Nobu is a DJVU family of ransomware-type infections1. This infection encrypts your private files (video, photos, documents). The encrypted files can be tracked by specific “.nobu” extension. So, you can’t obtain access to them at all.
In this article I will try to help you remove Nobu virus without any payment. Also, I will assist you in decoding your encrypted files.
What is “Nobu”?
☝️ Nobu can be correctly identify as a ransomware infection.
Ransomware is a specific kind of virus that encrypted your documents and then forces you to pay for them. Djvu/STOP ransomware family was first revealed and analyzed by virus analyst Michael Gillespie2.Nobu is similar to other representatives of ransomware like: Weui, Lisp, Sglh. Nobu encrypted all popular file types. Hence, you cannot use the own documents . Nobu adds its particular “.nobu” extension into all files. For instance, the file “video.avi”, will be changed into “video.avi.nobu”. As soon as the encryption is successfully accomplished, Nobu creates a special file “_readme.txt” and adds it into all folders that contain the modified files.
Here is a short details for the Nobu ransomware:
| Ransomware family3 | DJVU/STOP4 ransomware |
| Extension | .nobu |
| Ransomware note | _readme.txt |
| Ransom | From $490 to $980 (in Bitcoins) |
| Contact | [email protected], [email protected] |
| Detection | Win32/GenCBL.NT, Trojan.Agent.EZUU, Trojan.Cutwail |
| Symptoms | Most of your files (photos, videos, documents) have a .nobu extension and you can’t open it |
| Fix Tool | See If Your System Has Been Affected by .nobu file virus |
This text asking payment is for get files back via decryption key:
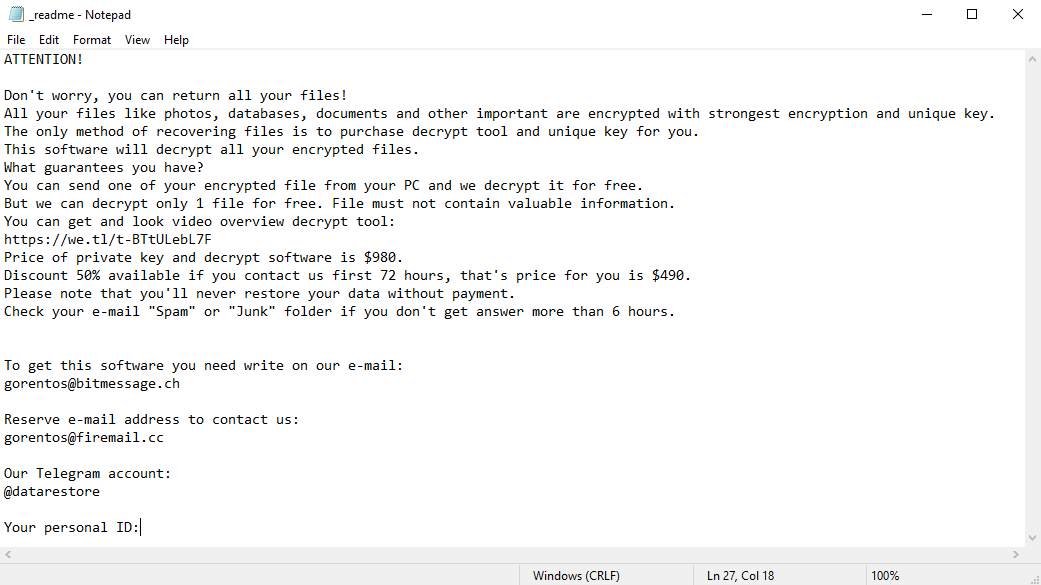
The scary alert demanding from users to pay the ransom to decrypt the encoded data contains these frustrating warnings
The cryptography algorithm used by Nobu is AES-256. So, if your documents got encrypted with a specific decryption key, which is totally unique and there are no other copies. The sad reality is that it is impossible to recover the information without the unique key available.
In case if Nobu worked in online mode, it is impossible for you to gain access to the AES-256 key. It is stored on a distant server owned by the criminals who distibute the Nobu infection.
