus 🙁 🙁 🙁 i used emisoft but it says its online key please help me my dad past away 5 years ago all his memories on my laptop
please decrypt file .repp
igual
Notice: this ID appears to be an online ID, decryption is impossible
when i tried this app? is there a way to decrypt online ID?
Unable to Decryption the .btos file.please send me solution or link.
Sir/mam, You have any solution to decrypt. gesd file type. Plz suggest me asap.
thank you so very much i wil no never be without antivirus thank you
File: C:\Users\Desktop\201106A0\24062011281.jpg.alka
No key for New Variant online ID: RhUB5Cg91VcscQRmYJFCqHYb9dTiO0CkgCrBQha2
Notice: this ID appears to be an online ID, decryption is impossible
it cannot work…
No key for New Variant online ID: WxIRjU4ROjh9Z4EjJJZDQITdLyZ3RJAtHTne2njZ
Notice: this ID appears to be an online ID, decryption is impossible
tengo criptado foto video con derp
Can you help me for solutions? how to decrypt .Npsg file?
My files are infected by .Bboo virus. I can’t solve, recover it. Does anyone can help me.
thanks in advance
Hi, I need BBOO Decrypt tool need,if someone now the solution please HELP!
This CHINESE HACKERS should be shoot on site. They are trying to find ways to earn money without sweating!
Same problem .. did you come up with any solution?
hello sir please help me..
File: C:\HP\DATA\HPSE\WMIEvent09.dat.alka
No key for New Variant online ID: jSQnM3MwSJizNx89zw4Kc1XHPy1JsSjVKqNAtvZd
Notice: this ID appears to be an online ID, decryption is impossible
solution please sir
My all data files affected with GESD extensions. Can you help me to decrypt my files. Thanks & Regards, Viru.
Dear sir,
Recently I have been caught by some ransomware what added extension after every file is .bboo for which I beg your kind help. I hope you can definitely give me some solution to recover my encrypted dada.
Millions of thanks in advance.
Please reply if anyone is able to decrypt .rooe files.
My PC have been infected with it and it is infected online.
Hello, all my data is encrypted by .rooe
How can I reverse this. regards
Please help
hi my computers have been infected with rooe files and am not able to recover them. please helpp
Can’t decrypt .btos and npsg files.
Used Emisisoft – message : “File: E:\$GetCurrent\media\boot\bootfix.bin.npsg
No key for New Variant offline ID: A9GoURN1YjdAQyaC6wsAFQH69tLYb2jZFkNvyct1 Notice: this ID appears be an offline ID, decryption MAY be possible in the future”.
Is there a decryptor available yet?
HI, my computers have been infected with mool files and how I can recover my file. please help…
I am not able to decrypt “.kodg” encrypted files using emisoft decryptor, it gives details that –
File: F:\2018\5_May\06_05_18_Melvin_Wanorie\extras\_49A1964.JPG.kodc
No key for New Variant online ID: gawPpPdQ9NjBw3duHo35lG9IeooBAhatXpUIaCgE
Notice: this ID appears to be an online ID, decryption is impossible
sir/mam do you have any solution for mool extension,someone add this extension to all my files,so now m unable to access my files.nd he demands 980dollars for deciption of my files
please sir/mam revert me back on my mail id
will be great help for me
thanks
plz help .nppp
I am not able to decrypt “.nppp” encrypted files using emisoft decryptor, pls help me
I am not able to decrypt “.nppp” encrypted files using emisoft decryptor, pls help me….
it seems impossible now, bye bye our files 🙁
The NPPP offline key was uploaded to the server. Try to decrypt.
Could someone please help me? I’ve been downloading decryption softwares and nothing is working. All of my files (audio, video and documents) now have .nppp extension. Please help ASAP!
Please .derp decryptor… I need it so much
Hi, I’ve been infected with this virus few days ago. Please help. 🙁
how to decrypt bboo files
sir my ransomware extension .lokd file so how can decrypt help me
lokd sitll doesn t decrypt….
Sir. please help me to remove .lokd extension file all of my pc file effect this virus please sir help me ….
please upload the key to decrypt all of my file please
please help me to decrypt .lokd files
Dear Sir,
Thank you for your good job, hope u doing alright. Recently I have problem with this ransomware (.remk) file extensions, do you have any way to recover my files that had been infected? I beg your kind help and solution for this problem, thank you
I have same problem now need back my files, all .remk….. what i do? Can recover my files, any idea or software… or just need…..
The REMK offline key was uploaded to the server. Try to decrypt.
please help me to *.opqz
Starting…
File: C:\Users\Administrator\Desktop\Virus\CHÚ ÐI N T3.20.xlsx.opqz
No key for New Variant online ID: mbv3S0tykETtrMLvqJTflIwXUSYX60CEzyS96oT9
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
Same attack here that of .opqz but unfortunately,it is new one .just wait…
Hi Jame
Also my computer was infected with this OPQZ and until now browsing forums I have not got any solution because it is a very new infection and nothing has been developed yet, please if you know something new contact me.
The OPQZ offline key was uploaded to the server. Try to decrypt.
MY FILES TO ENCRYPTED I CANT ABLE TO FIX THIS PROBLEM
pls info if can decrypt.opqz file… for avi,mp4,mkv,jpg,png,wav,mp3..
i hope who has creator djvu die fast and get corona until his ass cant drop shit!!
Some mp3 files change the file extension .ac3 and try again I saved a few files this way…
please help me please replay me how this problem solve ?????
Your personal ID:
0216OIWojlj48LdObY9KraS1JklIsTmpBaZbObayiV0YMzrFI33ld
and systm id : – LdObY9KraS1JklIsTmpBaZbObayiV0YMzrFI33ld
You have the online ID
I have the same problem. I’v been assigned the ID: 0216OIWojlj48r25obRZiIaEBLDVSM1zNIdlDpYXPcTcgCylBfJ0R
my files have .opqz file extension. Please help
You have the online ID
I have the same problem. Please help to decrypt.opqz file.
I’v been assigned the ID: 0216OIWojlj48zmgd82h65FItjbl56ff6P5GS3sZpZ1qEEGUOW6t1
The OPQZ offline key was uploaded to the server. Try to decrypt.
Unable to decrypt Old Variant ID plz help me
No key for New Variant online ID: QZsmCtMRQsHJI9S3kCmTMJcYYuchGKSq4vf1ANfO
Notice: this ID appears to be an online ID, decryption is impossible
You have the online ID
Sir
My system all files have extension is .opqz
online id is 0216OIWojlj48y8OKOeY019EXVTpqeQpCWMvGtcsR87Q0APwLamX2
please help me to recover my files .
You have the online ID
No key for New Variant offline ID: zmgd82h65FItjbl56ff6P5GS3sZpZ1qEEGUOW6t1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Plz help me
.opqz file extension
Same me .oqpz
but Your personal ID 0216OIWojlj48zmgd82h65FItjbl56ff6P5GS3sZpZ1qEEGUOW6t1
Do you find other option to solve decrypt file ?
You have the offline ID for the .opqz DJVU variant. However, Emsisoft has not yet recovered your offline/private key.
I can suggest you run the Emsisoft Decryptor on a test every week or so to check. Sorry to say, Emsisoft does not announce the recovery of keys.
please do let me know the soultion for .mado files
The MADO offline key was uploaded to the server. Try to decrypt.
my ID is quite similar to yours..same here
my pc is infected with .npsk
please help me with it
I have the same problem of opqz encryption in my pc. Please help to decrypt.opqz file.
I’v been assigned the ID: 0216OIWojlj48npXJWw5reazFSg6X5eauvduAP3ltj79mDgIp3TX4
my email-rahuldeeprastogi@gmail.com
This is an online key. Please, re-read this article.
sir this tool is not working in .npsk they give error {Error: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel}
Do You solve it and decrypt files?
No key for New Variant online ID: t9JCognUsMIypySTmYjZYEXE7jkXowJkouRKoz86
please help me Please help to decrypt .mado file
This is an online key. Please, re-read this article.
I am unable to decrypt .npsk ransoamware file and still I didn’t find the solution to decrypt it
I am unable to decrypt .mado ransomware file and still I didn’t find the solution to decrypt it
i am also facing same problem did u find the soltuion
can’t decrypt the ransomware
My assigned id : UwkABnHYkA914bGLBWvfvxkToFnX09w7CqZJtCPD
This is an online key. Please, re-read this article.
I am unable to decrypt .mado ransomware file and still I didn’t find the solution to decrypt it.
ID 0217OIWojlj48PRitd7mGCXedyVbaLKpudjTwfMdDgU6xY5vkM5Af
This is an online key. Please, re-read this article.
please help me to download any descriptor for .rooe file
pease sir
my total maraige photos thair shwoing jpg.rooe
this id sir
Your personal ID:
0206Sue883jP05WHgQmTH8GmScn0w2ZGrv4LQM2eLLG7ZY6eBMP
This is an online key. Please, re-read this article.
I am infected with .mado file extension with the personal email id of ransomware is 0217OIWojlj488TaHEsq5r7cNJKbYdWseLEB2pW1FuZKoKjKg5tt1
i have used emsisoft decryptor but it is not able to decrypt the .mado file extension.
please give some solution.
Anticipatory Thanks
It means that Emsisoft Decryptor has not yet recovered your offline/private key.
I can suggest you run the decryptor on a test every week to check updates and also make subscribe to this topic.
how can i restore my file encrypted with .mbed virus online
0184Asd374y5PieQsOiY3PUreyonDuSZb1ZZr2skTL4iCQjnLTuA
pleas help me
No key for New Variant online ID: setuHku5yJsRkpgglGfZ2RoB7b27HQHrPXAeUI8Y
Notice: this ID appears to be an online ID, decryption is impossible
how can i restore my file encrypted with .jope virus
please provide solution .
No key for New Variant online ID: 2D9zxz5AhgV2hcJxqUUpT6KFSvsn96zh3uX6Ea14
Notice: this ID appears to be an online ID, decryption is impossible
Sorry, this is online key. Use Restore Point: https://howtofix.guide/system-restore-point-windows-10/
I did that, it doesn’t work. still have my files encrypted
.jope
.jope
Please! Help Me!
No key for New Variant online ID: K1Ah3dB5pNmTunDHxZdW9Oe2I7cXbTt8sVQB1lqg
PLease .jope
mi ID zxOc8wfnTgY4EdUn0raPkXlPNLkBiCZHOKI4PGF7
I had the same situation
No key for New Variant online ID: f9bB0P6EdYToC94gXkr6UwtCyUY1QR8ZyU2AAvte
Notice: this ID appears to be an online ID, decryption is impossible
Error: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel
how to fix it? decrypt *.mpaj files
Error: Połączenie podstawowe zostało zakończone: Nie można ustanowić relacji zaufania dla bezpiecznego kanału SSL/TLS.
Your computer doesn’t support TLS 1.2 and assuming you have Windows 7 or older. You need to install updates.
Update Date and Time of your PC to the current version.
How can I recover my files from .mpaj
help my computer has been infected with .mpaj I can’t open my thesis to graduate help please
Starting…
File: C:\Users\ODIP\Desktop\12\flat hisab new 2018 Final .xlsx.horon
Unable to decrypt Old Variant ID: 9gpBuRZBb2otmKGynbS4FRztoc8nXMmXhua1a50S
First 5 bytes: 504B030414
File: C:\Users\ODIP\Desktop\12\New folder\flat hisab new 2018 Final .xlsx
No key for New Variant online ID: 9gpBuRZBb2otmKGynbS4FRztoc8nXMmXhua1a50S
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
STOPDecrypter v2.2.0.0
OS Microsoft Windows NT 6.1.7600.0, .NET Framework Version 4.0.30319.34209
—————————————-
No key for ID: 9gpBuRZBb2otmKGynbS4FRztoc8nXMmXhua1a50S (.horon )
Decrypted 0 files, skipped 35
How can I decrypt. Mado files ? Files are encrypted on March 26, 2020
The MADO offline key was uploaded to the server. Try to decrypt.
I have been caught by a ransomware named .qewe and that’s the overall situation
Need help….
Windows 10 pro x64 v.1903
Can I get help?
Hi,
My Pc infected with .npsk, its shows its online encryption. Any option to recover online encryptions of .npsk?\
Thank you
hey, PLEASE HELP ME WITH encryption file of (.MPAL). my system got encrypted with that.
need a decryption for that urgently.