For receiving decryption key the payment should be $980. To obtain the payment details, the victims are encouraged by the message to contact the frauds by email ([email protected]), or via Telegram.
Do not pay for Nobu!
Please, try to use the available backups, or Decrypter tool
_readme.txt file also indicates that the computer owners must get in touch with the Nobu representatives during 72 hours starting from the moment of files where encrypted. On the condition of getting in touch within 72 hours, users will be granted a 50% rebate. Thus the ransom amount will be minimized down to $490). However, stay away from paying the ransom!
I certainly advise that you do not contact these frauds and do not pay. The one of the most real working solution to recover the lost data – just using the available backups, or use Decrypter tool.
The peculiarity of all such viruses apply a similar set of actions for generating the unique decryption key to recover the ciphered data.
Thus, unless the ransomware is still under the stage of development or possesses with some hard-to-track flaws, manually recovering the ciphered data is a thing you can’t perform. The only solution to prevent the loss of your valuable data is to regularly make backups of your crucial files.
Note that even if you do maintain such backups regularly, they ought to be put into a specific location without loitering, not being connected to your main workstation.
For instance, the backup may be kept on the USB flash drive or some alternative external hard drive storage. Optionally, you may refer to the help of online (cloud) information storage.
Needless to mention, when you maintain your backup data on your common device, it may be similarly ciphered as well as other data.
For this reason, locating the backup on your main computer is surely not a good idea.
How I was infected?
Nobu has a various methods to built into your system. But it doesn’t really matter what method was used in your case.
Nobu ransomware attack following a successful phishing attempt.
- hidden installation along with other apps, especially the utilities that work as freeware or shareware;
- dubious link in spam emails leading to the Nobu installer
- online free hosting resources;
- using illegal peer-to-peer (P2P) resources for downloading pirated software.
There were cases when the Nobu virus was disguised as some legitimate tool, for example, in the messages demanding to initiate some unwanted software or browser updates. This is typically the way how some online frauds aim to force you into installing the Nobu ransomware manually, by actually making you directly participate in this process.
Surely, the bogus update alert will not indicate that you are going to actually inject the Nobu ransomware. This installation will be concealed under some alert mentioning that allegedly you should update Adobe Flash Player or some other dubious program whatsoever.
Of course, the cracked apps represent the damage too. Using P2P is both illegal and may result in the injection of serious malware, including the Nobu ransomware.
To sum up, what can you do to avoid the injection of the Nobu ransomware into your device? Even though there is no 100% guarantee to prevent your PC from getting damaged, there are certain tips I want to give you to prevent the Nobu penetration. You must be cautious while installing free software today.
Make sure you always read what the installers offer in addition to the main free program. Stay away from opening dubious email attachments. Do not open files from the unknown addressees. Of course, your current security program must always be updated.
The malware does not speak openly about itself. It will not be mentioned in the list of your available programs. However, it will be masked under some malicious process running regularly in the background, starting from the moment when you launch your computer.
The message by the Nobu ransomware states the following frustrating information:
ATTENTION! Don't worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-WJa63R98Ku Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: [email protected] Reserve e-mail address to contact us: [email protected] Your personal ID: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
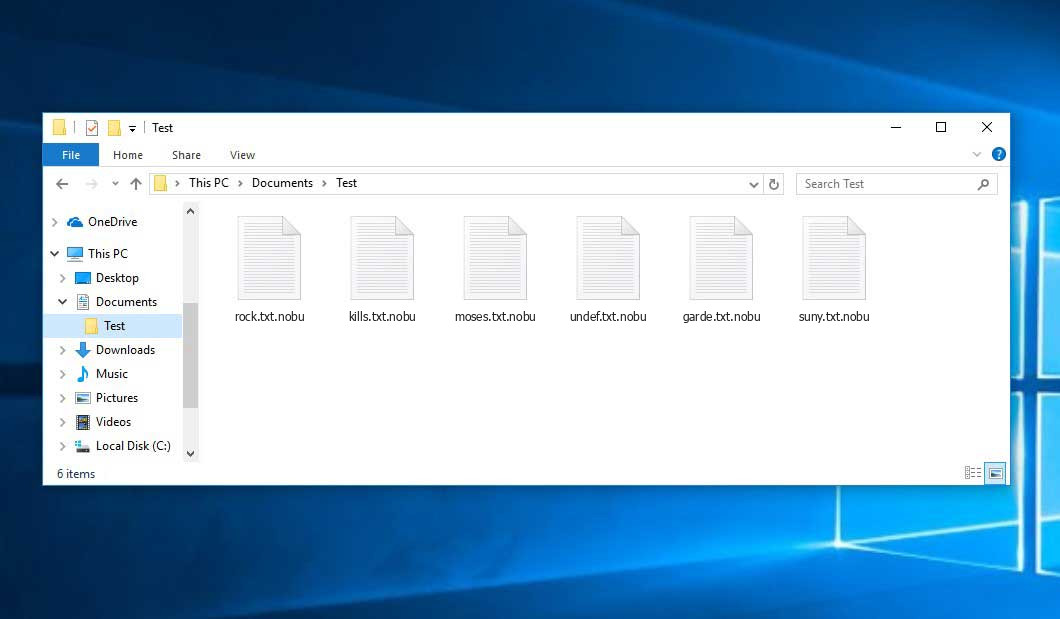
The image below gives a clear vision of how the files with “.nobu” extension look like:
How to remove Nobu virus?
In addition to encode a victim’s files, the Nobu virus has also started to install the Azorult Spyware on PC to steal account credentials, cryptocurrency wallets, desktop files, and more.5
Reasons why I would recommend GridinSoft6
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes7.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your computer.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Nobu infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
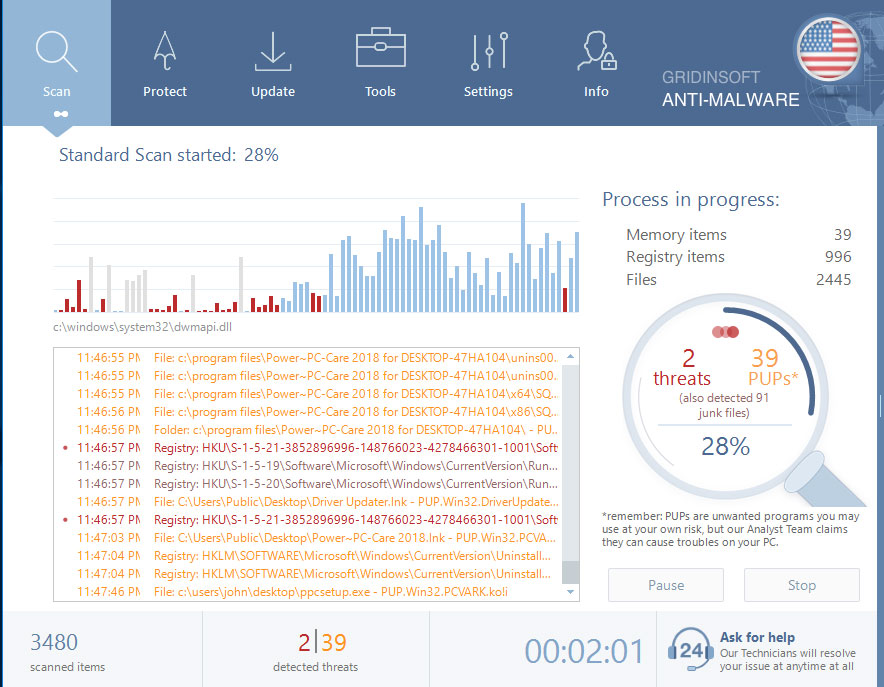
Click on “Clean Now”.