File: D:\FORMATED.GHO.mpal
No key for New Variant online ID: rh1qUzWaDsfgpTKz2pYqmuXLOjE5CDPWAlHX6qIK
Notice: this ID appears to be an online ID, decryption is impossible
After removing the malwares, just identify if it your .mpal is caused by offline and online key, then you can follow how you can decrypt those files
it came through the offline source.
and where to follow for decryption?
can you help over it ? please
File: C:\Users\Administrador\Google Drive\Multi-Tecno\Ventas\Yolanda Maldonado\Cotizacion Y-3.xlsx.jope
No key for New Variant online ID: P0eOhnd8ngvTuxAsIEAsaXdDKD7WU56jNXqYNK91
Notice: this ID appears to be an online ID, decryption is impossible
File: F:\VK Thesis\~$nposis PVK 17.09.18.docx.mpal
No key for New Variant online ID: stWzlGwlnICmiZYloGpiDubQdt7NoYMWbwcvkXtL
Notice: this ID appears to be an online ID, decryption is impossible
ayuda es en Linea Your personal ID: 0223yiuduy6S5dexcBEMKeUBkpr7BuEQDsfzasegK4CjHSJJRr1TSK
Hi,
PLEASE HELP ME WITH encryption file of (.MPAL). my system got encrypted with that.
need a decryption for that urgently.
PLEASE HELP ME WITH encryption file of (.MPAL). my system got encrypted with that.
need a decryption for that urgently.
No key for New Variant offline ID: HXrY0WMqvNQvSwO4TneG0C9cVMtVYLf0bH8uYft1
please help me
AYUDENME POR FAVOR CON ESTE ARCHIVO DE ENCRIPTACION DE (.SQPC) se encripto en mis archivos ,muchas gracias.
Sir please help me to decrypt .msop files . Please sir. I lost the collection of my data of almost 10 yrs.
hi ,sir
my file is encrypted with .sqpc
i have tried many tool even Emsissoft decryptor tool
but says it is encrypted by online id.. what to do thanks in advance
ID: P5nX7Bn5hBSluanjfYTPTJ0orjZBuzc5rMoBQ8k
saludo el motivo de este mensaje es que necesito de su ayuda para poder descripar unos documentos sqpc por favor necesito de quien me pueda ayudar gracias de ante mano.
my all foto and videos affected by this virus, not opened or working in any other system, how to fix it plz give me solution for removing this kind of virus (.LEZP)
How to decrypt this all .koti file
please guide me
Your personal ID:
0226yiuduy6S5dXv0eeunhZkcimRYNvtuPCyPbJdBRkQvqrqadQtFn
How to decrypt this all .koti file
please guide me
Hola buen día
tuve el desafortunado inconveniente que fueron cifrados mis archivos con extension .covm…
he implementado su herramienta pero no logro tener exito.
como puede ayudarme??
Saludos
The COVM offline key was uploaded to the server. Try to decrypt.
All files have been infected. No original files left that is not encrypted by lalo ransom ware. Do i have a chance to recover my very valuable Cinema 4D files?
i am not able to recover my files using https://howtofix.guide/download
or https://howtofix.guide/how-to-decrypt-djvu-ransomware-files/
Hi, Please Help am getting this
File: C:\Log\Traces.svclog.covm
No key for New Variant online ID: gTOQgYioXCxN77aYoe2engnvh9KcybW80GBhIEY5
Notice: this ID appears to be an online ID, decryption is impossible
did you recover the files?
no. my file not recovered
I hope you are good. I read all your reports. I have the sqpc extension virus and the decryptor stays on starting forever. I have many files that are the same as those infected and others that are virus free. Maybe I can serve you. How can I decrypt them.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important
You can get and look video overview decrypt tool:
https://we.tl/t-xcn1Dtzak4
Price of private key and decrypt software is $ 980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $ 490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@firemail.cc
Your personal ID:
0224yiuduy6S5dzRj1asfMIEWMODgopOBeKg1tlypdKqtZ9pBlZUjB
_readme.tex.98R4rqWlp9
File: D:\123654\u.zip.mzlq
No key for New Variant online ID: D9hEU3zvAJIDPsHwU6A0R83ub5StlkNU4wLAbl82
Notice: this ID appears to be an online ID, decryption is impossible
i have been attacked by ransomware malware named as .pezi but these
decryption tool was unable recover, i tried too many times but
it was in vain
please help
i have been attacked by ransomware malware named as .pezi but these
decryption tool was unable recover i tried too many times but
it was in vain
please help me .. i need a tool to decrypt .pezi files
this is the message appeared while attempting to decrypt pezi files
Starting…
File: D:\test.docx.pezi
No key for New Variant online ID:
9hKhIXzx1QiC5b1Jjt22LC8CVMUV7kyUscrSZqUv
Notice: this ID appears to be an online ID, decryption is
impossible
I am being hit by this “.nypd” extention
Plesase help me…
How can I clean my files with NYPD extension. Pls help me.
pls help me
my files with NYPD extension
how can decrypt ( zwer ) file
i have a problem with ransomware, all my file become .koti, how to recovery my file 🙁
I had tired to download the tool and use to decrypt .qewe files but it resulted as below.
Would you help me to decrypt .qewe files?
My personal ID:0222yiuduy6S5dAeUxwq75PdfoF4svCs3X3Ni1awcbnvFaRKhl3I80
Hello,
My PC has been enfected by the same virus
All of my files format have been changed to .kkll format
Please I want help decrypting and recovering back my files !!!
Bilgisayarıma .moba virüsü bulaştı.
Kişisel ID: ZE6IOfL40kInTL9uwsAJVdKlX3ttTwoZXKTGSnny
Lütfen yardım edin.
txt dosyası içinde yazan kişisel ID: 0236yiuduy6S5dZE6IOfL40kInTL9uwsAJVdKlX3ttTwoZXKTGSnny
Eu estou com um Vírus ransomware que renomeou meus arquivos com extensão .Pykw alguem tem o descrypt. ex para me vender ou me ajudar por favor, até o preço do resgate é caro.
Todos os meus arquivos foram sequestrados e agora estão .pykw busco uma solução :'(
Oi tudo bem? Fui infectado pelo mesmo em data semalhante. Já achou algum descrypt para o pykw? Estou na procura e se achar algo também te aviso. Abs
My Pc was Attacked by .zida
& it can encrypt my all data
can u help me for decryption my data
File: D:\TEMP\sale_01.xls.zida
No key for New Variant online ID: U50zCTuRfsHxaq8zqJjSSqZxO72iEucl2NsM4VmV
Notice: this ID appears to be an online ID, decryption is impossible
Hello Sir,
Please help me. All my files are infected with “.maas”
Hoping for your help in decrypting this one.
Thanks!
The MAAS offline key was uploaded to the server. Try to decrypt.
pleaee provide latest decryptor for zida
File: J:\Drown camera lucky Studio 14.2.19\DCIM\100MEDIA\DJI_0006.MOV.mbed
Error: The remote name could not be resolved: ‘decrypter.emsisoft.com’
.mbed error please give me the solution
Help me recovery .peet file plz sir
i have .pezi id online can’t restore data, anyone have decrypter ?
Could you help encrypting .hits files with online key
plz help us
solve a problem
Please, you made a new ransomware decraftor of ‘.kuus’ file
I got infected KUUS ransomware
Please help me to recover my files.
please help me, i register for free trial
I got this error
File: C:\Users\talha\OneDrive\Desktop\OOP-Final-Practice\OOP-Final-Practice\Debug\Source.obj.erif
No key for New Variant offline ID: FgNvm19dtGwiAeo0E1PMle6iyL3YnoVnx73sG5t1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
How can I fix it ?
please help
Is there a program that decrypts the .REPL virus?
ZIDA Extension files affected
With online System ID
My data files harmed with a ransomware and all extension is .vari I try many programs like Emsisoft and other to decryption them but it was useless. please help me how can I repair my data. thank you
my personal ID:
0246jjhYhkkatQpRfpTf6bEEYHQxofqkrbRZ6xrCH6OD1M6h6t1
I have the same problem and many files in 3dm format have been transformed into .vari, more than 10 years of work, this is a damaged life and many prejudices, I need urgent help!
I have followed the web page step to decrypt the data file but dosen’y work and have the follow massage:
Error: No key for New Variant online ID: tqP8yRh8ilTIyhziYklmxmEpIQdvzPveXRfT8bGQ
Notice: this ID appears to be an online ID, decryption is impossible
please kindly help me how can I repair my data. thank you
dear sir please devlop your decryptor tool with below personal id
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
0236yiuduy6S5dOJk5srilRceswmzVXA5lL4wsE5PMLIhkgsGfHi1W
i tray EMSI SOFT for recover my files bus when tray this so Always key Errar no match BMXU3osLf0t1IHX9twwCnDNfoPdybghBRSYDjYPD
plz help me for recover my data
thanks a lot
Is there any decryption tool .ERIF ransomwar?
Hello!I can,t decrypt virus .kolz
Please for .liyl
my pc is also infected with oonn extension pls how do i get my files back
i am also waiting for decrypter ;((
i wait too for .kkll
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7WqJh5indg
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
0258iodosadysp15U6nn6eoOEZx6PJWqk5t1mbFD0gM3Mb8EDHS
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7WqJh5indg
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
0257ad732hsdf6FdhJjHbkX8cnCTJTPT2t5ZXgjC81dCGLH1LUB8E
Please help all my files infected by mmpa virus
Mine too! Did you make any progress in recovering them?
Hi
My Pc infected by ransomware Stop Djvu with online key (PersonalID.txt end without t1) also all my files encrypted with .geno extension on the other hand I have not received an email or text (in my Pc) so please help me if you can
My files are changed to extenson “jdyi” and showing key “9kMq8lgGeWKHHxoz8T3XiRBjEba9qlDV0sS7Nzw5”. please help to recover the files.
please help me to decrypt .mmpa files…
I will continued follow up your good news T____T
My files are changed to extenson “zida” and showing key “0238yjnkjddrtivCJPUUiBI43u5tjP0bSk8FHrWeMIaCdkgSEZzi8”. please help to recover the files.
File: F:\x – file name-I.flv.mmpa
Error: No key for New Variant online ID: zZ9iuDfsZMc5Ks7MJTrLC5CB5DPhnC3Nf3QRMAm5
Notice: this ID appears to be an online ID, decryption is impossible
how can I tackle this ?/?
GridinSoft™ Anti-Malware i am sall but this MMPA files remover flies
file name-I.flv.mmpa My Error: No key for New Variant online ID: GL01SRnYz8voovPOGDSA8MryTOykuSQ1tZfKZLzq Notice: this ID appears to be an online ID, decryption is impossible how can I tackle this ?/?
No key for New Variant offline ID: ko5OlWVEcCbN2PFimi9sRYf7KxlaFMeZeUSB6Jt1
plz help!
Thank you!
Hello, I’ve just recently been attacked by the .agho ransomware… I’ve lost all my crucial files. Don’t know what to do since no decryption too seems to work!
idf2o3cXB1Ogyr6oGhvqh6q9m7zcN1rlCCxdmEQW here is my Id i have tried all possible solution but didn’t able to decrypt.
I really appreciate if anyone could help
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-72VNKmoPkb
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
File: E:\Download\test\decrypt_STOPDjvu.exe.vvoa
Error: No key for New Variant online ID: 9UXCgIqdbPiy7Ndk88RryYqqKwddzyOuZoICwN9a
Notice: this ID appears to be an online ID, decryption is impossible
I got infected .vvoa ransomware
Please help me
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-72VNKmoPkb
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
0263ergaXO7Q6YEQtudNQ1CqsmlYBMg1UX3YbRfyVCTIAx1M
And what about .rote..?? I just wait for 1 year but until now I can’t fix it please tell me if you done to offline key thank you very much
can you help me with .sglh?
hi frend SGHL encorpt files problem an selosan plzz
I’ve tried to remove the .weui extension for large files ( 2.6 GB) and its works !
But Smaller files didn’t work
larger files weui removal works fo me too. but smaller files have got online keys, so not working. Any way out?
Please help me!!
Error: No key for New Variant online ID: J9cfExzMGTYl64phpmCcDMidfrdv5OkbLbE49nWj
Notice: this ID appears to be an online ID, decryption is impossible
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-lYFGr2p9Fq
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
0266Orjk1yhRfSqWeBA2b86gZiJ0RS0tKBzND0nE9HUUS9yg
bonjour, j’ai été infecté par ce virus qui m’a renommé tous mes fichiers en .LISP
et le decryptor m’affiche
Error: Unable to decrypt file with ID: jfRE375bbiWnLBTtM3UcTQ93R1xtGIZyWmOW3Tq8
merci
the remote name cound not be resolved decrypter.emsisoft
My files locked by *.igdm.
Please help me to decrypt.