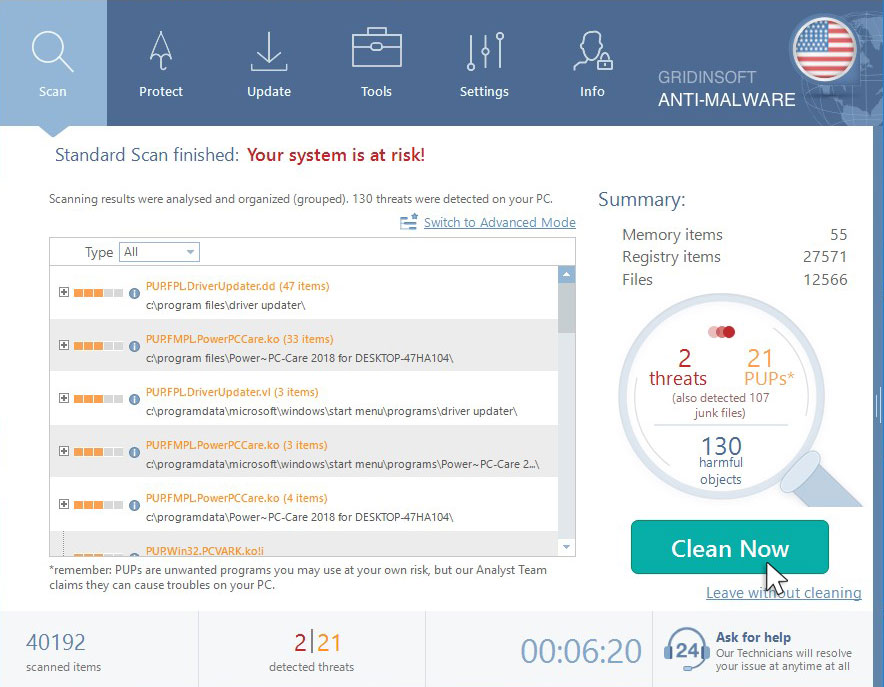
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
Trojan Killer for special instances
In some certain instances, Nobu ransomware can block the running of setup files of different anti-malware programs. In this situation, you need to utilize the removable drive with a pre-installed antivirus tool.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft – Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version 8. This term will definitely be 100% enough to wipe the Nobu ransomware out.
How to decrypt .nobu files?
Restore solution for big “.nobu files“
Try removing .nobu extension on a few BIG files and opening them. Either the Nobu ransomware read and did not encrypt the file, or it bugged and did not add the filemarker. If your files are very large (2GB+), the latter is most likely. Please, let me know in comments if that will work for you.
The newest extensions released around the end of August 2019 after the criminals made changes. This includes Slgh, Epor, Vvoa, etc.
As a result of the changes made by the criminals, STOPDecrypter is no longer supported. It has been removed and replaced with the Emsisoft Decryptor for STOP Djvu Ransomware developed by Emsisoft and Michael Gillespie.
You can download free decryption tool here: Decryptor for STOP Djvu.
Download and run decryption tool.
Start downloading the decryption tool.
Make sure to launch the decryption utility as an administrator. You need to agree with the license terms that will come up. For this purpose, click on the “Yes” button:
As soon as you accept the license terms, the main decryptor user interface comes up:
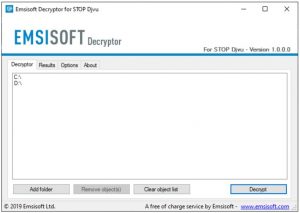
Select folders for decryption.
Based on the default settings, the decryptor will automatically populate the available locations in order to decrypt the currently available drives (the connected ones), including the network drives. Extra (optional) locations can be selected with the help of the “Add” button.
Decryptors normally suggest several options considering the specific malware family. The current possible options are presented in the Options tab and can be activated or deactivated there. You may locate a detailed list of the currently active Options below.
Click on the “Decrypt” button.
As soon as yo add all the desired locations for decryption into the list, click on the “Decrypt” button in order to initiate the decryption procedure.
Note that the main screen may turn you to a status view, letting you know of the active process and the decryption statistics of your data:
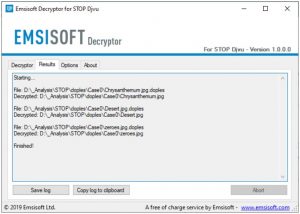
The decryptor will notify you as soon as the decryption procedure is completed. If you need the report for your personal papers, you can save it by choosing the “Save log” button. Note that it is also possible to copy it directly to your clipboard and to paste it into emails or forum messages if you need to do so.