Your personal ID:
0270IsdeYIOjvMsq7KdOlSyzsu35yHMBUUFhjnrhjrNmvFND
Thank You!
please i need help really badly, i have been infected with .booa all my valuable study files have been encrypted please kindly help me. please
please i need help really badly, i have been infected with .booa all my valuable study files have been encrypted please kindly help me. please
i have infected by .omfl and i couldnt decrypt my drives so please help me about that
The OMFL offline key was uploaded to the server. Try to decrypt.
Error: No key for New Variant online ID: N94Si93cnZqtiyYak5pbuQWLuSYmYONvYDAN3HNf
Notice: this ID appears to be an online ID, decryption is impossible
Help me, please..
When I try to decrypt my .booa files, it displays
‘Error: No key for New Variant offline ID: oSZWVSqVSArAtf4LDkC3Gf64lWEirgNneB9hBct1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future’.
help me please , i have infected by .omfl and i couldnt decrypt my drives so please help me about that
i deleted the read me text, i dont know my case id with Emsisoft i was able to recover most of the files but many more files are showing as impossible to recover, what should i do ?
Hi , I need to decrypte all of my files, which is attacked by virus ransome family djvu ,sglh n The Id text is online. where can I get the decrypter,, Thanks.
Hi , I need to decrypte all of my files, which is attacked by virus ransome family djvu ,qlkm. where can I get the decrypter,, Thanks.
QLKM File (.qlkm) virus how do i remove that
Error: No key for New Variant online ID: NMls1lZOcg7f8upEjX5nqoNLLpxM4DVmTVYATCTo
Notice: this ID appears to be an online ID, decryption is impossible
And what about .rote..?? I just wait for 1 year but until now I can’t fix it please tell me if you done to offline key thank you very much
help me *.wbxd
help me *.wbxd
ID: 5FONv6KWxARn1ok9RZoo6RJmK7NolD8I5IZKoZud
Your personal id indicates that you have files encrypted by an online key.
Run the Emsisoft decrypter on some of your files. If it indicates “decryption is impossible”, you are out of luck.
Also, try to restore your files with PhotoRec
Help me I have serious problem! wbxd
ID
0276oPsw3BVGoXvat6iH3WhbYNV02JtI0Z5DhrxQ6KB0trQt1
Same problem here. Same key
0276oPsw3BVGoXvat6iH3WhbYNV02JtI0Z5DhrxQ6KB0trQt1.
Help!
If you ever get your files decrypted, please contact me, I will do the same for you buddy.
James
please add key for .pola virus
please
please
please
please
please
i got .wbxd . did you find any solution?
I have .Pola virus trouble
Please solution for this virus
Please please 🤦🏻♂️
Hi.
.coos
Please help me to decrypt.
Your personal ID:
ZJU7IRxCG6MLwPKp8Gwb1weSgBaCkRjCpnkBVDZN
Hi Brendan Smith
Error: No key for New Variant online ID: FhN9LH59NwQdHYertNsG0O7BHaQk1OqIoAhGBJl9
Notice: this ID appears to be an online ID, decryption is impossible
how to get rid of this .omfl ransomware ?
Hi.
.topi
Please help me to decrypt.
Your personal ID:
0200a7d6a8sdaBvMfzaFfoS75wdU3AYioQWz4mBQVljOvlXJEmRxz
I’ve been infected with .agho and I can’t recover the files since november 2020. when will AGHO key get available ?
hello..how to decrypt .igdm help me please and thx in advance
Error: No key for New Variant online ID: eyo08gmfrnPog7C6ArBGgzFqEQlcGtGhPAaD9sEi
Notice: this ID appears to be an online ID, decryption is impossible
Please help me to decrypt .ytbn file
My PC is infected by .cadq Please help me to decrypt .cadq file
zwer extension ransomware how to decrypt plz
Please help me to decrypt .urnb file
My ID is :
0292ASd54hgfr6tKhWZrBxiwYTmYJSgfQhCZuvKtJjsDhhYOXwhL
please help me to decrypte wrui. Its showing…
Error: No key for New Variant online ID: gv85KN20F3Tqvj07rhvpaI7j7QRg473ZFS0D60Na
Notice: this ID appears to be an online ID, decryption is impossible
Please help me to decrypt .urnb file
Hi
Has a WRUI file decryption utility been found?
All my files have the WRUI extension added, and I removed the virus and used the available tools such as EMSISOFT to decrypt the encryption. Unfortunately, this message appears
This ransomware may be decryptable under certain circumstances.
I matched the encrypted files with the unencrypted files and this message popped up
Source: https://howtofix.guide/how-to-decrypt-djvu-ransomware-files/
Please refer to the appropriate guide for more information.
Identified by
sample_extension: .wrui
sample_bytes: [0x15891 – 0x158B7] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
Click here for more information about STOP (Djvu)
Error: No key for New Variant online ID: Rd9pKmGf8Muz6Rah80ojqTm6rxUaqksm6CUSNst6
Notice: this ID appears to be an online ID, decryption is impossible
I wonder what the solution, please help
All my files have the WRUI extension added.
Error: No key for New Variant online ID: dk9Ki0BWtDF1RAlTAs8RKhki8DJNymN038N6Vrej
Notice: this ID appears to be an online ID, decryption is impossible
please help
how can I decrypt files with .pcqq encrypt?
se llego a infartar mi pc y mis documentos estan con la extension de .pcqq ayuda por favor es urgente.
impossivel decrypt .PCQQ
please help me sir
File: E:\DL\Prasanjit Pradhan\voter.pdf.igvm
Error: No key for New Variant online ID: J0JgOYy268MEMUosB1eqsMCE4HZkBbA2A6BkmaPH
Notice: this ID appears to be an online ID, decryption is impossible
.igvm virus please help to get rid
Permisi, tolong singkiran virus IGVM ini
i need help please.
.ehiz is attack my file
Error: No key for New Variant online ID: zR8PRUBHBAkL4TgSeq8oikIx0sUFnJZbv2IYCkDv
Notice: this ID appears to be an online ID, decryption is impossible
I have the same prob. i think in future is possible to decrypt. think positiv
my .rejg file cannot repair, show is online key
Error: No key for New Variant online ID: JISHMuIukDUurRnL5et5snGk0C5mUJ4QdcYtEbb4
Notice: this ID appears to be an online ID, decryption is impossible
External hard drive infected with .pcqq virus hard drive 4 TB 3 Tb I recovered 1 TB virus how can I recover it please help me
File: E:\Recovered\Local Disk(E)\Existing Files\PF Customers list\Yogeshwar Bhuyar\WhatsApp Image 2021-04-12 at 7.40.28 PM.jpeg.ehiz
Error: No key for New Variant online ID: EOvFUJtXRqaNDbktQiRwWQKgvNtz8WzeTumhEOhK
Notice: this ID appears to be an online ID, decryption is impossible
How to solve this please help me
File: D:\startup 2 cara.txt.paas
Error: No key for New Variant online ID: LtXQeTd5Lq6aRmiSvVFPe6Ev22OmIMk5TvgwYfBz
Notice: this ID appears to be an online ID, decryption is impossible
any solution?
Is there hope of having new version of Stop DJVU soon?
File: C:\Cakewalk Content\Accoustic_0AC44.mln.paas
Error: The remote name could not be resolved: ‘decrypter.emisoft.com’
Sorry, does this means that there is a hope of decrypting my files in the future. And is there hope of having new version of STOP Djvu soon?
How to decrypt .padh ransomware?
I cannot find any decryption tool for this file format.
Error: No key for New Variant offline ID: dvQHMo0IXSevQni9AAQQ1xZ9UBSuYArpJOjiLLt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
please help me !!!
.mppq
hola ayuda con archivos .mppq este virus encrypto toda mi informaccion datos base de datos que tenia fotos documentos, etc ayuda por favor. muchas gracias
help me for pahd extension file i try alot of time Error: No key for New Variant offline ID
How to Decrypt My Files Which Are In QSCX Format?
My pc was attacked by .nusm but nothing working for decrypting my files as it is an online varient
External hard drive infected with .sspq hard drive 1 TB, howcan I recover it please help me
I have msg received below:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-eglcxvZv1s
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpteam@mail.ch
Reserve e-mail address to contact us:
helpmanager@airmail.cc
Your personal ID:
0304ewgfDdIJOb4PY4yurgeZJZmV91HlxVVkZkdrOr5r24Ty0p
how to remove ransomware that infect all of my file office and jpeg the ransomware add .IQLL extension
How to Decrypt My Files Which Are In iqll Format?
Please someone can help me, that my computer got infected by .mppq with variant id online
Please help me to decrypt .neer file
yess i also need help with neer
.neer fidye virüsü bana da bulaştı. Çözüm bulamıyorum. Eğer çözüm bulursanız ve bana da haber verirseniz çok sevinirim. Teşekkür ederim.
Please help me decrypt .pooe format.
Here’s what I’m getting when I tried to decrpy my files 🙁
File: C:\Users\Asus\Videos\Viddly YouTube Downloader\Bible #6 Worship Background Loops Full HD.mp4.pooe
Error: No key for New Variant online ID: AGrb4IRvBRdlO3rOPfbPtc02MlsPAmhRsieMYoqO
Notice: this ID appears to be an online ID, decryption is impossible
Is there a key for that one already available?
vcredist_x64.exe.pooe
Error: No key for New Variant offline ID: vm44NzSFuQur9eHklQ3YBUraVfy1szN1yvv5Jwt1
My System infected by .neer extension virus ransomware virus. I can’t find a solution. Can you please provide me the solution?
Thank you.
Haribabu
My System was infected by the .neer extension virus ransomware virus. I can’t find a solution. Can you please provide me the solution?
My personal ID: 0310ewgfDdIV9g5UKoQNTA81q6PdbaIl2bbLoR95iqyzpsXxqN
Thank you.
Haribabu
i need solution for online neer virus
Your personal ID:
0310ewgfDdRWE7GoImKgKc6jsWFtkedbhvoPTHt8w6DCO5Paio
pooe. file virus
e.g. Epubor_Keys\adobekey1585631616.der.pooe
Error: No key for New Variant online ID: 14o3TRN9o1CR8PcQYRsUrendtftqlHLkGpPNhEYN
Notice: this ID appears to be an online ID, decryption is impossible
can someone help me with this? would really appreciate it so much!
hola podrían salvar mis ficheros
File: C:\logWSVCUUpdateHelper.log.qscx
Error: No key for New Variant online ID: absr86iD51kFxVkD6s7Zvx8qauwarRwJMXVhBwna
Notice: this ID appears to be an online ID, decryption is impossible
Hi
My Pc infected by ransomware Stop Djvu with online key , also all my files encrypted with .zzla extension
is there any method to decrypt the files affected.
Error: No key for New Variant online ID: acjGW88SwuMMaoYgUs8dEMX2p5CuJmm6kxkEu6SS
Notice: this ID appears to be an online ID, decryption is impossible
Is there new update on the decrypter?
File: C:\Users\Enduser\.musixmatch\WMPRemoteStandalone.exe.zzla
Error: No key for New Variant online ID: acjGW88SwuMMaoYgUs8dEMX2p5CuJmm6kxkEu6SS
Notice: this ID appears to be an online ID, decryption is impossible
This is the sample error on the Decryptor
File: E:\jyothsna rajaswala photes\DSC_013 (1).JPG.vpsh
Error: No key for New Variant online ID: BXlbKSiXIMa3tovJRwvXKjBI2JLuPOo3Qyeoo9G7
Notice: this ID appears to be an online ID, decryption is impossible
My Total Hardisk was not working all my files pls help me sir.
this decrytpor is for offline ID only why keep messaging about online ID when they find a solution it will be posted….
hi
three days ago my computer was attacked by .zzla virus all format of file was changing to .zzla
I try every software but my file wasnt open
Im M.A student and my file is very important
if some one know please help me
i need help please virus .zqqw
ID= 0312ewgfDdvm44NzSFuQur9eHklQ3YBUraVfy1szN1yvv5Jwt1
Two days ago my computer was attacked by ransomware. I can’t open my files now. They all have a .zzla extension. I’m an undergraduate. So these files are very important to me. If anyone knows how to decrypt my files, please help me.
I need help please.
I was attacked by the virus and all my files on my pc were crypted and the extension changed to .gujd.
I tried decrypt_STOPDjvu but I got the following message
Error: No key for New Variant online ID: kkHj2BQgIaMIHzwqbC8DAxYCeHTbPbilhnbZgFH8
Notice: this ID appears to be an online ID, decryption is impossible
please help me :'(((
Que tal buenas noches quisiera su ayuda como puedo eliminar la extension “nusm” prove algunas cosas pero no puedo desencriptar mis archivos.
me sale este mensaje
No key for New Variant online ID: 0iNX0zeWaVUmHHA10PgG0XZ9zBlhryVJU9gpm45F
Notice: this ID appears to be an online ID, decryption is impossible
Gracias por la ayuda que me puedan brindar gracias.
Someone help me please, I was attacked by this virus that changes all of my data into .gujd extensions. I tried decrypt_STOPDJVU and got this message:
Error: No key for New Variant online ID: Wy2jZEa51rg35lktIuknV1J5v6y4Y8EDdQUhp6vs
Notice: this ID appears to be an online ID, decryption is impossible
Please help me, cause I’m in an exam this week, and I couldn’t open my task T_T
I can’t decrypt my files .gujd
Error:The remote name could not be resolved.
Any one can help me please..
Salut,
Mon ordinateur a subit une attaque ransomware en ligne par le virus (zola) dont l’extension est .zzla nouvelle variante, suite à l’installation du logiciel adobe flash player, le document readme contient le texte suivant :
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-mNr1oio2P6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
helpmanager@airmail.cc
Your personal ID:
0314ewgfDd58eBUZvVGfIoKRqxIWFMaHObzqfbAd8DxTSJOLMf
Alors que je sache qu’ il n’existe aucune solution possible pour le moment, prière m’informer toute fois il y’aurait une lueur d’espoir .
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-fhnNOAYC8Z
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
helpmanager@airmail.cc
Your personal ID:
0312ewgfDdDHoqyWZaMvxWt7GG6fTkWsmcAsMDpX6gjKLWIxsp
Le programme decrypt_STOPDjvu ne parvient pas à décrypter !!!
File: G:\101NC_D5_Artifou au château de Feluy_19-06-2021\DSC_2184.NEF.zqqw
Error: No key for New Variant online ID: DHoqyWZaMvxWt7GG6fTkWsmcAsMDpX6gjKLWIxsp
Notice: this ID appears to be an online ID, decryption is impossible
Merci d’avance pour votre aide, Willy
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-mNr1oio2P6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
managerhelper@airmail.cc
Your personal ID:
0317ewgfDdTxZnVLBRV5TExVtNLKKuNOhwlsssrlKImk98P6U8
i have format my hardisk directly but my other hardisk file are same problem, picture, movie, music all become ufwj
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-mNr1oio2P6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
managerhelper@airmail.cc
Your personal ID:
0317ewgfDdUcpVhu0hKecHRURIMB4U9e5HmOVF8ulAGujVM83H
Mes fichiers ont été crypté avec extension wwka, Merci de m’aider à trouver une solution.
preciso de ajuda para descriptografar .pahd alguem pode me ajudar??
preciso de ajuda para processo abaixo
File: C:\pai fone\IRNU0848.JPG.pahd
Error: No key for New Variant online ID: ajoVdl6TdrqOvQsswWXBPpDRUlNww5cqndUW2kZd
Notice: this ID appears to be an online ID, decryption is impossible
New virus file with .moqs
this is OFFLINE KEY
tried emsisoft decrypt but it still cannot decrypt this new virus
please help
I’m having the same problem at the moment. The Decryptor just says “may be possible in the future.”
NcBG8wI6Q1WFhUNlCRyjmrWGeGew2vvCKtJgKot1
gujd extension please help
the same extension
Your personal ID:
0317ewgfDd08ETpSqTrJS1paGVJ8Jci0RacpudDCLxtFN4KUpx
File: D:\All Softwares new.zip.moqs
Error: No key for New Variant online ID: rS7mIDd0oloY5nxomVIU4f1wX29CSB3AsNyTsndr
Notice: this ID appears to be an online ID, decryption is impossible
Hola.
Tengo el mismo problema, mis archivos quedaron con la extensión moqs-
Pudiste recuperar los archivos?
My Files are encrypted with .pooe extension..
personal ID:
0313ewgfDdjWsTmZ5swfTLnMdsEzIogWnahqfrh3GVBFR1WGil
Please help
Can you help me for solutions? how to decrypt .udacha123yes file
I have got the same problem with MOQS ransomware ( ID: cIpZzKiItXZqziNr56Ww17J3cySOWxcLgxxOAot1)
Please help
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-mNr1oio2P6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
helpmanager@airmail.cc
Your personal ID:
0315ewgfDdOFezpPxnkaW4toYSwwYmMyL2FNEL1vIsIkQN0QYQ
Please help me to decrypt .moqs files
Thank you!
I have encryption of .moqs files and its an online key. Please help because I have tried thousands of decrypter tools and hacks to get my data back. Apart from this, the only data that gets recovered is Jpgs which were never in your computer and a huge pile of.dll files.
Please Help!
Thank You!
Hola.
mis archivos quedaron con la extensión moqs-
Slguina manera recuperar los archivos? 🥺🙏🙏
Your personal ID:
0318ewgfDdU6f6lrBs5MldXLF54rpZ8CbKZWxWbrpADuzHJLD2
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-CnI3tI6Ktv
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
managerhelper@airmail.cc
Your personal ID:
0322gDrgoMsPgFiEgR63kgnLrG7Yb5Nl1NjGQsF2mgvahXI9X
I tried this emisoft recovery tool but it also denied to recover.
Please help me to decrypt .neer files
Your personal ID:
0310ewgfDdLTYv5JAYPKU9SqYbMp9sbHbkMoA4JlKc46dTaLt1
We have identified “STOP (Djvu)”. This ransomware may be decryptable under certain circumstances.
Please refer to the appropriate guide for more information.
Identified by:
ransomnote_filename: _readme.txt
ransomnote_email: helpteam@mail.ch
sample_extension: .ehiz
sample_bytes: [0x15B28 – 0x15B4E] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
Click here for more information about STOP (Djvu).
Case number: 34f22197c7907bc259190998f37d14eabf88f8581628451189
I cannot fixed .nooa file by Emsisoft, the software is show Error :
Error: No key for New Variant online ID: 2saUUn3Z7BTjIpC58vr03wiLifoCfNGZVIGXyTJ8
Notice: this ID appears to be an online ID, decryption is impossible
Please help and advise
Please help. I tried to decrypt *.reqg files with EMSISOFT Decryptor but it resulted with the following error.
Thank you in advance.
Error: No key for New Variant offline ID: ioYmb0jtMMtue7xjmkS3WQWGWLR8FTQhb2giQtt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Exactly the same symptoms.
I’m hoping for a quick analysis.
Por gentileza como posso corrigir este erro que aparece na mensagem quando uso o Emsisoft Decryptor for STOP Djvu?
Não consigo descriptografar os arquivos.
Erro: nenhuma chave para o ID online da nova variante: nDSFKfp1iv3xb69oH6SfoL7pAi2euxSIDXXhSjKC
Aviso: este ID parece ser um ID online, a descriptografia é impossível
al igual que a muchos, hoy me ha caído el virus STOPDjvu, tengo todos los archivos encriptados y no quisiera perderlos, tengo imágenes familiares que son imposibles de recuperar, y el programa emsisoft decryptor no me ha mostrado nada aún, existe otra solución a parte de este programa para recuperar los archivos?, en serio, necesito ayuda urgente, saludos
reqg şifreli dosyaları emsisoft ile çözemedim bana da yardımcı olurmusunuz ?
Hi, I’m also victim of ransomware which made my files extensioned .reqg, tried EMIMSOFT and many other decryptors but it was a online key that non was able to decrypt, need help in this regards please.
I will tell you from Japan.
(Since it uses a translation engine, please forgive me if it is difficult to read)
I also suffered from ransomware.
“EMI SOFT Decryptor For STOP Djvu version 1.0.0.5”
I tried to decrypt using, but it failed.
The contents of the console are as follows.
——————-
Error: No key for New Variant online ID: U1w5VbrkQiPKtOIO33nrpTOGh4vABS3w8BtcVhth
Notice: this ID appears to be an online ID, decryption is impossible
Please help with compounding.
Nooa virüsü çözümünü beklemedeyim.
Result: No key for new variant offline ID: [example ID]
This ID appears to be an offline ID. Decryption may be possible in the future.
All my archive files jpg, mp3, mp4, xls, docx etc are encripted by reqg extension. Related ransomware was cleaned by manually meantime, _readme.txt file is also gone. so I do not know if there was a personal id key or so. when tried to decrypt with Emsisoft tool, I get
Error: No key for New Variant offline ID: ioYmb0jtMMtue7xjmkS3WQWGWLR8FTQhb2giQtt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
So I copied all the infected archive to a separate external HDD and started waiting for a possible solution.
Do you think it is all right to delete all infected files from my laptop’s HDD?
The key for REQG ransomware has not yet been received. Now available for decryption only: gero, hese, geno, seto, peta, moka, meds, kvag, domn, karl, nesa, noos, kuub, reco, bora, nols, werd, coot, derp, meka, toec, mosk, lokf, peet, grod, mbed, kodg, zobm, rote, msop, hets, righ, mkos, nbes, nosu, reha, topi, repp, alka, nppp, remk, npsk, opqz, mado, covm, usam, tabe, vawe, maas, nile, geno, omfl, sspq, iqll, ddsg.At the moment, the key for this ransomware has not yet been received. Now available for decryption only: gero, hese, geno, seto, peta, moka, meds, kvag, domn, karl, nesa, noos, kuub, reco, bora, nols, werd, coot, derp, meka, toec, mosk, lokf, peet, grod, mbed, kodg, zobm, rote, msop, hets, righ, mkos, nbes, nosu, reha, topi, repp, alka, nppp, remk, npsk, opqz, mado, covm, usam, tabe, vawe, maas, nile, geno, omfl, sspq, iqll, ddsg.
I need help opening .hoop files Please help me
Archivo: C: \ Users \ profo \ OneDrive \ Escritorio \ Caja chica3.xlsx.pcqq
Error: No hay clave para el ID en línea de la nueva variante: lCjB9ZsGWWIEEe2Y3rHjdhaMHqZrBJgu502icL16
Aviso: esta identificación parece ser una identificación en línea, el descifrado es imposible
¡Finalizado!
el decrupt-SOTPDjvu.exe no sirve para nada es pura falsedad llevo tres meses intentando desencriptar un archivo chica3.xlsx.pcqq y sigo sin poder encontrar algo que funcione
At the moment, the key for this ransomware has not yet been received. Now available for decryption only: gero, hese, geno, seto, peta, moka, meds, kvag, domn, karl, nesa, noos, kuub, reco, bora, nols, werd, coot, derp, meka, toec, mosk, lokf, peet, grod, mbed, kodg, zobm, rote, msop, hets, righ, mkos, nbes, nosu, reha, topi, repp, alka, nppp, remk, npsk, opqz, mado, covm, usam, tabe, vawe, maas, nile, geno, omfl, sspq, iqll, ddsg.
I need help, opening .hoop files Please help me too!
Intento descrifrar archivo .moqs pero aparece lo siguiente:
No key for New Variant online ID: 9ctpgeF0SQosVtkyOTqFETYh1XHMTpqOy3hGKjl5
Notice: this ID appears to be an online ID, decryption is impossible
I need help .hoop virus … how can restore my file
My computer is infected with orkf virus. My personal ID: dqrXY3ieriNpuqvwCPhJvLPoeoWpixGC2eqwwYHp. Whether it will be possible to decrypt orkf files encrypted with an online key in the future? And whether it is safe to buy a licence in the Gridinsoft Anti Malvare 4.2.3 program, and whether by purchasing a license I will get the right one that will upgrade this program to the full version?
Please help. I tried to decrypt *.reqg files with EMSISOFT Decryptor but it resulted with the following error.
Thank you in advance.
Error: No key for New Variant online ID: iTkOTf8Ej88mDdRjUW4OqU7hixKMbt5PPVBDL8vq
Notice: this ID appears to be an online ID, decryption is impossible
please decrypt file .orkf
I has been infected with ORFK type online key
is there any possibility to remove it if it was online ?
is yours variant online type or offline type
i heard that online type would be impossible to save
Olá. Bem, meu cliente foi infectado por um ramsonware e acredito que os piores, a extensão é .reqg e parece que a chave é on-line. Baixei o decrypt_STOPDjvu e foi exatamente o que me indicou e disse que era impossuível a descriptografar dos arquivos. Bem, não sei mais o que faço. Formatei a maquina em Linux e depois em Windows, mas reservei todos os arquivos criptografados em uma pasta a parte. Não sei mais o que fazer, estou para desistir.
please help get the ORKF file back to normal
Error: No key for New Variant offline ID: 4aBXQVNZ4BhjpMjt78QLIFtBSJPbgbflYLHrBut1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
It seems I got also new version of STOP/DJVU ransomware because latest version of Emsisoft Decryptor (v1.0.0.5) could not decrypt my files and giving the message below.
Can you please give an update for this new variant ID ?
File: C:\Users\Emre\Desktop\Foto\DSC07295.JPG.orkf
Error: No key for New Variant offline ID: 4aBXQVNZ4BhjpMjt78QLIFtBSJPbgbflYLHrBut1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Thanks & Regards.