The Emsisoft Decryptor might display different messages after a failed attempt to restore your NOBU files:
✓ Error: Unable to decrypt file with ID: [your ID]
✓ No key for New Variant online ID: [your ID]
Notice: this ID appears to be an online ID, decryption is impossible
✓ Result: No key for new varient offline ID: [example ID]
This ID appears be an offline ID. Decryption may be possible in the future.
It can take a few weeks or months until the decryption key gets found and uploaded to the decryptor. Please follow updates regarding the decryptable DJVU versions here.
✓ Remote name could not be resolved
How to Restore .nobu files?
In some case Nobu ransomware is not doom for your files…
Nobu ransomware encryption mechanism feature is next: it encrypts every file byte-by-byte, then saves a file copy, deleting (and not overriding!) the original file. Hence, the information of the file location on the physical disk is lost, but the original file is not deleted from the physical disk. The cell, or the sector where this file was stored, can still contain this file, but it is not listed by the file system and can be overwritten by data that has been loaded to this disk after the deletion. Hence, it is possible to recover your files using special software.
Recovering your files with PhotoRec
PhotoRec is an open-source program, which is originally created for files recovery from damaged disks, or for files recovery in case if they are deleted. However, as time has gone by, this program got the ability to recover the files of 400 different extensions. Hence, it can be used for data recovery after the ransomware attack
At first, you need to download this app. It is 100% free, but the developer states that there is no guarantee that your files will be recovered. PhotoRec is distributed in a pack with other utility of the same developer – TestDisk. The downloaded archive will have TestDisk name, but don’t worry. PhotoRec files are right inside.
To open PhotoRec, you need to find and open “qphotorec_win.exe” file. No installation is required – this program has all the files it need inside of the archive, hence, you can fit it on your USB drive, and try to help your friend/parents/anyone who was been attacked by DJVU/STOP ransomware.
After the launch, you will see the screen showing you the full list of your disk spaces. However, this information is likely useless, because the required menu is placed a bit higher. Click this bar, then choose the disk which was attacked by ransomware.
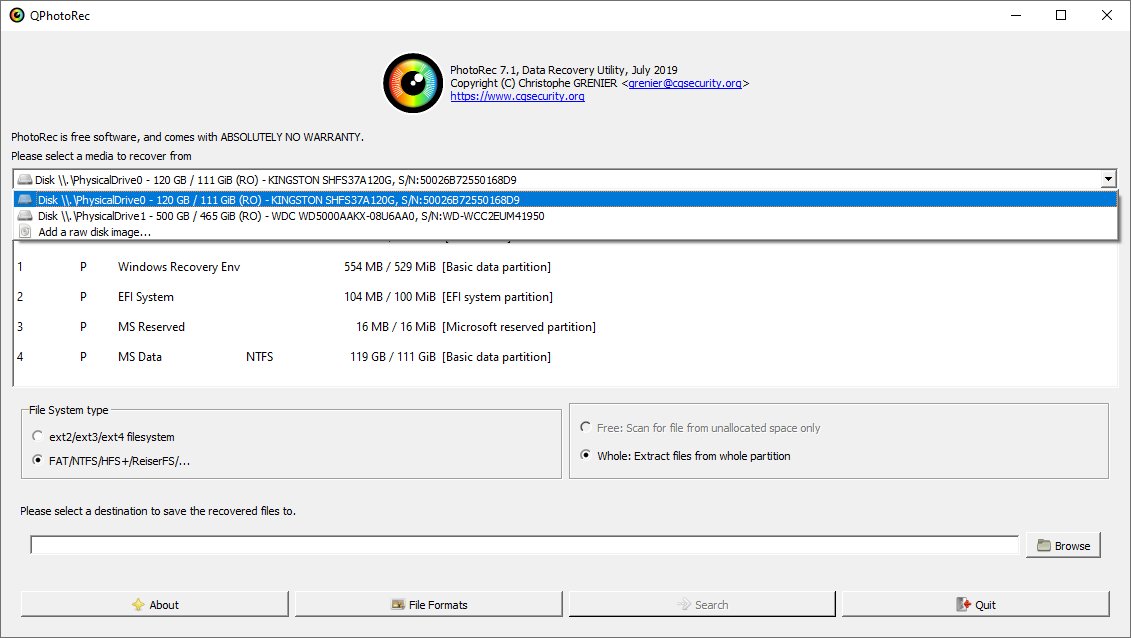
After choosing the disk, you need to choose the destination folder for the recovered files. This menu is located at the lower part of the PhotoRec window. The best desicion is to export them on USB drive or any other type of removable disk.