Fui infectado com a variante .orkf e o software não conseguiu descriptografar.
Minha ID: 0328gDrgopl13aFVHBqw9GcL001GFs7n9gBzffnKjcAEx2iNG
Ajuda por favor!
Obrigado desde já.
Error: No key for New Variant online ID: hQHyAXXOXOh0lfVOHVIERlJoIpdUjsfXb4wyK8Pt
Notice: this ID appears to be an online ID, decryption is impossible
Please help get the ORKF file back to normal !
I’ve got the same problem with u sir.. my PC got .orkf extention on all of my files..
it said it’s an online encryption so it’s impossible to decrypt.. so sad..
I also had a problem with the orkf virus. I deleted the virus using Gridinsoft Anti-Malware. At this time, it is not possible to decrypt files locked with a network key. It is worth trying Stellar Data Recovery or some other recovery programs for now until they add the key to online locked files by the orkf virus in the future. Do not move or delete any encrypted file as it will be impossible to decrypt.
Please help I have 24 terra file full encrypted files, what am i supposed to do? the message i get is
Error: No key for New Variant online ID: wL6r4kptKGdP3JBft9n89ErCQY01yW0vxp9Q3xyP
Notice: this ID appears to be an online ID, decryption is impossible
this is a new variant (.ORKF) that has started to affect many people as far as I can see. i am suffering from this problem. I hope you resolve this matter as soon as possible. waiting for you to update your decoder
is there any works to fix .lqqw?. is this newest ransom?. need help to decryp.
As I have seen in many people, the .hoop virus has spread. I would appreciate it if you could create a decrypt for this ransomware variant.
I see the virus (.regq) has spread, please help us to decrypt this malware!
It seems there is a new key
Error: No key for New Variant online ID: u1bdRnBITEPAYbEXHsaTZupAXBQTe74Eus4EPDYS
lqqw new ransom?
Help me!
My laptop all file affected by .orkf file extension how will i remove please let me know.
My system infected by gujd virus. I could not find solution about this virus. Please help me.
how to decrypt .qscx file?
this ID appears to be an online ID, decryption is impossible
hi,
.lqqw it is in the list? i start the aplication but nothing….remain an “Starting…”
i have been attacked by ransomware malware named as .LQQW but these decryption tool was unable recover i tried too many times but i have deleted all ransomware txt file note, but i have kept lqqw extension encrypted files.
Error: No key for New Variant online ID: RNui8fKfqlBCXkxYJCHocIluZMtaKrBAQGQ3bM0U
Notice: this ID appears to be an online ID, decryption is impossible
I hope Emsisoft will take action on this “new variant” of .orkf ransomware that infected ALL of my Personal files in the past 15+ years as a Game modder 🙁 🙁 🙁 .
Error: No key for New Variant online ID: PcJr1ZDPgwIc05BX2lalfeD2gPCLWyhL7TLndjZV
Notice: this ID appears to be an online ID, decryption is impossible.
I’ll be waiting nonetheless 😉
-George
I don’t know why, my hdd locked. As far i know, i never give encrypt for any thing about that. Then all my document bring efdc file. Would you help Sir ? give me any solution to mudinuton@gmail.com
help me
how to decrypt .efdc file
tanks
i have been attacked by ransomware malware named as .EFDC but these decryption tool was unable recover.
Error: No key for New Variant online ID: tClGfIjbYBa8gDkRjdqQ7RTHi9BU8YQ3RB38EIOM
Notice: this ID appears to be an online ID, decryption is impossible
Please help all my personal files, office files and google drive files are also infected.
Well, my laptop got infected by .efdc type and at first the decryptor work well and I accidentally abort it. When I start again, it says something like “error the file can’t be….” I forgot the rest.
What should i do?
help me
how to decrypt .efdc file
tanks
Pelo amor de Deus salva meus arquivos efdc, atualiza as versões 🙏🏼😭
por favor me pueden ayudar mi computadora fue infectada por un virus ransomware y todos mis documentos y archivos de cifraron en un formato ORKF, quiero recuperar mis documentos y archivos son de suma inportancia por favor alguien que me pueda ayudar 🙁
my id online how decrypt
WXz4zxGOPXRmHCwHIiuzEDI7KD7VmAAGLbHbzDCD
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-VCW326HODa
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
managerhelper@airmail.cc
Your personal ID:
0330gDrgoWXz4zxGOPXRmHCwHIiuzEDI7KD7VmAAGLbHbzDCD
Hi Dear
pls, few daye ago my pc crypt by EFDC virus
I reset windows but all my files with extend EFDC and I can not open
pls.need ur help
thanks
Hi. Dears
I have had such this problem with .efdc format file.
I used the last version of PhotoRec.
It was not bad. I tried it once. But it wasn’t enough satisfaction. I have to try other soft wares.
Some of my files have been decrypted.
Just Some of the Zip, rar, docx, xlsx, jpg formats were decrypted. None of doc, xls files were decrypted.
Fortunately The MOST of PDF format files were decrypted.
Very of dll, exe files were decrypted.
Butttttt unfortunately you can’t select a folder or a drive for decryption files.(ofcourse you do, but it doesn’t work)
So all of decrypted files gather one place(where you define) and unfortunately unfortunately with a changed name.
If you have a lot of files, it’ll be hard.
If somebody will search and find an easy and suitable way for this problem, let me know, with my email:
abka1001@gmail.com
Please write “decryption of efdc” in the SUBJECT of mail.
Thankyou in advance.
Hello again friends
About Ransomware .efdc format files,
How can I be sure that the virus has been removed from my computer forever, after virus detection?
Because some sites says that after virus detection, virus can remain in computer and MAYBE it’ll cause some problems in the future.
😭😭😭
If somebody can guide me it’ll be a big favor.
abka1001@gmail.com
Sincerely
Abbas
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-8FD9fC02w8
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
managerhelper@airmail.cc
Your personal ID:
0332gDrgozizCTvBgwk25ux5Ex8sSwH37sfMo0Tj8hkvdgd5d
kindly help me to decrypt files thanks
contact me on whatsapp: +923025062715
can you help me with formal .EFDC ?
please let me know when decryption for online key is possible for .efdc
si tienen alguna solucion para el EFDC, favor su ayuda
Hi. my files encrypted with ransomware .xey9ai extension . Is it possible to decrypt
hello sir,, i hope you can help me. my Files got Ransom Attack with “.koom” please give me the decryptor thank you for your all Kindness. 🙂
sorry for my bad English..
We are in the same, my files changed to extension “.koom” and for now there is no solution.
me too, can anyone help
Thakns
We are in the same, my files changed to extension “.koom” and for now there is no solution.
my laptop has injected by ransomware with .WIOT extension.
all my data already infected and i need to decrypt it.
please help if anyone has info
Regards
Same here… wait for a solution…
thanx for anyone wich studi to help us…
my files changed to extension “.hoop” and for now there is no solution.
my Files got Ransom Attack with “.koom” too. please give me the decryptor thank you very much
My Computer has infected by .koom, i use the decryptor version 1.0.0.5 but not work
“Error: No key for New Variant online ID: DI2jKcQ6sJl9MZuMtV4oWBB8gyYJdLgxxa9odpJb
Notice: this ID appears to be an online ID, decryption is impossible”
How i can fix my files.. Oh my God.. Please help me..
please give me a solution regarding extension “.koom 🙂
Buen día, podrian ayudarme a recuperar mis archivos, me ataco .koom, cuando intento desencriptar con el software obtengo el mensaje que tengo una clave ONLINE, 67XPyXqdpmYPGOdtKeOzYTlfMvxL4WDdssnTVvWG, tengo una carpeta SystemID con un texto 0334gSd743d67XPyXqdpmYPGOdtKeOzYTlfMvxL4WDdssnTVvWG,, tengo este otro 99p8vN1UYnRVfJrLk31VTLd69Ni5b0ex99QMQKt1,, Espero puedan ayudarme ya que tengo mis trabajos ahí,
Mil Gracias de Antemano
Amigo meu pc foi infectado pelo ORKF se vc tem a soluçao me informe aqui, pois minhas fotos todas falidas e com esse complemento
também preciso .koom e se possível recuperar gmail hackeado pelo mesmo vírus😩🙏🏻
Please, a solution regarding extension .koom
If anyone can find a solution to decrypt files with extension .koom please let me know.
. PAHD ransomware encrypted files to decrypt tools please 🥺 help update this
s’il vous plait, pouvez vous m’aider à décrypter tous mes documents cryptés par le virus Djvu mon ID est le suivant :Your personal ID:
0318ewgfDdCatwRkqdYh2Jomn6DqwFoGgcSbDsle1xlE1NPtt1
je vous serai reconnaissant pour le reste de ma vie! je suis un enseignant et le hacker a crypte tous les documents dont j’ai besoin pour enseigner !
Olá, existe algum jeito de descriptografar arquivos em .rigd? Alguém poderia me ajudar.
Koom… We need help…. please…..
Hello, I also got rigd ransomware on my computer yesterday. Has your problem been solved? How is it solved? Thank you so much!!!
je suis un chercheur, et tout mes fichier ont été cryptés par un ransomware Djvu (KOOM), et la tool emisoft decrept stop djvu s’affiche que le déchiffrement est impossible , aider moi svp
Any update for Wiot extension offline key? Its been 3 week after the encryption. Please help
my PC was infected with .efdc virus
is there any solution for decrypting them??????
how to decrypt wiot, nooa this two virus
how can i decrypt .okrf file
Hello, I also got rigd ransomware on my computer 3 days ago, please help me by updating this:”) thank you
Sorry dude i’m not the creator of that Decryptor Tool me just sharing it for a possible so that may others will get it.
Hello has provision to decrypt .tsic
ile: E:\SAMPLER\Vietnam bilder\IMG_0892.PNG
Error: No key for New Variant online ID: S0X7lDsmsD5oCky3tcZ82QlYLhUh3mtD6cSDReVm
Notice: this ID appears to be an online ID, decryption is impossible
File: E:\SAMPLER\Vietnam bilder\IMG_0892.PNG.wiot
Error: No key for New Variant online ID: S0X7lDsmsD5oCky3tcZ82QlYLhUh3mtD6cSDReVm
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
I have got .rigd ransomware same upper reply, I will waiting for resolved method.
hi
Error: No key for New Variant online ID: pWwMlLSjhmIFVXJX1HYTJXt0GxgZ6WJzWlW5C17V
Notice: this ID appears to be an online ID, decryption is impossible
pls help
ty
I was blackmailed by the TISC virus!! Request a decryption program!! Please!!
I got infected by .tisc , please any decryptor for this ???
hi, thanks fot the information.
I’ve been searching the web for possible solutions since yesterday and I’ve found out that my .Tisc encrypted files are impossible to be decrypted since they use an online key.
I’ve decided to store my encrypted family pictures so if AES256 will be decryptable in the future I don’t regret deleting them.
I would be happy if anyone can comment and help me in any way.
All my files that i made was encrypted by .tisc yesterday(‘21.10.7).
I tried to fix the files with EMSISOFT but i got the result as below.
File: C:\aa\aa\20191019_culture.jpg.tisc
Error: No key for New Variant offline ID: uFHwN7bjwCkJEeUg8JHISzLqrwudidH8XsPzHDt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Please help me and i am looking forward to your new update. Thanks~.
Your personal ID:
0324gDrgona5VVkffHfkNT34fNALFIXo28YunMlcb5GFNWAvK
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-jTbSQT8ApY
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
managerhelper@airmail.cc
Your personal ID:
0324gDrgona5VVkffHfkNT34fNALFIXo28YunMlcb5GFNWAvK
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-1JwFK5rT39
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
supporthelp@airmail.cc
Your personal ID:
0336gSd743dSJmV6kDF9Vvmir85zMAQmj8hQ17hE0Snb78u198x
i got hit by koom
all my files,photos, documents etc has this as extension ( eg photo1.JPG.koom,Music2.mp3.koom etc )
simply,if i delete the “koom” the file can not be open anymore …
i copied all my files to my data bank, and reinstall OS for my PC..i have clean PC ( in terms of new installation), now i want to RESTORE/RECOVER my files from koom to normal.
how can i do ?
someone please help
Today I was infected by ransomware that leaves files with the .tisc extension.
Is there already a decryption tool?
Thanks!
any solution for .tisc type ?????????
Please help me for decryp my file, i was attack virus ransomeware name is .tisc
please help me
tisc extension you a hole …. im living in iran …. that means no visa or paypal and no mining rig… and half of my files is locked
File: C:\Users\Eriberto\Desktop\Desktop\PLDO_2022_CAJAZEIRAS\Read_Me.txt.nqsq
Error: No key for New Variant offline ID: OGykROpbgxJhrG1qc9yB9PwnsSv1Eo04vOCP0rt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
é possivel descriptografar?
All my files in my PC was encrypted by .irjg yesterday(‘21.10.17).
I tried to fix the files with EMSISOFT decrypt_STOPDjvu but i got the result as below.
File: E:\Downloads\Documents\02._naskah_publikasi.pdf.irjg
Error: No key for New Variant offline ID: xcdIdDNFh62dy3iJsba1COhcfDENsbjPHQQ2Eht1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Please help me and i am looking forward to your new update. Thank you.
I am attacked with new variant of ransomware
irjg
please I need to know how to decrypt my files, they are with the .irjg extension
any application for recovery file has affected by ransomeware .vtua (online id) sir ?
.zzla files was error decrypt , please help
I got infected by .vtua , please any decryption tool for this ??
all file had rename file extension to .zaps
tambem estou tem o problema com esse ransomware alguem tiver uma comunidade pra indicar agradeço
.Maql no new key variant available help me
Arquivo terminado em .MAQL. me ajudem por favor.
Tüm dosyalarım bu rugj uzantısı ile şifrelendi.
Starting…
File: C:\$AV_ASW\$VAULT\vault.db.rugj
Error: No key for New Variant online ID: fGbLKcXXzMzCeUZ2aJPV91KoL84u5EjC7pdnFSLh
Notice: this ID appears to be an online ID, decryption is impossible
readme.txt
0341gSd743dfGbLKcXXzMzCeUZ2aJPV91KoL84u5EjC7pdnFSLh
.vtua Virus Infection – You already have the update for this virus
I’m waiting for more than 2 years for .rooe offline key. can you please work on it?
I got infected by .cool ransomware yesterday. All my images, office files, etc are encrypted now. Please help me to recover them. I followed your guide and did complete removing the virus from my laptop.
Please help me with .reqg file encryption
i was affected by .vtua & .irjg malwave
Please Help decrypte my files
I got infected today by the .cool ramsomware. Please, help me with that.
I got infected by .cool ransomware yesterday.
Também fui infectado por um link que estava na descrição no youtube, arquivos estaão em .cool
Extensão .cool help-me please
. cool was on my comp 70 hours ago. Saved few important file if sometimes it could be encrypted. Help us
Fui infectado pelo ransomware .cool ontem.
Todos os meus arquivos foram alterados, perdi praticamente todas as minhas fotos do meu hd de 1TB
Nos ajude !
Dear Brendan Smith Sir,
Good Morning!
Sorry if you not getting any way to fix this .pahd Ransomware, i think many people sending you A lot off email or msg post for this Decrypting! me also send many time, my point is please Tech to someone how you working for this all RANSOMWARE, because, only you are the one how fix this 1st time and now also all site are giving only your name who is fixing this king of RANSOMWARE, you know this tip off vires making is easy or solution too hard.
thanks sir!!
Do you have any solution with .cool file.. my all data encrypted. Please help. Please help.
Do you have any solution with .cool file.. my all data encrypted. Please help. Please help.
PersonalID: vkkerIMedP7WK1ZhHOAlJV10Wxn9fHEbEQbgait1
Please help me to decrypt .stax stop/djvu ransomeware let me know after it is added to the servers
.stax please
Your personal ID:
0345uSifkePxV8RUU4uZD21xWcmsHCFS9CRwpHAf8zuTcpEyXj
.stax rasonware
ayudeme por favor a desencriptar , por accidente abri el archivo . por favor
Please help me to decrypt .stax stop/djvu ransomeware let me know after it is added to the servers
File: D:\STAX\MODUL JURNALISTIK.pdf.stax
Error: No key for New Variant online ID: KVO9fq0sw75Ws3q0lfPDeP3qbyZfBzL8FUZU6j83
Notice: this ID appears to be an online ID, decryption is impossible
MAQL plsss lütfen çözün şu uzantıyı yardıma ihtiyacım var
please help me!!! .futm online ID. How to solution ????????
0349gSd743duu2i5D61Y7oIP5Pi8BqxLQLKFE7pFDaKoXF7kfHR
Sir plz any solution of .hets virus files recovery plz
please help me!!!
all file had rename file extension to .futm
Error: No key for New Variant online ID: VHEVmB4UUxM8qsGN4Eu6do4tFx2AkSrW5MLERxGA
Notice: this ID appears to be an online ID, decryption is impossible
personal ID:
0349gSd743dVHEVmB4UUxM8qsGN4Eu6do4tFx2AkSrW5MLERxGA
O app do senhor descriptografa arquivo .qdla? (Does your app decrypt .qdla file?)
Esse id tem alguma serventia? (Does this id have any use?)
Your personal ID:
0347gSd743dkiC8Cbcp9SK127Ql2yR1Nev7lc1zHlLhalAY5NLu
please help .gujd file
File: E:\M\Pratiksha\DSC_0260.JPG.orkf
Error: No key for New Variant online ID: lQdJTQPWHui5BLRvgS4U05CzyiYJSC5IJs3xQa52
Notice: this ID appears to be an online ID, decryption is impossible
how to decrypt .iisa file djvu is not working, it said decrypt finish but when i look at it its still .iisa
.tisc please help me!!!
how to decrypt .iisa file djvu is not working
all files are encrypted first in xls format and then in rivd format. decrypt_STOPDjvu The program cannot help. such is the report
Error: No key for New Variant online ID: c2USrGFrJRar5EpxCo12vS55qSgRfEGPePXxj10M
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
Help me plssss….
.rigj
UvTkynkTFYDsBtRJrS53l2qBEvn8tDjFPILDYdLu
.wbxd
DMoUnGuuQMUL0UbazxJjlHejGxeVqmwuBdGeIjBs
I realy need help plssss
Ola este software consegue resolver file.rgij??
How decrypted all my files after attack online virus STOP Djvu Ransomware.
File: C:\Users\dell\OneDrive\Desktop\Choota Bheem.cdr.cool
Error: No key for New Variant offline ID: vkkerIMedP7WK1ZhHOAlJV10Wxn9fHEbEQbgait1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Error: No key for New Variant online ID: qsBa2EbBJ9u6bPx5yUQx5BQ5tl2FlENDOTqEZFCe
Notice: this ID appears to be an online ID, decryption is impossible
my file was in .YQAL pls help, i need all my files back
please help me for New Variant .rigj
Your personal ID:
0353gSd743dlOuNOW7rtWAG8uCPrtw31dy0NtT8JOBX3oZShE8v
Error: No key for New Variant online ID: lOuNOW7rtWAG8uCPrtw31dy0NtT8JOBX3oZShE8v
Notice: this ID appears to be an online ID, decryption is impossible
please help me for New Variant .rigj
Your personal ID:
0353gSd743dzm6MhmzLDStNHB0CsPUcAumZsJf89NmF2xbPugTE
Please someone can help me?!
File: F:\1.pdf.wnlu
Error: No key for New Variant online ID: AJ6LQFmyQpkU72HDd6s1PRcvQl0OMCzToiXSDGbk
Notice: this ID appears to be an online ID, decryption is impossible
Please someone can help me?!
File: F:\1.pdf.wnlu
Error: No key for New Variant online ID: AJ6LQFmyQpkU72HDd6s1PRcvQl0OMCzToiXSDGbk
Notice: this ID appears to be an online ID, decryption is impossible
Your Personal ID: 0357SigrjAJ6LQFmyQpkU72HDd6s1PRcvQl0OMCzToiXSDGbk
File: D:\1.docx.wnlu
Error: No key for New Variant online ID: AJ6LQFmyQpkU72HDd6s1PRcvQl0OMCzToiXSDGbk
Notice: this ID appears to be an online ID, decryption is impossible
Please help me , my files are decrypted
How can I decrypt files with extension .wnlu KEY ONLINE
Olha eu estou com os meus arquivos com a extensão .mljx já existe meios de recuperar?
my system affected by .koom and my online id is 0334gSd743dybCyRrfuoN1mctsSapnQUE1xfvo8PnqFTxuEmagP pls help to decript.
please help with .shgv ransomware thanks
Please, i need help to decript files .MOIA online key
Good day there is any news regarding robm virus
How to remove .XLS extension virus and how to decrypt my data
Im waiting for more than 1 year for the .rooe extension. Will you please give the offline code of this virus?
hello please how to decrypt .zqqw ransomware file. I’ve been waiting for this for 6 months
File: C:\Users\EvandrooMiixOK\Desktop\ELAINE. BIA\VENDA E RECEBIMENTO 20211.xlsx.miia
Error: No key for New Variant online ID: ODUsBYOYeET4ZuPfb0VQfYSpiCwjXHSgdcA7MeUd
Notice: this ID appears to be an online ID, decryption is impossible
Mine is giving this message.
Respected sir,
please let me know how can i remove .XCMB extension virus and how to decrypt my data.
i have tryed to use GRIDINSOFT ANTI MALWARE software and your decryt toll but i m not able to remove .xcmb extention.
please help to to get rid of this problem.
How can I decrypt files with extension .npsk . Files infected 2019
Thanks
good day, someone has the program to pass the ID and the password and be able to unlock the files that the Ransomware blocked.
I have the ID I only need the other two things
I am not able to decrypt “.maak” encrypted files using Emsisoft decryptor,
pls, help me asap.
Thanks in advance.
please help with .eight ransomware thanks
I am not able to decrypt “.yoqs” encrypted files using Emsisoft decryptor,
pls, help me asap.
Thanks in advance.
My Id personel
uDLux1czyPsWNYYagNMKwIiTFQR7Ucyf00Na8st1
SvVEeuFFxcRWOEHAokHH7MVuJSfWQI5a927p11vL
plz help me to decrypt my file
Alright, So i got ransomware attacked.
Type: .maiv
Online key, I Provide you adding .maiv to the list.
And thanks.
Como posso descriptografar arquivos com extensão BBBE
e outro ZAQI
Obrigado
Ayuda con el ransomware SHGV, necesito recuperar mis datos
Hello everyone
I would like some help, I have a ransomware with the MAIV ending, can anyone help me?
I have encrypted the files with .zobm
I have encrypted the files with .MAAK
Hello everyone
I would like some help, I have a ransomware,
with My personal ID:
0393UIhfSdr3bFG6APRYicS0I1tnnghpPC5xulSebRz7ByqcxY
I am not able to decrypt “.Qnty” encrypted files using Emsisoft decryptor
can anyone help me?
help decrypt .cool files
Error: No key for New Variant online ID: f8poyymDISMCVdDFin9VxZpyHzl9WhdZEZShh6QW
Notice: this ID appears to be an online ID, decryption is impossible
please
Meus arquivos foram criptografados por uma licença on-line mais não tenho a Chave os arquivos apareceram com uma extensão ( arquivos.ooii) caso alguém possa me ajudar.
Ajuda para o arquivos (.qbaa)
por favor me ajudo a descriptografar esse virus Qbaa
Please help me decrypt .cuag, online key
Hello,
Thank you for this exceptional guide..
I got the following message..
Error: No key for New Variant offline ID: rpx4UUTYZiAR5omq187UvM233jloVHyJUkA8s3t1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
What should I do, please??
The extension is .iiof format
Por favor solución para descifrar archivos .orkf
please help me descrypt .devil files
Please help me decrypt .cuag, online key
Please help me decrypt .Vyia, online key
Please help me decrypt bpqd. files, the log is:
“Error: No key for New Variant online ID: wQ5VIEODEOUWIVLwP7DV4tUWftjOwycQ4d3CRLcH Notice: this ID appears to be an online ID, decryption is impossible.”
Buenas tardes le agradezco me ayuden a descifrar archivos con extensión .FGUI, ya intente con el programa Emsisoft Decryptor para STOP Djvu, pero me sale que no es posible el descifrado “Notice: this ID appears to be an online ID, decryption is impossible” muchas gracias
Please help me descrypt .devil online key
Very good work, we were attacked by a ramsoware.
If you can help us, thank you.
My Computer had infected with the Ransomware virus, My docs was encrypted by the virus they had got .iiof extension. I am using the emsisoft decrypt file but after decrypt they show that: Error: No key for New Variant online ID: hQ3tQaxv2OuzTcbiUyrraXVaYRcFOHQd9dAa9WWO
Notice: this ID appears to be an online ID, decryption is impossible.
what does it mean? what could I do after that.
Please help me decrypt .Vyia
Hi!
Can you decrypt this?