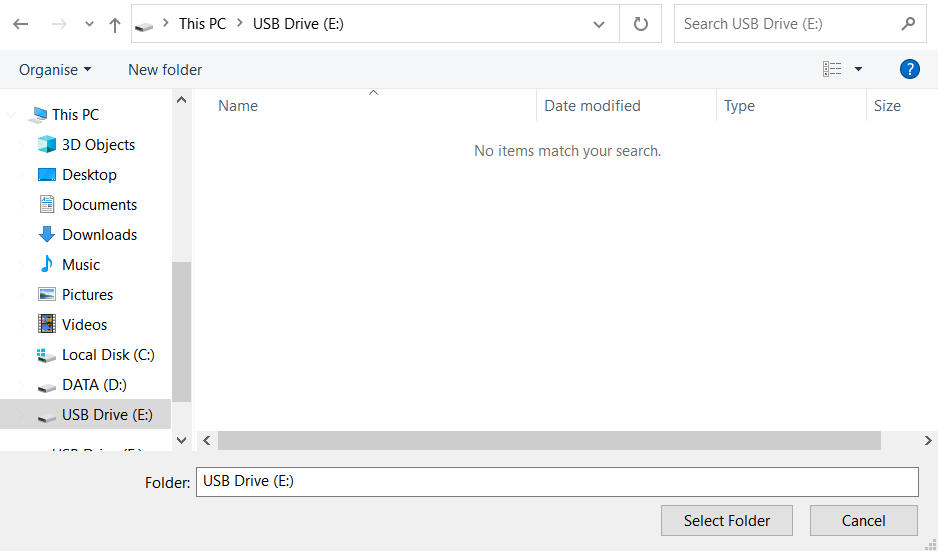
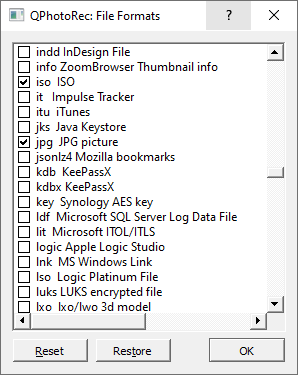
Then, you need to specify the file formats. This option is located at the bottom, too. As it was mentioned, PhotoRec can recover the files of about 400 different formats.
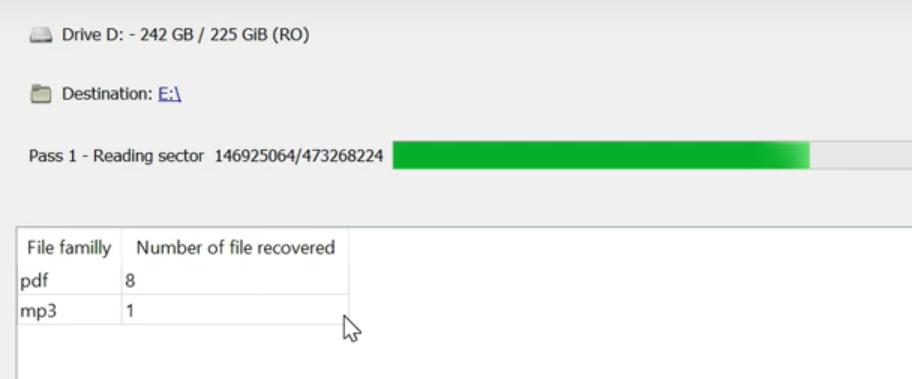
Finally, you can start files recovery by pressing the “Search” button. You will see the screen where the results of the scan and recovery are shown.