Starting…
File: D:tempcarprog10.93�81105CAR001773I.lib.rigd
Error: No key for New Variant online ID: cnFxZOAV1mrPeoWvWeDACGT8qZFaUDokPZ1nwcPG
Notice: this ID appears to be an online ID, decryption is impossible
File: D:tempcarprog10.93carprog 10.05.exe.rigd
Error: No key for New Variant online ID: cnFxZOAV1mrPeoWvWeDACGT8qZFaUDokPZ1nwcPG
Notice: this ID appears to be an online ID, decryption is impossible
File: D:tempcarprog10.93carprog 10.93.exe.rigd
Error: No key for New Variant online ID: cnFxZOAV1mrPeoWvWeDACGT8qZFaUDokPZ1nwcPG
Notice: this ID appears to be an online ID, decryption is impossible
File: D:tempcarprog10.93READ ME!!!.txt.rigd
Error: No key for New Variant online ID: cnFxZOAV1mrPeoWvWeDACGT8qZFaUDokPZ1nwcPG
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
HELLO, PLEASE I NEED UIGD RANSOMWARE DECRYPTOR. THANKS.
Plis .ssoi
friend help me please I don’t know how to solve this anymore all my files ended up with .MPAG extension
Boa noite, tudo 100% sou o Carlos e contrai esse ransoware ao baixar arquivos pra ativar o windows 8.1Pro, e exatamente este que esta aqui no site e tem estes textos pedindo resgate pra liberar meus arquivos que ficaram com a extensao .udla sera que este programa desbloqueia essa extensao, desde ja agradeço pelo seu otimo trabalho e desejo Sucesso pra toda sua Vida, grande abraço.
Por favor me ajude a descriptografar .Vyia, chave online
I was infected with a ransoware that needs an online key, “.mpag” I have already stopped the virus, now I need to decrypt the files, please help me.
Starting…
File: C:\Users\GRAPHIX DESK\Desktop\pdf\Zambian Paralegal Working to Bridge DRAFT 30th Nov 2021.pdf.xcbg
Error: No key for New Variant online ID: VKva6uKQoR2ptIGMlegM494vuHz4qPFhB9laokDz
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
Boa tarde fui Infectado Pelo GTYS perdi varias fotos e nao consigo Descriptografar pelo StopDjavu
alguem sabe me diser se tem como recuperar sem precisar pagar !
ja fis de tudo todas as pesquisas programas e nada AJUDEM !!!!!!!!!!!
Please Heeeelp me for solve uyjh please
Error: No key for New Variant online ID: AHuGOEx7cyJript53SZUg6lzMvqBppTHapxUt2lS
Notice: this ID appears to be an online ID, decryption is impossible
HElp Help HelpPleaseeee
i have been attacked by ransomware malware named as .grod but these decryption tool was unable recover i tried too many times but i have deleted all ransomware txt file note, but I can not dycript my files
File: C:\Users\Win 7\Desktop\ŞİFRELİ DOSYALAR\bmw.jpg.gtys
Error: No key for New Variant offline ID: qwVQoIsE2xLety0oNWloOilSDuIBXJGK86LM3ot1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Please help me decrypt my file,
My ID: 0413JsfkjnsKFFeKe3xHaw4laoikmznrCs5Z1bOuQTSZtjkXca
Error: No key for New Variant online ID: 4uZnA2fk2KkJnnTAsuhjarGr70PcScZ3jYfEh37Z
Notice: this ID appears to be an online ID, decryption is impossible
dwqs RANSOMWARE
Do you have an update scheduled?
File: C:\Users\IT SOLUTIONS\Desktop\20210927233656.mp3.maiv
Error: No key for New Variant online ID: djyXhqdPadZQvU3j9x3kynZBBjP5myWRRscCJHFy
Notice: this ID appears to be an online ID, decryption is impossible
fui infectado pelo vírus SSOi preciso de ajudaa
Archivos cifrados con extension .GHAS
el software devuelve esta respuesta.
Error: No key for New Variant online ID: fQTZeunxSx4rCq7HNYSrEmE42FqI1YIe8s6jfNis
Notice: this ID appears to be an online ID, decryption is impossible
any solution to .voom extension ransomware??
Please .ssoi
kenapa kok bikin susah orang-orang
.WEUI alguma solução para decriptografar!?
Hello! okay.
can you help me.
I tried with the offline program but it didn’t work, it resulted in the below error.
Please, help me!
20160229_164725.mp4.hhjk
Error: No key for New Variant offline ID: w6IKbZ9nGWp1wM5W7MK8obmynSc0Hx2FVdvsSzt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
My laptop very recently infected by .gtys all important files how do i get files back dycryptor
No key for New Variant offline ID: qwVQoIsE2xLety0oNWloOilSDuIBXJGK86LM3ot1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Error: No key for New Variant online ID: mVpW9bsFIc9gbYkl58YuYJjfmnnJ4gdxYV9jwao5
Notice: this ID appears to be an online ID, decryption is impossible
perdi arquivos importantes
Please help me to decrypt fgnh. I lost everything on computer.
ID.0439JIjdmfToCHeQer5DFbt4KJDsbAC1fYYt0qICPhV48MDgK …………Please help me to decrypt GTYS- VOOM
Error: No key for New Variant online ID: QlFL1frt4I6f3B7GNmTR6gDAdYJCMzpJVoE1HCTi
Thanks for the try and all this info.
As far as I can see, there is NOT a single person here who has managed to recover ANY infected files.
Error: No key for New Variant online ID: 1VBCrowgNhzz0cXsYDU6PDQUiRMz0MnfTkALyD6P
please help me for New Variant
File: E:\bookmarks.html.vpsh
Error: No key for New Variant online ID: CxKtHt5VYmeKEInhEHnlTEpWxisThFO4X3AyBWOP
Notice: this ID appears to be an online ID, decryption is impossible
ajude-nos a descriptografar a extensão fghn
Hi love, I have all my files on my external HD with the *.ewdf virus, all encrypted, my songs that I composed, everything blocked and they still sent the ransom letter ID 0490JIjdm0Lmzh4JViIntkK43n61LdehYz2PRhTKa8WzQmStZ.
I hope you can get a decryptor to solve my problem, God bless you, kisses.
hoop? hoop?
Have solver?
how to decrypt .kasp ramsome ware, plzz……
please help me for New Variant
File: E:bookmarks.html.nnuz
Error: No key for New Variant online ID: hGQ4ZYacnqRbrWtjQzMMRvURPkG5FAgLCEOHAJso
Notice: this ID appears to be an online ID, decryption is impossible
File: C:UsersenderDocumentsWondershareWondershare FilmoraUser MediaMediaDataMediaData.DB.eegf
Error: No key for New Variant online ID: ZOR6B1XdYA2f0VBuECl1LhA0VJh99q0W3kgiiCIv
Notice: this ID appears to be an online ID, decryption is impossible
can anybody help tp decrypt files encrypted by BBYY… it happened about 3 days back… also received note as mentioned by many
Estimado Brendan Smith
su ayuda por favor a descifrar archivos con SSOI me sale un error con la herramienta STOP DJVU Notice this ID appears to be online ID decryption is imposible su ayuda por favor
meus arquivos estao em EIUR o que faço?
Dear Sir . i have done all the said steps. But the result is……
Notice: this ID appears be an offline ID, decryption MAY be possible in future……
Kindly help me to solve the problem…..
Thanks…
lloo bu uzantının cozumu varsa lutfen yardım arkadaslar
LLOO için şifre çözme aracı için lütfen yardım edin
Help me recovery .peet file plz sir.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-WJa63R98Ku
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
Quando uscirà la chiave per decriptare nnuz?
sono vittima di DJVU e i miei file hanno estensione .lloo
il decriptor mi da questi messaggi sui file analizzati:”Error: No key for New Variant online ID: GJkn0TkfAFGevzWQxWBdP8rgsQ4OUjiHY2PJNlBh
Notice: this ID appears to be an online ID, decryption is impossible”
help
aslamulikam
Good day
sir my na Mohammed Iqbal sir i want some help i don’t no more English
i am working in uae united arabe emirates i am scorching your website i am spacing handi
sir my computer attack ransomware virus my all file lock every file last bbii coming can you help me sir
so many try but no go virus bbii my file my data is back sir any saloction
can you sand me watsap number pls sir halp me
sir i am sand file screen shot i am scan my computer eset nod32 antirust
ID: lnBBXCayfEWiNOix5kNgGVd7IYdvbbUtbRjkm7jA
thanks
extension .vvwq
I used Decryptor Stop DJVU app, and it can’t decrypt.
I get the following message. What I can do?
Starting…
File: D:\TIENDA\a recuperar\LISTA DE PRECIOS ACCESORIOS.xlsx
Error: No key for New Variant online ID: 4a74Z2B6h2zBHBWG9TTBkZlHkHVYeyOJEvE5wB8s
Notice: this ID appears to be an online ID, decryption is impossible
Finished!
Hello Brendan Smith, I would like to know if there is already a tool to decrypt .VVWQ?
Thanks
Hola por favor ayuda con .orkf
ayuda por favor todos mis archivos tienen extension hhwq como los puedo desencriptar
Error: No key for New Variant online ID: PrKH3wTHTEsiy6xsQKPAQD5RRy7ebHT8GxE4ml1N
Notice: this ID appears to be an online ID, decryption is impossible
Could you help me on the above problem ?
Error: No key for New Variant online ID: DlCRFDzj5q3Ej6VDcMazYP45HZbfPdsxgFtH7baV
Notice: this ID appears to be an online ID, decryption is impossible
Could you help me on the above problem ?
Hello Brendan Smith, I would like to know if there is already a tool to decrypt .VVEW?
Thanks
Emsisoft Ransomware Decryption Tool
File: C:\Users\ADMIN\Desktop\IMAGES\Ganapathi.jpg.qqlo
Error: No key for New Variant online ID: LF4AjS0x9QAa5gbph8EESQ1rVTMiSG3ptVaWLUuV
Notice: this ID appears to be an online ID, decryption is impossible
My Computer is affected By .GGWQ Ransonware. Please Help Me To Restore My File.
I would like to know if there is already a tool to decrypt .VVEW
I saw that for now the tool still does not work, but I would like to know if there is already a job to create for the .vvew remover. Thanks.
Hi Brendan Smith.
My files are all infected with the qqjj extension.
I lost everything, videos, photos, txt, and important documents from college papers.
I looked at your list and it still doesn’t have the extension I mentioned, so there’s no point in me downloading your program or formatting my computer.
Maybe you can help me, sorry for the bad english I’m from Brazil and my native language is Portuguese, I used a program called – Advanced System Repair Pro.
It found some trojans and as soon as I clicked fix everything it infected my whole computer with this damn QQJJ extension.
I will wait for a response from you to my email, thank you for your attention.
My pc is infected by ransomware STOP djvu with .qqlo extension. Mine is an offline id. Emsisoft decryptor is not possible to decrypt .qqlo files yet. Can you tell me when it will be possible or are there any other ways to decrypt files sir?
did you solve it? I also got infected by qqjj
did you solve it? I also got infected by qqjj
I know they do it for money, but they don’t take into account poor people with no money, in need, working for a few cents, and losing hours of work or photos of they beloved family or dead friends, you have no respect for anyone and do this just for money so I am going to contact anonymus crew to help find a solution for people with no money and to get thsat servers down and get the people doing this to public so they can be prosecuted and justice will be made.
MoaCD11OaG2dgfHYZtJxyWvQIhM3iufk4fcMkFkl
this the key they used and .EEMV is the extension of infected files.
thanks for your time and help.
From Colombia.
300F9AFA66C3247795A2190311D196D0CE7D2C4B
this key was also into a file named 0AEA090CD206
is there a solution for .mmdt
this is a offline key. when can i repeat my files
I have .mmdt extension problem please help me.
when I use the emsisoft, an error appears and that error is below
Error: No key for New Variant offline ID: yd6oYv6aBN90yFzTWdZ34sXSXtXiauzOLXZyWht1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Please help me and answer this post.
I have .mkos extension problem please help me.
when I use the Emsisoft, an error appears and that error is below
Error: No key for New Variant online ID: w3oZSxroVER63MmaiNL1Fb844arcCgWpeo4Xoog8
Notice: this ID appears to be an online ID, decryption is impossible
Please help me and answer this post.
Dear Sir,Could you please help me decrypt .EEWT File?
help me .bbii recover please
I keep seeing the message below when i try to decrypt my documents, what do i need to do in this case?
File: C:\Users\User\Documents\EPPA MEETINGS\Draft EPPA MEETING MINUTES 18.12.2020.doc.ofww
Error: No key for New Variant offline ID: xkNzhkB1wvgoDI7Uo0HPNLY3qCuwoFpP7nlhlut1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Finished!
Ola, meu computador foi afetado pela criptografia ( ofoq) e a (oflg) tem como salvar?
ID: 5mQh9NgrMmrZplvE9QTj7pcbVMjDkdPwUX4eNIhc
Notice: this ID appears to be an online ID, decryption is impossible
extenção do arquivo .ofoq
Hello please.
How to decrypt .pphg ransomware file.
File: C:\$Recycle.Bin\S-1-5-21-2056994554-1883553153-4115512118-1001\$RB4WMNG.pphg
Error: No key for New Variant offline ID: dYUDKE4rrBmSPsf8srHMsyP40jle9uyxDDCfdxt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Failed to decrypt file with .adww extension.
Help please
Error: No key for New Variant offline ID: atQpRfpTf6bEEYHQxofqkrbRZ6xrCH6OD1M6h6t1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
please help!
Kindly help me on this matter.
File: D:\Downloads\Compressed\a1 – t9mbc2\a1 – t9mbc2\t9mbc2.zip.aayu
Error: No key for New Variant offline ID: MyudhIExJux2oRQXw95TT1oAPu7mvqRMzxr1eet1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Thank you.
Estoy esperando que alguien pueda decifrar la extension .adww desde el 4 de octubre 2022 que me bloquearon archivos. Nada ha funcionado de momento, tengo la llave pública, no la privada.
my laptop files encrypted by .pozq and i can’t decrypt it using your tool. Please help me. Thank you
this ID appears to be an online ID, decryption is impossible, this with EMISOFT, is there a way to decrypt my files?
File: G:\pfe final name\chp4\PFE-Chapitre IV.doc.powd
Error: No key for New Variant online ID: xY43J2UFhZQpI3TA7OWoL75fhqSdj2YbwqrKVqce
Notice: this ID appears to be an online ID, decryption is impossible
MI PC SE INFECTO E INCREMENTARON EXTENSION DE ARCHIVOS .ZATP, LOGRE ELIMINAR EL VIRUS, EL PROBLEMA ES QUE LOS ARCHIVOS QUEDARON CON LA EXTENSION .ZATP Y NO LOS PUEDO ABRIR, FAVOR AYUDA PARA RECUPERAR MIS ARCHIVOS….
my COMPUTER files encrypted by .zapt and i can’t decrypt it using your tool. Please help me. Thank you
Please help me to decrypt .erif file
Por favor necesito ayuda todos mis archivos fueron modificados con al extensión .zatp, ayuda…..
please help how to remove .igal extension
please i need help online ID key BOWD
por favor .znsm
Pls help me, my id is online key
will it be updated to decrypt isza files?
I need a solution for “tisc” could you help me?
AVArmor incoming response :
misleading claims or unethical 4 issues to resolve site
EMSISOFT incoming response :
File: C:\Office14\SAMPLES\SOLVSAMP.XLS.sspq
Error: No key for New Variant online ID: I99lxdhoim39NutsZ4sLtwoONWYJpEDsLizC4sWk
Notice: this ID appears to be an online ID, decryption is impossible
GRİDİNSOFT Anti-Malware v.4261 incoming response :
5 items -34 PUP-144 Harmful items found
What would you recommend for my sspq.
Error: No key for New Variant online ID: jQcfDnSstV5eyr72V4jckujEYH75KxOsfkUNpqlC
Your personal ID:
0632JOsiejQcfDnSstV5eyr72V4jckujEYH75KxOsfkUNpqlC
IObit_Malware.rar.poqw
this decrption is avaible on emsissoft?
I am a graphic design student and these miserable people have encrypted my schoolwork. Is there a solution for the .tcvp variant?
Hi There,
my laptop was infected with MZTU
Error: No key for New Variant online ID: N6oUVG3mJefRww5QrOIoC3CJQTlrlYqPe02rPnlF
Notice: this ID appears to be an online ID, decryption is impossible
this decryption is avaible on emsissoft?
file2.ico.mztu
Regards
OJoker
Please someone can help me, that my computer got infected by .mppq with variant id online, please.
Help me, I get the error: Invalid characters in path. I have a backup, but I want to get my disk back, so deleting the files is not a problem, but I can’t do it because the disk is protected.
Please help me to recover .MKP encrypted files
Do you get any solution for .repp or .erop ?
I have downloaded the tool & followed the instructions. This message appears
@This ID appears be an offline ID. Decryption may be possible in the future.@
Will you update the tool & will you let us to know the status of updating…
Many Thanks
Error: No key for New Variant online ID: Wvsf5hXlIHriwbu5dUltmi7RdX94NMjuEhf09CC3
Notice: this ID appears to be an online ID, decryption is impossible =(
Hola, ayuda por favor, pc con archivos encriptados variante hhoo
Error: No key for New Variant online ID: E2uaceFQ16o3DyXcC3SeKpUHXrraygOGJ8g44emv
Notice: this ID appears to be an online ID, decryption is impossible
Hello, your help, I need how to decrypt with the .REMO variant with the ID: 0214OIQuhkjdDyUl24AXu78WtxNVxgERckl829FIhO6bn00lDUNy
Please
Thank you
Hello, your help, I need how to decrypt with the .REMK variant with the ID: 0214OIQuhkjdDyUl24AXu78WtxNVxgERckl829FIhO6bn00lDUNy
Please
Thank you
Hola su ayuda necesito como descifrar archivos con la variante. IOTR
ID: 0651JOsierwfnSuSDJ9dLbwdyfjvQPvmdlHT5MNME2eqbQjSu
como recupero archivos iotr
Please Mr.
Please someone can help me. I have “.wrui” extension problem and too ssoi.
My whole files are attacked by .kasp malware and need to decrypt. I have removed the virus by formatting C: Drive and reinstalled the windows 7.
Online key
ID: DsNMLxvTJCA8kPumRFAipNBL9MBstlhEyPY59pB1
What should I do?
Try to use PhotoRec (it is a free tool) to recover encrypted files. If it did not help – just have to wait for the moment when decryption becomes possible. Follow the news on our site or telegram.
Hope someone help me about jyos decryption Tool or software
tywd.exe.boty
çözümü nedir?
descrypt ransomeware BOZQ please 🙁
Please help me to decrypt .foty file
Emsisoft Decryptor says:
Error: No key for New Variant offline ID: JFtdCcJoPS9sBORc6lnQV44QG764HrKKynxqdVt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Existe solución para descifrar la online ID: ptAc6WywOSSpCkQAgPNuMdwYFrCMU5sEznGFkuHT
y luego descifrar los archivos afectados por esta variante ransomware .boza
Encontré la solución para descifrar la clave en online ID: ptAc6WywOSSpCkQAgPNuMdwYFrCMU5sEznGFkuHT
y luego descifrar los archivos afectados por esta variante ransomware .boza
It Didn´t work with the Vapo virus How to fix it?
Buen día, estoy lidiando con un disco externo, el cual se infecto y tiene todos sus datos con la extencion .MBTF, Alguien sabe como recuperar los archivos encriptados???. gracias.
hello, new ransomware virus .aabn I couldn’t find a solver for this virus, please help me with this. Waiting for your e-mail response.
sono stato colpito da virus neqp c’e possibilità di recuperare i miei dati grazie
por favor alguien me puede ayudar a recuperar o desencriptar un hdd de 500GB que me encripto un ataque por un RAMSONWARE y todos los archivos del disco tienen extensión .MZOP y no puedo acceder a abrirlos…por favor alguien me puede ayudar necesito recuperar información muy valiosa de ese disco. Saludos
Hola amigo, yo estoy desde el 2019 esperando solución, lamentablemente fui infectado por la “online key”, esto quiere decir que una vez que fui infectado, me volví a conectar a internet y se colgó del servidor pirata, lo cual le cambio la “offline key” por una clave única indescriptable que llaman “online key”, lo que en resumen, no existe software que pueda arreglarlo. La única opción de recuperar todo, es que no te hayan asignado una “online key”, lo cual puedes saberlo a través del software de decriptacion. Si este software te arroja error, entonces te asignaron una “online key”, y ante eso no hay nadie que pueda ayudarte. Es lamentable, pero asi es esto. Yo perdí mucha info, y la verdad que lo único que he hecho desde el 2019, es respaldar la info encriptada hasta que alguna vez haya solución, que lo dudo.
Local\Google\Chrome\User Data\Default\Cache\Cache_Data\f_000a5c
Error: Error en el servidor remoto: (404) No se encontró.
how I can remove virous change extinctions file to mitu.
Please if you have tools to Decryption for remove mitu send it to me.
How do I decrypt Kitu file
Dear Sir please notify me when you find out the decryptor for .neqp files? why there is no update from 2021?
thanks
Hey guys!
Is there a key to decrypt ransomwre .oori?
Thank you very much for your attention!
Carlo
Hi,
my ransomware is called .wzqw.
I’m trying to download the Emsisoft decryptor but the link doesn’t work (https://www.emsisoft.com/ransomware-decryption-tools/download/stop-djvu), any idea of where we can find it?
thank you, this website is very helpful
Hi,
Try this link: https://www.emsisoft.com/en/ransomware-decryption/download/stop-djvu/
Hi.
my ransomware is called .coos.
Emsisoft Decryptor says:
Error: No key for New Variant online ID: DBhaUh1JHUiNWx3goDigfL3aCUlx04nexXOzXF12
Notice: this ID appears to be an online ID, decryption is impossible
Please help me to decrypt
Tem atualização para ransomware .iswr ?
Hello.
There are files encrypted by a virus with the extension .azhi. Attempts to decrypt files using quick methods ended in failure.
I also retained a number of original files, without changes.
Perhaps you know a way to create a Decryptor based on a normal and encrypted file?
Thank you.
Mis archivos están con infectados con extensión .mzop
My whole files are attacked by .Bhgr malware and need to decrypt
.rtpz? decryption MAY be possible in the future? can u help me?
.itqw? decryption MAY be possible in the future? can u help me?
Please, my machine network ended up being contaminated by ‘.ITQW’, could you help me?
not work for .ppvs !
please help me if anyone know what should I do.
Error: No key for New Variant online ID: Oalv4swWTTJY9NXsKsnnAQNE70MXXEX5WuolYwua Notice: this ID appears to be an online ID, decryption is impossible
Ransom where is really powerful and can put you back from your current age to a few years back in terms of update and data, I have unfortunately experienced that 🙁
how can i decrypt.iicc
Error: No key for New Variant online ID
my system is affected yesterday
My problem is: “id appears to be an online id, decryption is impossible”
How can i fix this problem ?
Error: No key for New Variant offline ID: nN1rRlTxKTPo66pmJEAHwufZ2Dhz4MsNxIlOk6t1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
Well, at least it’s not an online variant. Still, what now? Can’t I send sample files to decrypt?
Apparently, yes we can send files to be decrypt!
https://decrypter.emsisoft.com/submit/stopdjvu/
You need to give them both the encrypted file and the original. How do you get the original you may ask? I’m thinking of using a file recovery software. You can just look up any on the internet. Good luck to everyone going through this!
You know how to fix my decryption problem ?
Should i wait so long again to have a answer ?
Me ajuda por favor!!
Error: No key for New Variant online ID: IBYivweDyZDgZzLHvtCmMkCJW4NTLYuvd85SLtAT
Notice: this ID appears to be an online ID, decryption is impossible
my photos and video attached .yzaq virus pls help me
Pls help to recover my file that has extension .hhaz due to ransomware.
Thank you very much
hangi uzantılı dosya türünü çözemediniz dosyanızın aasıl uzantısı nedir
Error: No key for New Variant online ID: 9TlMcFNc8vZBzJpJQqTHy06kfcdoqzIjwPVxYc0N
Notice: this ID appears to be an online ID, decryption is impossible
I have been attacked with .neqp please if you have any solution help me please.
please help me
due to virus attack, the affected files have beenconverted in ti ‘kizu’ and ‘kitu’.
please suggest me a best decryptor that can decrypt all
god bless you.
Hello Abhishek Medatiya. did you found any solution?
hello can i get back my file attcak by the uyro … because i already format my computer buy the external hdd file is all encrypted
Hello. I recovered jpg files encrypted with the hhaz extension in December, but I cannot recover files with other extensions. My decoder can only decrypt jpg files. When will the decyrp of this extension be released?
Help me…please…
Error: No key for New Variant online ID: Az4DDZFnBgxkk9oWbpLri27MnV4XWZUuA2g3t5R3
Notice: this ID appears to be an online ID, decryption is impossible
dear sir my system got .lkfr kindly give me decryption software
I got infected by the .cool ramsomware. Please, help me with that.
Help me…please…
sir my system got .mkp file kindly give me decryption software
Despite all the effort they make, it does not work to decrypt my files with Vyia extension. it is a pity. Thank you anyway. I hope one day these types of scams will end.
is it possible to decrypt .qlln malware .
I am waiting for an update on .rooe extension. I have lost so many memorable images and videos.