NOBU files recovery guide
Frequently Asked Questions
No way. These files are encrypted by Nobu ransomware. The contents of .nobu files are not available until they are decrypted.
If your data remained in the .nobu files are very valuable, then most likely you made a backup copy.
If not, then you can try to restore them through the system function – Restore Point.
All other methods will require patience.
Of course not. Your encrypted files do not pose a threat to the computer. What happened has already happened.
You need GridinSoft Anti-Malware to remove active system infections. The virus that encrypted your files is most likely still active and periodically runs a test for the ability to encrypt even more files. Also, these viruses install keyloggers and backdoors for further malicious actions (for example, theft of passwords, credit cards) often.
In this situation, you need to prepare the memory stick with a pre-installed Trojan Killer.
Have patience. You are infected with the new version of Nobu ransomware, and decryption keys have not yet been released. Follow the news on our website.
We will keep you posted on when new Nobu keys or new decryption programs appear.
The Nobu ransomware encrypts only the first 150KB of files. So MP3 files are rather large, some media players (Winamp for example) may be able to play the files, but – the first 3-5 seconds (the encrypted portion) will be missing.
You can try to find a copy of an original file that was encrypted:
- Files you downloaded from the Internet that were encrypted and you can download again to get the original.
- Pictures that you shared with family and friends that they can just send back to you.
- Photos that you uploaded on social media or cloud services like Carbonite, OneDrive, iDrive, Google Drive, etc)
- Attachments in emails you sent or received and saved.
- Files on an older computer, flash drive, external drive, camera memory card, or iPhone where you transferred data to the infected computer.
Also, you can contact the following government fraud and scam sites to report this attack:
- In the United States: On Guard Online;
- In Canada: Canadian Anti-Fraud Centre;
- In the United Kingdom: Action Fraud;
- In Australia: SCAMwatch;
- In New Zealand: Consumer Affairs Scams;
- In India, go to Indian National Cybercrime Reporting Portal.
- In France: Agence nationale de la sécurité des systèmes d’information;
- In Germany: Bundesamt für Sicherheit in der Informationstechnik;
- In Ireland: An Garda Síochána;
To report the attack, you can contact local executive boards. For instance, if you live in USA, you can have a talk with FBI Local field office, IC3 or Secret Service.
Video Guide
It’s my favorite video tutorial: How to use GridinSoft Anti-Malware and Emsisoft Decryptor for fix ransomware infections.
If the guide doesn’t help you to remove Nobu infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help.
I need your help to share this article.
It is your turn to help other people. I have written this article to help users like you. You can use buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Brendan SmithHow to Remove NOBU Ransomware & Recover PC

Name: NOBU Virus
Description: NOBU Virus is a DJVU family of ransomware-type infections. This infection encrypts important personal files (video, photos, documents). The encrypted files can be tracked by a specific .nobu extension. So, you can't use them at all.
Operating System: Windows
Application Category: Virus
User Review
( votes)References
- Ransomware-type infection: https://en.wikipedia.org/wiki/Ransomware
- Twitter: https://twitter.com/demonslay335
- My files are encrypted by ransomware, what should I do now?
- About DJVU (STOP) Ransomware.
- Windows passwords vulnerability (Mimikatz HackTool): https://howtofix.guide/mimikatz-hacktool/
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison
- Trojan Killer Review: https://howtofix.guide/trojan-killer/
![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean


please help my pc yesterday was just hit by the NOBU ransomware virus. sari yesterday until now I am still confused about how to return it. I was looking there and there still didn’t get the solution,
very pity because a lot of important data on my pc
I tried your way but when i install the descryptor it was error’ so i cannot go to next step , and i tried to use restore point in windows but all my file in other partition there is still .Nobu virus